Thanks andesu and everyone.
Now I can browse internet!!!!!
This is my setup for years.
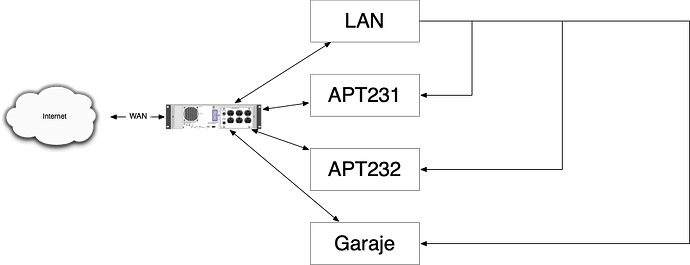
The main router is a quad core i5 with 8GB of RAM, 256GB of SSD and 6 network cards.
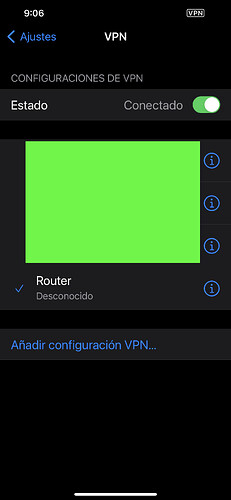
I only want the VPN to be able to connect from my phone or a laptop to perform basic management tasks on time.
I currently have a Raspberry PI dedicated as an ipsec/l2tp server. It works fine, but I want to remove stuff and have all network services in one place.
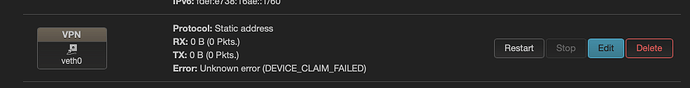
But I can't access the LAN or any other zone. DNS seems to be the only thing that works.
I have followed all instructions and advice. I've tried playing with the VPN zone on the firewall, but I can't get it to work.
I have also tried it with the network settings.
- bridge br-vpn
- VLAN 30 - eth0.30 (eth0 is the lan). My ISP use VLAN 20 on WAN.
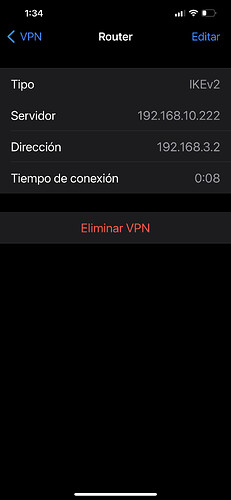
I can ping any address. 8.8.8.8, www.google.com, 192.168.2.1 (LAN), 192.168.10.220(WAN), 192.168.3.1 (br-vpn), but I can't ping a PC connected on the LAN (192.168.2.100) .
I think I'm close, but I can't find the problem.
I am currently doing the tests with a computer connected to my lan to make the connection. It's a mini lab. The WAN of the lab is in the LAN of my actual network.
If we get it working, I promise to make a detailed step by step tutorial.
Thanks a lot.
Setup
opkg update
opkg install strongswan-full kmod-crypto-gcm openssl-util iptables-nft
/etc/init.d/ipsec stop
/etc/init.d/ipsec disable
mv /etc/ipsec.conf /etc/ipsec.conf.old
mv /etc/ipsec.secrets /etc/ipsec.secrets.old
mv /etc/ipsec.user /etc/ipsec.user.old
mv /etc/ipsec.d /etc/ipsec.d.old
/etc/init.d/swanctl enable
/etc/init.d/swanctl start
/etc/nftables.d/20-ipsec.nft
chain ipsec_chain {
type nat hook postrouting priority -1;
ip daddr 192.168.3.0/28 counter accept
}
chain forward {
type filter hook forward priority 0;
ip saddr 192.168.3.0/28 counter drop
}
By the way, it is very important to leave at least one blank line at the end of the file "/etc/nftables.d/20-ipsec.nft". If it is not left it gives the meta error...
