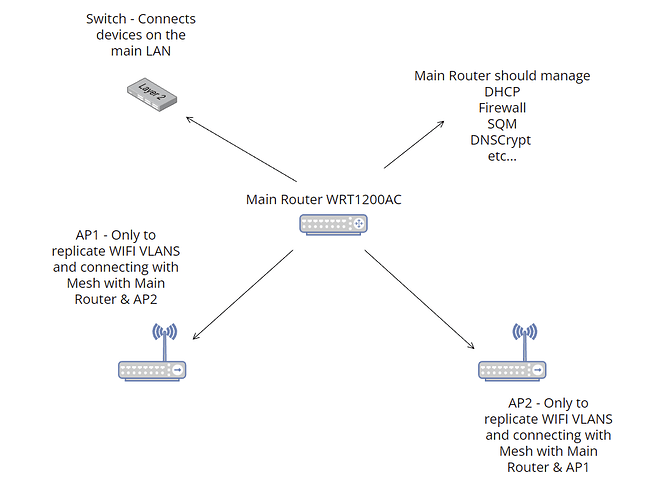
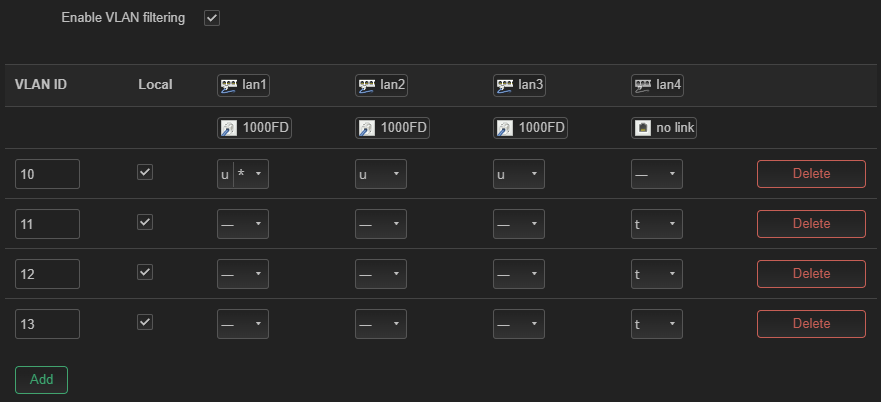
TLTR - Describing how I managed to fix the DHCP vlan issue and install AdGuard
But I have a couple of questions at the end...
Everything now works as it should.
After many re-flashes trials and errors, it finally works!
Reason of not giving DHCP on vlans, I came to conclusion that it must be my backup settings, something there, breaks this option but I couldn't think of it since without vlans, the DHCP worked...
Anyway I manually re configured everything and got it working.
Since I already lost my sleep two days now switching from the very old Snapshot r13342 to the latest one, I thought maybe is a good opportunity to change from DNSCrypt Proxy 2 to your recommendation @mercygroundabyss (AdGuard)
I've read both your guide and also this one from @directnupe
To be honest at some point I couldn't follow because the scripts throwed me errors, so I decided to combine your knowledge with what I do usually with DNSCrypt and it seems to work.
Below the procedure and your comments are more than welcome.
USB Storage | Format and configure as extroot for AdGuard Home.
-
Install USB related stuff
opkg update && opkg install block-mount e2fsprogs kmod-fs-ext4 kmod-usb-storage kmod-usb2 kmod-usb3 kmod-usb-storage-uas usbutils
-
Check USB name
ls -l /dev/sd*
or
block info
- Format USB
mkfs.ext4 /dev/sda1
Increase Routers Storage by Using The Available USB
mkdir /mnt/sda1
mount /dev/sda1 /mnt/sda1
mkdir -p /tmp/cproot
mount --bind / /tmp/cproot
tar -C /tmp/cproot -cvf - . | tar -C /mnt/sda1 -xf -
umount /tmp/cproot
Set Router to boot from USB
Edit the /etc/config/fstab (I did this by sshing with WinSCP)
changed the below lines.
config 'global'
option anon_swap '1'
option anon_mount '1'
config 'mount'
option target '/'
option uuid 'must be filled with the uuid of the usb from the block info command'
option enabled '1'
Save & Reboot
Now that I have that sorted out, it was time to install AdGuard Home.
Installation Procedure:
Necessary packages:
opkg update && opkg install sudo ca-certificates ca-bundle curl wget wget-ssl tar unzip bind-tools
AdGuard Home installation folder:
mkdir -p /opt/
I downloaded and extracted the package that corresponds to my router's architecture from here
Then moved the AdGuardHome folder created after the extraction with WinSCP to the path I created earlier /opt.
ssh again and hit the following in order to install AdGuard.
chmod 755 /opt/AdGuardHome/AdGuardHome
/opt/AdGuardHome/AdGuardHome -s install
After that, I went to the listening address of AdGuard that showed after the installation and configured the wizard.
Tweaks:
The below are the steps I always do with DNSCrypt so I did also with AdGuard.
Change the dnsmasq port from 53 to 5353
Luci > Network > DHCP and DNS > Advanced Settings > DNS Server Port
Prevent DNS Leaks & Disable dnsmasq Cache & Rebind Protection
Edit etc/config/dhcp and add
config dnsmasq
option noresolv '1'
option localuse '1'
option boguspriv '0'
option cachesize '0'
option rebind_protection '0'
Save & /etc/init.d/dnsmasq restart
Completely disable ISP's DNS
Edit etc/config/network
config interface 'wan'
option peerdns '0'
Force All Clients to use AdGuard Even if They Use a Different DNS
Edit /etc/config/firewall and add the following rules.
config redirect
option name 'Divert-DNS, port 53'
option src 'lan'
option proto 'tcp udp'
option src_dport '53'
option dest_port '53'
option target 'DNAT'
config rule
option name 'Reject-DoT, port 853'
option src 'lan'
option dest 'wan'
option proto 'tcp udp'
option dest_port '853'
option target 'REJECT'
config redirect
option name 'Divert-DNS, port 5353'
option src 'lan'
option proto 'tcp udp'
option src_dport '5353'
option dest_port '53'
option target 'DNAT'
At the end, I added to the router which DNS to use.
Luci > Network > DHCP and DNS > General Settings > DNS Forwardings and added the AdGuard DNS I configured in the setup wizard. ex: 192.168.1.1#53
Final step force AdGuard DNS to clients through DHCP.
In every interface I have (ex vlans) I edit each one with the following.
Luci > Network > Interfaces > Edit > DHCP Server > Advance Settings > DHCP Options and added the DNS with the 6, in front. ex 6,192.168.1.1
Rebooted the router and everything is working as it should!
Questions:
Under DNS Settings on AdGuard on the Private reverse DNS servers field I just added 127.0.0.1 and my dns ip ex 192.168.1.1.
Is that correct? I cannot figure exactly what IP I should add there.
Also should I enable Encryption if I use DoH servers already under Upstream DNS servers?
Otherwise they will not work? or this Encryption settings is if I don't want to use public servers and instead I have my own?
Thank you!