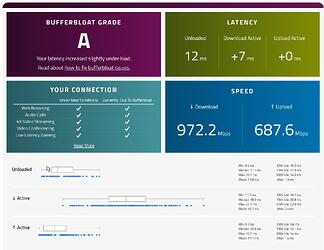
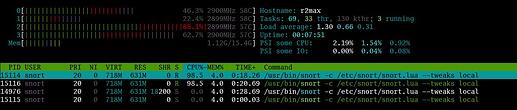
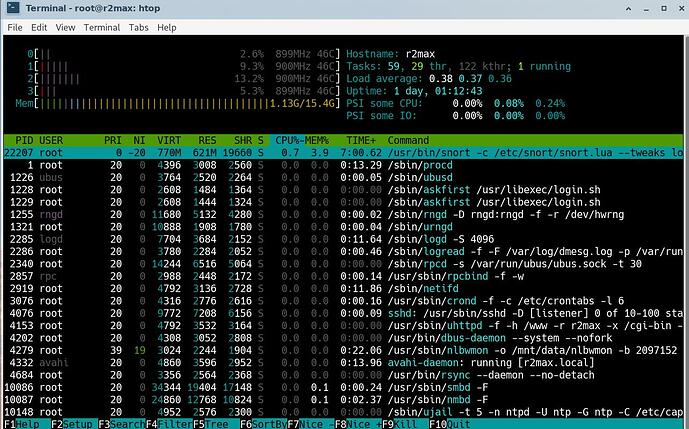
I think the results are too good to be true. Below is my setup, could there be something misconfigured causing traffic to not be fully routed through snort?
In the box, eth0 is LAN facing (to a managed switch) and eth1 is WAN facing.
/etc/config/snort
config snort 'snort'
option config_dir '/etc/snort/'
option interface 'eth1
/etc/init.d/snort
#!/bin/sh /etc/rc.common
START=99
STOP=10
USE_PROCD=1
PROG=/usr/bin/snort
validate_snort_section() {
uci_validate_section snort snort "${1}" \
'config_dir:string' \
'interface:string'
}
start_service() {
local config_file interface
validate_snort_section snort || {
echo "validation failed"
return 1
}
procd_open_instance
procd_set_param env SNORT_LUA_PATH="$config_dir"
procd_set_param command nice -n -20 $PROG -c "${config_dir%/}/snort.lua" --tweaks local
fw4 reload
procd_set_param file $CONFIGFILE
procd_set_param respawn
procd_set_param stdout 1
procd_set_param stderr 1
procd_close_instance
}
stop_service()
{
service_stop ${PROG}
nft delete chain inet fw4 IPS_output
nft delete chain inet fw4 IPS_input
}
service_triggers()
{
procd_add_reload_trigger "snort"
procd_add_validation validate_snort_section
}
/etc/snort/homenet.lua
HOME_NET = [[ 10.9.8.0/24 10.9.7.0/24 10.9.6.0/24 10.9.5.0/24 ]]
EXTERNAL_NET = "!$HOME_NET"
/etc/snort/local.lua
snort = {
['-Q'] = true,
['--max-packet-threads'] = 4,
}
suppress = {
-- this kills stuff in lxc
{
gid = 1, sid = 650, track = 'by_dst', ip = '10.9.8.101'
},
}
network = {
checksum_eval = 'none',
}
daq = {
module_dirs = { '/usr/lib/daq' },
inputs = { '4', '5', '6', '7' },
snaplen = 65531,
modules = {
{
name = 'nfq',
mode = 'inline',
variables = {
'queue_maxlen=8192',
'fail_open',
'device=eth1'
}
}
}
}
ips = {
mode = inline,
variables = default_variables,
action_override = 'drop',
include = RULE_PATH .. '/snort.rules',
}
output.logdir = '/mnt/data'
alert_fast = {
file = true,
packet = false,
}
file_policy = {
enable_type = true,
enable_signature = true,
rules = {
use = {
verdict = 'log', enable_file_type = true, enable_file_signature = true
}
}
}
search_engine = {
search_method = "hyperscan",
offload_search_method ="hyperscan",
detect_raw_tcp = true,
}
detection = {
hyperscan_literals = true,
pcre_to_regex = true,
}
/etc/snort/snort-table.sh
#!/bin/sh
#verbose=false
nft list ruleset | grep -q 'IPS_' && nft delete chain inet fw4 IPS_output && nft delete chain inet fw4 IPS_input
nft -f - <<TABLE
table inet fw4 {
chain IPS_output {
type filter hook postrouting priority 225
policy accept
oifname { $(uci get network.wan.device),wg0 } tcp flags ack ct state established counter accept
oifname $(uci get network.wan.device) udp dport 14500 counter accept
oifname { $(uci get network.wan.device),wg0 } counter queue flags bypass to 4-7
}
chain IPS_input {
type filter hook prerouting priority 300
policy accept
iifname $(uci get network.wan.device) udp sport 14500 ct state established counter accept
iifname { $(uci get network.wan.device),wg0 } counter queue flags bypass to 4-7
}
}
TABLE
#$verbose
exit 0
And at the end of /etc/config/firewall I have:
config include
option enabled '1'
option type 'script'
option path '/etc/snort/snort-table.sh'
option fw4_compatible '1'