/dev/stdin:105:3-6: Error: syntax error, unexpected meta, expecting newline or semicolon
meta nfproto ipv4 udp dport 68 counter accept comment "!fw4: Allow-DHCP-Renew"
^^^^
/dev/stdin:125:3-6: Error: syntax error, unexpected meta, expecting newline or semicolon
meta nfproto ipv6 icmpv6 type { 128, 129, 1, 3 } limit rate 1000/second counter accept comment "!fw4: Allow-ICMPv6-Forward"
^^^^
The rendered ruleset contains errors, not doing firewall restart.
/etc/swamctl/common.conf
local_addrs = 0.0.0.0/0,::/0
remote_addrs = 0.0.0.0/0,::/0
local {
auth = pubkey
certs = serverCert_vpn.molvizar.net.pem
id = vpn.molvizar.net
}
children {
ikev2clients {
local_ts = 192.168.3.0/28, 192.168.2.0/24
esp_proposals = default
}
}
pools = strongswanippool
unique = never
version = 2
proposals = default
/etc/strongswan.d/attr.conf
# Section to specify arbitrary attributes that are assigned to a peer via
# configuration payload (CP).
attr {
# <attr> is an attribute name or an integer, values can be an IP address,
# subnet or arbitrary value.
# <attr> =
# Whether to load the plugin. Can also be an integer to increase the
# priority of this plugin.
3 = 192.168.3.1
25 = lan
load = yes
}
/etc/strongswan.conf
# strongswan.conf - strongSwan configuration file
#
# Refer to the strongswan.conf(5) manpage for details
#
# Configuration changes should be made in the included files
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
}
start-scripts {
load-all = /usr/sbin/swanctl --load-all
}
}
include strongswan.d/*.conf
# include /var/ipsec/strongswan.conf
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list masq_dest '!192.168.3.0/28'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule 'ipsec_esp'
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
config rule 'ipsec_ike'
option name 'Allow-ISAKMP'
option src 'wan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule 'ipsec_nat_traversal'
option src 'wan'
option name 'Allow-IPSec-NAT-T'
option proto 'udp'
option dest_port '4500'
option target 'ACCEPT'
config rule 'ipsec_auth_header'
option src 'wan'
option name 'Allow-Auth-Header'
option proto 'ah'
option target 'ACCEPT'
config zone
option name 'apt231'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'apt231'
config zone
option name 'apt232'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'apt232'
config zone
option name 'garaje'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'garaje'
config forwarding
option src 'lan'
option dest 'apt231'
config forwarding
option src 'lan'
option dest 'apt232'
config forwarding
option src 'lan'
option dest 'garaje'
config forwarding
option src 'apt231'
option dest 'wan'
config forwarding
option src 'apt232'
option dest 'wan'
config forwarding
option src 'garaje'
option dest 'wan'
config rule
option name 'AllowIPsec2WAN'
list proto 'all'
option src 'wan'
option dest 'wan'
option target 'ACCEPT'
config include
option type 'nftables'
option path '/etc/fwuser.nft'
option position 'chain-pre'
option chain 'input_wan'
config include
option type 'nftables'
option path '/etc/fwuser.nft'
option position 'chain-pre'
option chain 'forward_wan'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'vpn'
option forward 'ACCEPT'
option masq '1'
/etc/fwuser.nft
meta ipsec exists ip saddr 192.168.3.0/28 counter accept comment "custom: allow for vpn"
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fded:05b9:85cc::/48'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'eth0'
option ipaddr '192.168.2.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option name 'eth0'
config device
option name 'eth1'
option ipv6 '0'
config interface 'apt231'
option proto 'static'
option device 'eth2'
option ipaddr '192.168.231.1'
option netmask '255.255.255.240'
list dns '1.1.1.3'
list dns '1.0.0.3'
config interface 'apt232'
option proto 'static'
option ipaddr '192.168.232.1'
option netmask '255.255.255.240'
list dns '1.1.1.3'
list dns '1.0.0.3'
option device 'eth4'
config interface 'garaje'
option proto 'static'
option ipaddr '192.168.200.1'
option netmask '255.255.255.240'
list dns '1.1.1.3'
list dns '1.0.0.3'
option device 'eth3'
config device
option name 'eth5'
option ipv6 '0'
config device
