Hello all,
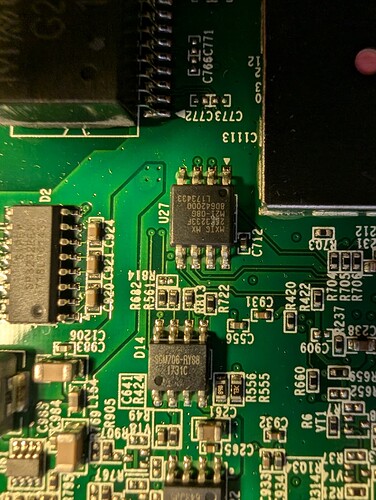
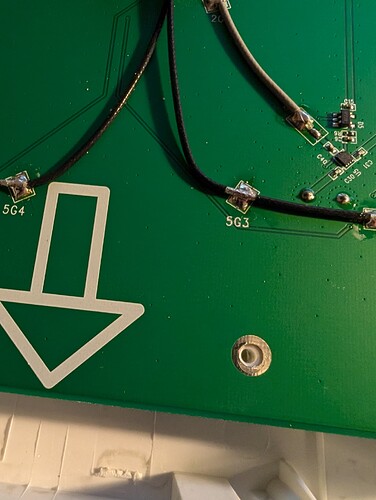
I recently looked at von Rosenberg's excellent commit for the Huawei AP5030DN, and was impressed with how relatively smooth the process was for enterprise equipment. I was wondering if it would be viable to port OpenWRT to Huawei devices using the newer ARM-based IPQx SoCs via the same TFTP interface, and recently had the opportunity to buy an AP7050DE for fairly cheap. The board inside the device appears very similar to the AP6050 Ver. A. , but with a larger RAM capacity and a different antenna. Here are some external pictures:
I appended the tty bootlog below. I know that one thing to watch out for with IPQ8068 is secure boot, but I don't see any indications of it being utilised in the bootlog. Is there a good way to non-destructively find out whether secureboot or worse yet hardware fuses are present?
I'm trying to figure out what to do next. Should I just flash stock openwrt and see if I am held back by the same 1.6s watchdog and PHY suspension, that von Rosenberg was with the AP5030DN, trial and error?
Thank you very much for all your input!
Bootlog:
Welcome To HUAWEI Wlan World
U-Boot 628 (Jul 29 2020 - 18:23:32)
DRAM: 512 MB
NAND: 128 MB
NOR: 4 MB
Board Type: 0x105
BOOT: Primary
USB0: USB XHCI 1.00
USB1: USB XHCI 1.00
0 Storage Device(s) found
PCI0 Link Intialized
PCI1 Link Intialized
Press CTRL+T for Full Memory Test in 1 Seconds: 1 0
Net: Ethernet Mac: <redacted>
eth0, eth1
Start Up time(s) : 1
POST test: Begin
Testing GE_0 : Passed.
Testing GE_1 : Passed.
Testing PCIE1 : Passed.
Testing PCIE2 : Passed.
Testing DDR : Passed.
Testing Nor Flash: Passed.
Testing Nand Flash: Passed.
Saving POST results: Done
POST test: End
Image: Current Bootup is B
Press f or F to stop Auto-Boot in 3 seconds: 3 2 1 0
No need to update from sys-boot!