For reference starting snort manually without the init.d script give this output:
snort.log
# snort -c /etc/snort/snort.lua --tweaks local
--------------------------------------------------
o")~ Snort++ 3.9.1.0
--------------------------------------------------
Loading /etc/snort/snort.lua:
Loading homenet.lua:
Finished homenet.lua:
Loading snort_defaults.lua:
Finished snort_defaults.lua:
Loading local.lua:
Finished local.lua:
snort
ssh
host_cache
pop
so_proxy
stream_tcp
mms
smtp
gtp_inspect
packets
dce_http_proxy
detection
alert_fast
suppress
cip
ips
stream_icmp
hosts
normalizer
binder
wizard
appid
js_norm
file_id
http2_inspect
http_inspect
stream_udp
ftp_data
ftp_server
search_engine
port_scan
dce_http_server
dce_tcp
dce_smb
iec104
telnet
ssl
sip
rpc_decode
netflow
modbus
host_tracker
stream_user
stream_ip
process
back_orifice
classifications
dnp3
active
trace
ftp_client
decode
alerts
stream
references
daq
arp_spoof
output
network
dns
dce_udp
imap
file_policy
s7commplus
stream_file
Finished /etc/snort/snort.lua:
Loading file_id.rules_file:
Loading file_magic.rules:
Finished file_magic.rules:
Finished file_id.rules_file:
Loading rules/snort.rules:
Finished rules/snort.rules:
--------------------------------------------------
pcre counts
pcre_rules: 11141
pcre_to_hyper: 8540
pcre_native: 2601
--------------------------------------------------
ips policies rule stats
id loaded shared enabled file
0 40857 0 40857 /etc/snort/snort.lua
--------------------------------------------------
rule counts
total rules loaded: 40857
text rules: 40857
option chains: 40857
chain headers: 1695
flowbits: 701
flowbits not checked: 82
--------------------------------------------------
port rule counts
tcp udp icmp ip
any 1802 380 455 287
src 1055 149 0 0
dst 4498 827 0 0
both 28 48 0 0
total 7383 1404 455 287
--------------------------------------------------
service rule counts to-srv to-cli
bgp: 5 1
dcerpc: 1400 1055
dhcp: 19 5
dns: 269 111
drda: 5 0
file: 773 784
ftp: 194 23
ftp-data: 1070 9132
gopher: 0 1
http: 15289 12166
http2: 15289 12166
http3: 15289 12166
ident: 1 0
imap: 1124 9387
ipp: 0 1
irc: 40 14
ircd: 9 3
java_rmi: 55 3
kerberos: 32 6
ldap: 42 8
ldp: 1 0
mysql: 5 0
netbios-dgm: 2 2
netbios-ns: 8 4
netbios-ssn: 1325 1055
netware: 2 0
nntp: 2 2
ntp: 36 7
openvpn: 16 16
pop3: 1081 9390
postgresql: 10 0
printer: 3 1
radius: 3 2
rdp: 3 8
rtmp: 1 4
rtp: 1 1
rtsp: 17 2
sip: 340 44
smtp: 8398 1028
snmp: 46 9
ssdp: 13 0
ssh: 13 6
ssl: 176 208
sunrpc: 118 9
syslog: 4 0
teamview: 1 2
telnet: 34 2
tftp: 6 5
vnc: 1 1
vnc-server: 12 10
total: 62583 68850
--------------------------------------------------
fast pattern groups
src: 478
dst: 1533
any: 8
to_server: 125
to_client: 95
--------------------------------------------------
search engine (hyperscan)
instances: 1230
patterns: 145965
fast pattern only: 95590
appid: MaxRss diff: 512
appid: patterns loaded: 300
--------------------------------------------------
nfq DAQ configured to inline.
Commencing packet processing
++ [0] 4
++ [1] 5
++ [2] 6
++ [3] 7
Again, the alert_fast txt files are getting populated over time.
# ls -lh *.txt
-rw------- 1 root root 117K Jul 18 17:19 0_alert_fast.txt
-rw------- 1 root root 0 Jul 18 15:17 1_alert_fast.txt
-rw------- 1 root root 2.5K Jul 18 17:21 2_alert_fast.txt
-rw------- 1 root root 2.4K Jul 18 17:17 3_alert_fast.txt