Hi there,
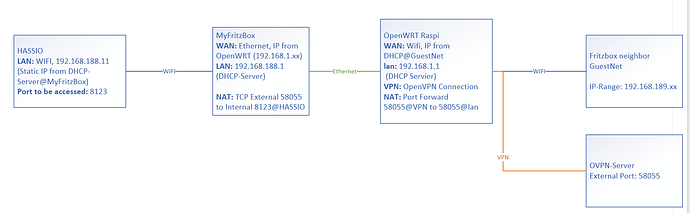
I have a bit of a complicated setup (see Image below) and don't know how to do the port forwarding in OpenWRT properly.
What I want to achieve:
I have a HASSIO server running on an raspi3 and want to access it from outside. I have internet access via my neighbors guest wifi. The problem is, that my neighbor doesn't want to apply port forwarding rules which prevents me from accessing my HASSIO server. I subscribed to OVPN (public VPN service which allows port forwarding from outside to my client) and installed OpenVPN and OpenWRT on another raspberrypi (4), which I set between my own Fritzbox (which manages my own private WIFI) and my neighbors router.
The Problem:
Internet access from inside my private LAN through the VPN tunnel works fine. The problem is, that I cannot access my HASSIO server from outside. Apparently the double NATing (my fritzbox and openwrt) is not set up properly. I can access the HASSIO server via MyFritzBox-WAN IP (192.168.1.xx) but not via either WAN IP of OpenWRT. How do I have to setup the firewall-rules in OpenWRT to get external access?
Thanks very much!
Fabian
firewall-config:
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone
option name 'VPN'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
option masq '1'
option network 'VPN'
config forwarding
option src 'lan'
option dest 'VPN'
config redirect
option target 'DNAT'
option name 'External Port'
list proto 'tcp'
option src 'VPN'
option src_dport '58055'
option dest 'lan'
option dest_ip '192.168.1.247'
network-config:
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd68:ab57:5262::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'dhcp'
option peerdns '0'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'VPN'
option proto 'none'
option ifname 'tun0'