Image Name: Linux Kernel Image
Image Type: ARM Linux Kernel Image (lzma compressed)
Data Size: 2662871 Bytes = 2.5 MB
Load Address: 41508000
Entry Point: 41508000
Verifying Checksum ... dcrc 0xfd39bea, image_get_dcrc 0xfd39bea
OK
Uncompressing Kernel Image ... OK
Linux version 3.10.62-ltsi-WR6.0.0.21_standard (root@100.109.231.145) (gcc version 4.8.1 (GCC) ) #1 SMP PREEMPT Wed Jul 29 18:25:04 CST 2020
CPU: ARMv7 Processor [512f04d0] revision 0 (ARMv7), cr=10c5387d
CPU: PIPT / VIPT nonaliasing data cache, PIPT instruction cache
Machine: Qualcomm Atheros AP7050DE reference board
msm_reserve_memory: 0x44000000, 0x100000
msm_reserve_memory: 0x44800000, 0x400000
Memory policy: ECC disabled, Data cache writealloc
smem_find(137, 80): wrong size 72
Built 1 zonelists in Zone order, mobility grouping on. Total pages: 123178
Kernel command line: console=ttyHSL1,9600n8 norootfssplit ubi.mtd=RWFS rootautoubi=10 root=/dev/mtdblock34 ro rootfstype=squashfs rdinit=/sbin/init
FWD_MEM: aligned address c6b00000
FWD_MEM: 48000000
FWD_MEM: Allocating 128MB (32768 pages) of memory at addr c6b00000
Memory: 351768k/357912k available, 144872k reserved, 0K highmem
Virtual kernel memory layout:
vector : 0xffff0000 - 0xffff1000 ( 4 kB)
fixmap : 0xffc00000 - 0xfff00000 (3072 kB)
vmalloc : 0xdf000000 - 0xff000000 ( 512 MB)
lowmem : 0xc0000000 - 0xdeb00000 ( 491 MB)
pkmap : 0xbfe00000 - 0xc0000000 ( 2 MB)
modules : 0xbf000000 - 0xbfe00000 ( 14 MB)
.text : 0xc0008000 - 0xc0721a3c (7271 kB)
.init : 0xc0722000 - 0xc0756e00 ( 212 kB)
.data : 0xc0758000 - 0xc080acc0 ( 716 kB)
.bss : 0xc080acc0 - 0xc08f8834 ( 951 kB)
CPU1: Booted secondary processor
AXI: msm_bus_fabric_init_driver(): msm_bus_fabric_init_driver
smem_find(137, 80): wrong size 72
clk_tbl_nss - loaded
msm_pcie_setup: no link initialization
PCI: enabling device 0000:02:00.0 (0140 -> 0143)
PCI: enabling device 0000:00:00.0 (0140 -> 0143)
SCSI subsystem initialized
smd: no register irq on wcnss_a11
smd: deregistering IRQs
SMD: smd_core_platform_init() not ok
get_bootconfig_partition: magic not found
msm_rpm_log_probe: OK
Creating 15 MTD partitions on "msm_nand":
0x000000000000-0x000000040000 : "SBL1"
0x000000040000-0x000000180000 : "MIBIB"
0x000000180000-0x0000002c0000 : "SBL2"
0x0000002c0000-0x000000540000 : "SBL3"
0x000000540000-0x000000660000 : "DDRCONFIG"
0x000000660000-0x000000780000 : "SSD"
0x000000780000-0x000000a00000 : "TZ"
0x000000a00000-0x000000c80000 : "RPM"
0x000000c80000-0x000001400000 : "APPSBL"
0x000001400000-0x000002e00000 : "ROOTFSA"
0x000002e00000-0x000004800000 : "ROOTFSB"
0x000004800000-0x000005000000 : "KERNELA"
0x000005000000-0x000005800000 : "KERNELB"
0x000005800000-0x000006c00000 : "RWFS"
0x000006c00000-0x000008000000 : "EMT"
m25p80 spi5.0: found mx25l3205d, expected s25fl512s
Creating 18 MTD partitions on "m25p80":
0x000000000000-0x000000010000 : "SBL1"
0x000000010000-0x000000030000 : "MIBIB"
0x000000030000-0x000000050000 : "SBL2"
0x000000050000-0x000000080000 : "SBL3"
0x000000080000-0x000000090000 : "DDRCONFIG"
0x000000090000-0x0000000a0000 : "SSD"
0x0000000a0000-0x0000000d0000 : "TZ"
0x0000000d0000-0x0000000f0000 : "RPM"
0x0000000f0000-0x0000001f0000 : "APPSBL"
0x0000001f0000-0x000000200000 : "APPSBLENV"
0x000000200000-0x000000220000 : "ICT"
0x000000220000-0x000000240000 : "BoardData"
0x000000240000-0x000000260000 : "BoardData-B"
0x000000260000-0x0000002c0000 : "ResultA"