option name 'eth2'
option ipv6 '0'
config device
option name 'eth3'
option ipv6 '0'
config device
option name 'eth4'
option ipv6 '0'
config device
option type '8021q'
option ifname 'eth0'
option vid '30'
option name 'eth0.30'
option ipv6 '0'
config interface 'vpn'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.240'
list dns '1.1.1.3'
list dns '1.0.0.3'
option device 'eth0.30'
nft monitor trace
trace id c527376c inet fw4 trace_chain packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 trace_chain rule udp dport 53 meta nftrace set 1 (verdict continue)
trace id c527376c inet fw4 trace_chain verdict continue
trace id c527376c inet fw4 trace_chain policy accept
trace id c527376c inet fw4 raw_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 raw_prerouting verdict continue
trace id c527376c inet fw4 raw_prerouting policy accept
trace id c527376c inet fw4 mangle_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 mangle_prerouting verdict continue
trace id c527376c inet fw4 mangle_prerouting policy accept
trace id c527376c inet fw4 prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 prerouting verdict continue
trace id c527376c inet fw4 prerouting policy accept
trace id c527376c inet fw4 mangle_input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 mangle_input verdict continue
trace id c527376c inet fw4 mangle_input policy accept
trace id c527376c inet fw4 input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54991 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x36eb01200001000000000000
trace id c527376c inet fw4 input rule iifname "lo" accept comment "!fw4: Accept traffic from loopback" (verdict accept)
trace id c02cef77 inet fw4 trace_chain packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 trace_chain rule udp dport 53 meta nftrace set 1 (verdict continue)
trace id c02cef77 inet fw4 trace_chain verdict continue
trace id c02cef77 inet fw4 trace_chain policy accept
trace id c02cef77 inet fw4 raw_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 raw_prerouting verdict continue
trace id c02cef77 inet fw4 raw_prerouting policy accept
trace id c02cef77 inet fw4 mangle_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 mangle_prerouting verdict continue
trace id c02cef77 inet fw4 mangle_prerouting policy accept
trace id c02cef77 inet fw4 prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 prerouting verdict continue
trace id c02cef77 inet fw4 prerouting policy accept
trace id c02cef77 inet fw4 mangle_input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 mangle_input verdict continue
trace id c02cef77 inet fw4 mangle_input policy accept
trace id c02cef77 inet fw4 input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54992 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xa1bb01200001000000000000
trace id c02cef77 inet fw4 input rule iifname "lo" accept comment "!fw4: Accept traffic from loopback" (verdict accept)
trace id c7a2e3aa inet fw4 trace_chain packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 trace_chain rule udp dport 53 meta nftrace set 1 (verdict continue)
trace id c7a2e3aa inet fw4 trace_chain verdict continue
trace id c7a2e3aa inet fw4 trace_chain policy accept
trace id c7a2e3aa inet fw4 raw_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 raw_prerouting verdict continue
trace id c7a2e3aa inet fw4 raw_prerouting policy accept
trace id c7a2e3aa inet fw4 mangle_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 mangle_prerouting verdict continue
trace id c7a2e3aa inet fw4 mangle_prerouting policy accept
trace id c7a2e3aa inet fw4 prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 prerouting verdict continue
trace id c7a2e3aa inet fw4 prerouting policy accept
trace id c7a2e3aa inet fw4 mangle_input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 mangle_input verdict continue
trace id c7a2e3aa inet fw4 mangle_input policy accept
trace id c7a2e3aa inet fw4 input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54993 ip protocol udp ip length 72 udp sport 38161 udp dport 53 udp length 52 @th,64,96 0x6ef01200001000000000000
trace id c7a2e3aa inet fw4 input rule iifname "lo" accept comment "!fw4: Accept traffic from loopback" (verdict accept)