0x0000002c0000-0x000000320000 : "ResultB"
0x000000320000-0x000000340000 : "ArtArgs"
0x000000340000-0x000000400000 : "Rsv"
0x000000000000-0x0000001f0000 : "NORBOOT"
ipq-dwc3 ipq-dwc3.0: unable to read platform data num of dbm eps
ipq-dwc3 ipq-dwc3.1: unable to read platform data num of dbm eps
unable to find transceiver of type USB2 PHY
msm_hsusb_host msm_hsusb_host: unable to find transceiver
Registering SWP/SWPB emulation handler
ipq_nss_get_mac_addr: MAC[0]: ff:ff:ff:ff:ff:ff
ipq_nss_get_mac_addr: MAC[1]: ff:ff:ff:ff:ff:ff
ipq_nss_get_mac_addr: MAC[2]: ff:ff:ff:ff:ff:ff
ipq_nss_get_mac_addr: MAC[3]: ff:ff:ff:ff:ff:ff
no pmic restart interrupt specified
UBI: attaching mtd13 to ubi0
UBI: scanning is finished
UBI: attached mtd13 (name "RWFS", size 20 MiB) to ubi0
UBI: PEB size: 131072 bytes (128 KiB), LEB size: 126976 bytes
UBI: min./max. I/O unit sizes: 2048/2048, sub-page size 2048
UBI: VID header offset: 2048 (aligned 2048), data offset: 4096
UBI: good PEBs: 160, bad PEBs: 0, corrupted PEBs: 0
UBI: user volume: 1, internal volumes: 1, max. volumes count: 128
UBI: max/mean erase counter: 1630/1344, WL threshold: 4096, image sequence number: 871908348
UBI: available PEBs: 0, total reserved PEBs: 160, PEBs reserved for bad PEB handling: 20
UBI: attaching mtd10 to ubi1
UBI: scanning is finished
UBI: attached mtd10 (name "ROOTFSB", size 26 MiB) to ubi1
UBI: PEB size: 131072 bytes (128 KiB), LEB size: 126976 bytes
UBI: min./max. I/O unit sizes: 2048/2048, sub-page size 2048
UBI: VID header offset: 2048 (aligned 2048), data offset: 4096
UBI: good PEBs: 208, bad PEBs: 0, corrupted PEBs: 0
UBI: user volume: 1, internal volumes: 1, max. volumes count: 128
UBI: max/mean erase counter: 1/0, WL threshold: 4096, image sequence number: 331879724
UBI: available PEBs: 42, total reserved PEBs: 166, PEBs reserved for bad PEB handling: 20
attach mtd10 return ubi1
Bad inittab entry at line 10
Bad inittab entry at line 11
starting pid 109, tty '': '-/etc/init.d/rcS'
hello
ksecure: module license 'unspecified' taints kernel.
Disabling lock debugging due to kernel taint
MIMC_KERNEL: Module init.
Insmod bsp_adapter
Insmod cryptodev
Insmod I2C
Insmod GPIO
Initializing arch flag Done.
starting thermald...
read content=/modules/3.10.62/net/wifi_module.ko,len=36.
Insmod broadcom
######## 32Bit Kernel ##########
######## MSS Memory Device register success ########
**********************************************************
* Driver :NSS GMAC Driver for RTL v(3.72a)
* Version :1.0
* Copyright :Copyright (c) 2013-2014 The Linux Foundation. All rights reserved.
**********************************************************done.
read content=/modules/3.10.62/net/umac.ko,len=29.
done.
read content=/root/cap32,len=12.
done.
read content=/modules/msu.ko,len=16.
done.
read content=/root/vos.o,len=12.
UBIFS: background thread "ubifs_bgt0_0" started, PID 148
UBIFS: recovery needed
UBIFS: recovery completed
UBIFS: mounted UBI device 0, volume 0, name "RWFS"
UBIFS: LEB size: 126976 bytes (124 KiB), min./max. I/O unit sizes: 2048 bytes/2048 bytes
UBIFS: FS size: 15998976 bytes (15 MiB, 126 LEBs), journal size 2920448 bytes (2 MiB, 23 LEBs)
UBIFS: reserved for root: 0 bytes (0 KiB)
UBIFS: media format: w4/r0 (latest is w4/r0), UUID 4B10169E-E57E-41D5-8A97-822BA10BC03E, small LPT model
mount RWFS successfully
get path free Disk 1628
get path free size enough!
Insmod ipq eth module OK.