trace id 867d5365 inet fw4 trace_chain packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 trace_chain rule udp dport 53 meta nftrace set 1 (verdict continue)
trace id 867d5365 inet fw4 trace_chain verdict continue
trace id 867d5365 inet fw4 trace_chain policy accept
trace id 867d5365 inet fw4 raw_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 raw_prerouting verdict continue
trace id 867d5365 inet fw4 raw_prerouting policy accept
trace id 867d5365 inet fw4 mangle_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 mangle_prerouting verdict continue
trace id 867d5365 inet fw4 mangle_prerouting policy accept
trace id 867d5365 inet fw4 prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 prerouting verdict continue
trace id 867d5365 inet fw4 prerouting policy accept
trace id 867d5365 inet fw4 mangle_input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 mangle_input verdict continue
trace id 867d5365 inet fw4 mangle_input policy accept
trace id 867d5365 inet fw4 input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54994 ip protocol udp ip length 73 udp sport 38161 udp dport 53 udp length 53 @th,64,96 0x618b01200001000000000000
trace id 867d5365 inet fw4 input rule iifname "lo" accept comment "!fw4: Accept traffic from loopback" (verdict accept)
trace id d4238eac inet fw4 trace_chain packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 trace_chain rule udp dport 53 meta nftrace set 1 (verdict continue)
trace id d4238eac inet fw4 trace_chain verdict continue
trace id d4238eac inet fw4 trace_chain policy accept
trace id d4238eac inet fw4 raw_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 raw_prerouting verdict continue
trace id d4238eac inet fw4 raw_prerouting policy accept
trace id d4238eac inet fw4 mangle_prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 mangle_prerouting verdict continue
trace id d4238eac inet fw4 mangle_prerouting policy accept
trace id d4238eac inet fw4 prerouting packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 prerouting verdict continue
trace id d4238eac inet fw4 prerouting policy accept
trace id d4238eac inet fw4 mangle_input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 mangle_input verdict continue
trace id d4238eac inet fw4 mangle_input policy accept
trace id d4238eac inet fw4 input packet: iif "lo" @ll,0,112 0x800 ip saddr 127.0.0.1 ip daddr 127.0.0.1 ip dscp cs0 ip ecn not-ect ip ttl 64 ip id 54995 ip protocol udp ip length 71 udp sport 38161 udp dport 53 udp length 51 @th,64,96 0xba2501200001000000000000
trace id d4238eac inet fw4 input rule iifname "lo" accept comment "!fw4: Accept traffic from loopback" (verdict accept)
swanctl --log
08[NET] received packet: from 192.168.10.75[500] to 192.168.10.220[500] (604 bytes)
08[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
08[IKE] 192.168.10.75 is initiating an IKE_SA
08[CFG] selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
08[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(CHDLESS_SUP) N(MULT_AUTH) ]
08[NET] sending packet: from 192.168.10.220[500] to 192.168.10.75[500] (456 bytes)
06[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (512 bytes)
06[ENC] unknown attribute type INTERNAL_DNS_DOMAIN
06[ENC] parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr CPRQ(ADDR MASK DHCP DNS ADDR6 DHCP6 DNS6 DOMAIN) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(MOBIKE_SUP) ]
06[CFG] looking for peer configs matching 192.168.10.220[vpn.molvizar.net]...192.168.10.75[SolaresVPN]
06[CFG] selected peer config 'rw-eaptlsios'
06[IKE] initiating EAP_TLS method (id 0x0B)
06[IKE] received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
06[IKE] peer supports MOBIKE
06[IKE] authentication of 'vpn.molvizar.net' (myself) with RSA signature successful
06[IKE] sending end entity cert "C=ES, O=Molvizar, CN=vpn.molvizar.net"
06[ENC] generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/TLS ]
06[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (1232 bytes)
12[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (240 bytes)
12[ENC] parsed IKE_AUTH request 2 [ EAP/RES/TLS ]
12[TLS] using key of type RSA
12[TLS] negotiated TLS 1.2 using suite TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
12[TLS] sending TLS server certificate 'C=ES, O=Molvizar, CN=vpn.molvizar.net'
12[TLS] sending TLS cert request for 'C=ES, O=Molvizar, CN=Molvizar'
12[ENC] generating IKE_AUTH response 2 [ EAP/REQ/TLS ]
12[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (1104 bytes)
10[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (80 bytes)
10[ENC] parsed IKE_AUTH request 3 [ EAP/RES/TLS ]
10[ENC] generating IKE_AUTH response 3 [ EAP/REQ/TLS ]
10[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (448 bytes)
16[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (532 bytes)
16[ENC] parsed IKE_AUTH request 4 [ EF(1/3) ]
16[ENC] received fragment #1 of 3, waiting for complete IKE message
05[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (532 bytes)
05[ENC] parsed IKE_AUTH request 4 [ EF(2/3) ]
05[ENC] received fragment #2 of 3, waiting for complete IKE message
12[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (180 bytes)
12[ENC] parsed IKE_AUTH request 4 [ EF(3/3) ]
12[ENC] received fragment #3 of 3, reassembled fragmented IKE message (1104 bytes)
12[ENC] parsed IKE_AUTH request 4 [ EAP/RES/TLS ]
12[ENC] generating IKE_AUTH response 4 [ EAP/REQ/TLS ]
12[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (80 bytes)
15[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (532 bytes)
15[ENC] parsed IKE_AUTH request 5 [ EF(1/3) ]
15[ENC] received fragment #1 of 3, waiting for complete IKE message
05[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (532 bytes)
05[ENC] parsed IKE_AUTH request 5 [ EF(2/3) ]
05[ENC] received fragment #2 of 3, waiting for complete IKE message
04[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (180 bytes)
04[ENC] parsed IKE_AUTH request 5 [ EF(3/3) ]
04[ENC] received fragment #3 of 3, reassembled fragmented IKE message (1104 bytes)
04[ENC] parsed IKE_AUTH request 5 [ EAP/RES/TLS ]
04[TLS] received TLS peer certificate 'C=ES, O=Molvizar, CN=SolaresVPN'
04[TLS] received TLS intermediate certificate 'C=ES, O=Molvizar, CN=Molvizar'
04[CFG] using trusted ca certificate "C=ES, O=Molvizar, CN=Molvizar"
04[CFG] checking certificate status of "C=ES, O=Molvizar, CN=SolaresVPN"
04[CFG] certificate status is not available
04[CFG] reached self-signed root ca with a path length of 0
04[CFG] using trusted certificate "C=ES, O=Molvizar, CN=SolaresVPN"
04[ENC] generating IKE_AUTH response 5 [ EAP/REQ/TLS ]
04[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (80 bytes)
16[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (128 bytes)
16[ENC] parsed IKE_AUTH request 6 [ EAP/RES/TLS ]
16[ENC] generating IKE_AUTH response 6 [ EAP/REQ/TLS ]
16[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (144 bytes)
09[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (80 bytes)
09[ENC] parsed IKE_AUTH request 7 [ EAP/RES/TLS ]
09[IKE] EAP method EAP_TLS succeeded, MSK established
09[ENC] generating IKE_AUTH response 7 [ EAP/SUCC ]
09[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (80 bytes)
05[NET] received packet: from 192.168.10.75[4500] to 192.168.10.220[4500] (112 bytes)
05[ENC] parsed IKE_AUTH request 8 [ AUTH ]
05[IKE] authentication of 'SolaresVPN' with EAP successful
05[IKE] authentication of 'vpn.molvizar.net' (myself) with EAP
05[IKE] IKE_SA rw-eaptlsios[29] established between 192.168.10.220[vpn.molvizar.net]...192.168.10.75[SolaresVPN]
05[IKE] scheduling rekeying in 13929s
05[IKE] maximum IKE_SA lifetime 15369s
05[IKE] peer requested virtual IP %any
05[CFG] reassigning offline lease to 'SolaresVPN'
05[IKE] assigning virtual IP 192.168.3.2 to peer 'SolaresVPN'
05[IKE] peer requested virtual IP %any6
05[IKE] no virtual IP found for %any6 requested by 'SolaresVPN'
05[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
05[IKE] CHILD_SA ikev2clients{8} established with SPIs ced3c30e_i 048ab218_o and TS 192.168.2.0/24 192.168.3.0/28 === 192.168.3.2/32
05[ENC] generating IKE_AUTH response 8 [ AUTH CPRP(ADDR DNS DOMAIN DNS) SA TSi TSr N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_6_ADDR) ]
05[NET] sending packet: from 192.168.10.220[4500] to 192.168.10.75[4500] (352 bytes)