Drv_ap_api module:Init
Get the HighMem address is 0xe1800000
mtd30
Wifi Load AP7050DE freq
AP7050DE load default caldata
377+0 records in
377+0 records out
12064 bytes (11.8KB) copied, 0.059075 seconds, 199.4KB/s
377+0 records in
377+0 records out
12064 bytes (11.8KB) copied, 0.038175 seconds, 308.6KB/s
377+0 records in
377+0 records out
12064 bytes (11.8KB) copied, 0.044611 seconds, 264.1KB/s
coset ulMcThValue: 512
py ap7050de boarddata file to /lib/firmware
11ac wave2 Target Bin or Patch Selecting
0:Uninstall Target Patch Sucess!
wifi start ko path ./modules/3.10.62/net
__ol_ath_attach() Allocated scn d87004c0
Atheros Attach: dev name wifi1, radio id: 1
Chip id: 0xa, chip version: 0x1000000
Target Version is 1000000
ol_transfer_bin_file: flash data file defined
ol_transfer_bin_file[3888] Get Caldata for wifi1.
ol_transfer_bin_file 3963: Download Flash data len 12064
Board data initialized
ol_ath_download_firmware:##Board Id 1 , CHIP Id 0
ol_transfer_bin_file: Board Data File download to address=0xc0000 file name=QCA9984/hw.1/boardData_QCA9984_CUS239_5G_v1_001.bin
ol_transfer_bin_file: Downloading firmware file: QCA9984/hw.1/athwlan.bin
+HWT
-HWT
Firmware_Build_Number:74
ol_ath_thermal_mitigation_attach: --
###############Load radio 1
wifi1 Attach success
###############Radio[1] enter cs thread
__ol_ath_attach() Allocated scn d88804c0
Atheros Attach: dev name wifi0, radio id: 0
Chip id: 0xa, chip version: 0x1000000
Target Version is 1000000
ol_transfer_bin_file: flash data file defined
ol_transfer_bin_file[3888] Get Caldata for wifi0.
ol_transfer_bin_file 3963: Download Flash data len 12064
Board data initialized
ol_ath_download_firmware:##Board Id 2 , CHIP Id 0
ol_transfer_bin_file: Board Data File download to address=0xc0000 file name=QCA9984/hw.1/boardData_QCA9984_CUS260_2G_v1_002.bin
ol_transfer_bin_file: Downloading firmware file: QCA9984/hw.1/athwlan.bin
+HWT
-HWT
Firmware_Build_Number:74
ol_ath_thermal_mitigation_attach: --
###############Load radio 0
wifi0 Attach success
###############Radio[0] enter cs thread
__sa_init_module
cat: can't open '/proc/rf_switch': No such file or directory
Mount fsimage type: patch
User fs folder : /opt
Loop device : /dev/loop0
Mount folder : /mnt/patch
Wed Jul 29 18:29:30 UTC 2020
find: /mnt/patch/V200R019C00SPC803B728/*/lib: No such file or directory
cap32 start, build time 10:29:21
get security mode sucess, mode 0
Module MEM Init ...MSS_PUB_Init Succ, ret = 0
AP_Board_Cfg Succ, ret = 0
... OK!
Module DIAG Init ...... OK!
Module PBUF Init get security mode sucess, mode 0
Module MEM Init ...... OK!
Module DIAG Init ...... OK!
Module PBUF Init ...... OK!
Module IM Init ...... OK!
Module IIC Init ...... OK!
Module HAL Init ...... OK!
Module Timer Init ...... OK!
Module TIME Init ...... OK!
MSS_Global_Init Succ, ret = 0
...... OK!
Module IM Init ...... OK!
Module MSU Init OK
MSU_Init Succ, ret = 0
IIC Init ...... OK!
Module HAL Init ...... OK!MSS_IM_InstGlobalInit Succ, ret = 0
MSS_Local_Init Succ, ret = 0
Module Timer Init ...... OK!
Module TIME Init ...... OK!
MSS_Global_Init success!
MSC Process run on core [0], PID = [280]
MSC_TCTL_Init Succ! u32Ret = 0
MSC goto scheduler!
done.
read content=/root/cmdtree.bin,len=18.
done.
read content=/root/db.dat,len=13.
done.
read content=/root/infoeng.res,len=18.
done.
VOS_Start ......
PPI_DEV_SysInit begin.
CDEV_InitProduct Success !
DEV_EVT_InitEvtData Success !
PPI_DEV_SysInit End.
......OK
Task GRSA Init......Ok
Press any key to get started