Hey guys is there a package that would let me configure a vpn thru graphic interface? I´m completly new to this and I don´t think i would be able to do it using ssh.
There are no web forms for strongswan, you will have to configure via its configuration files.
If IKEv2/IPSec isn't a hard requirement, both WireGuard and OpenVPN have LuCI (web) based configuration available.
Hi, @psherman
By your mention , can use WireGuard or OpenVPN which provide native VPN profile in Android 12/13?
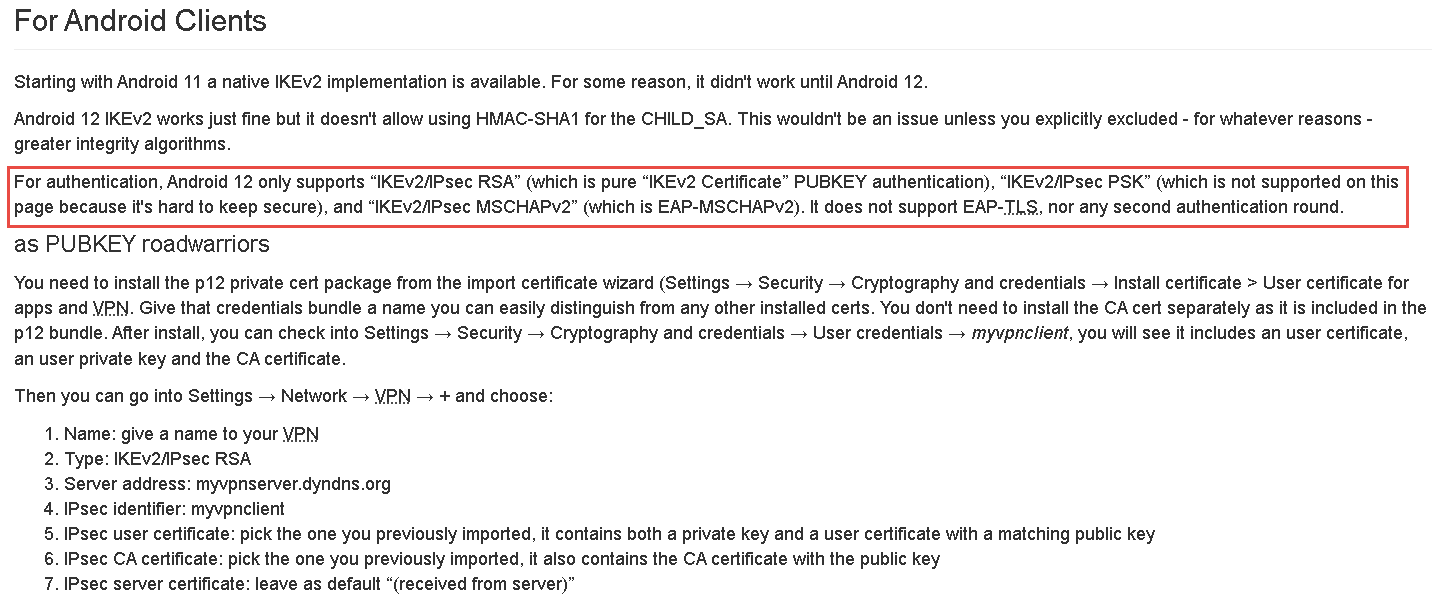
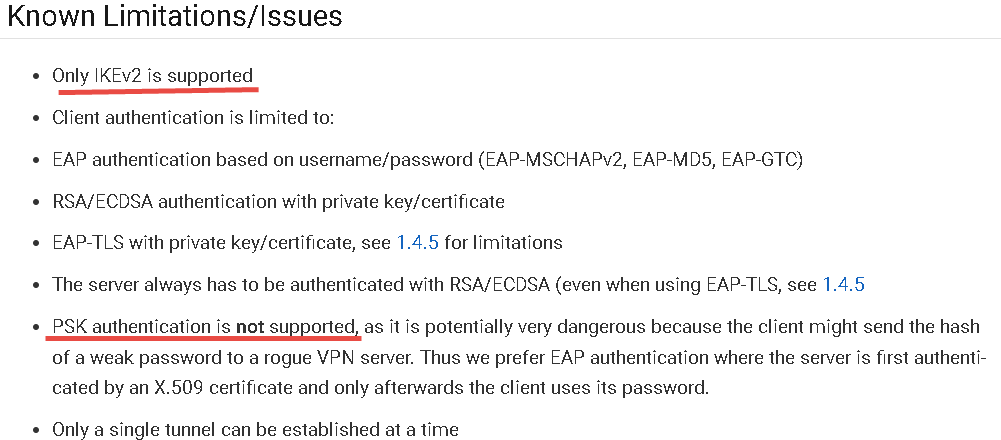
Form Android 12/13 only support IKEv2/IPsec MSCHAPv2,IKEv2/IPsec PSK,IKEv2/IPsec RSA,but I read the guide , look like don't support IKEv2/IPsec PSK
And also read from here, show don't support PSK
I would like to qucik build up the VPN server which let using native Android 12/13 VPN profile(client) to access VPN server.
Please kindly give some comments or help , thanks lot
Have you attempted to download the wireguard app on your android devices?
@psherman , thanks for your support.
I don't download the wireguard client app on my android
So far ,just study how to build VPN server in OpenWRT with RPi 4,and choice which kind of VPN server can quick build up .
As like @plebus 's requirement, prefer configure by GUI (Luci) may will be quickly.
And would like VPN client can access VPN server by using native VPN profile of Android 12/13 , not using VPN client app .
Take a look at @slh's comment about about Strongswan.
WireGuard is by far the fastest and easiest to setup.
Is there a reason you do not want to install the WireGuard app?
@psherman
Actually,my job is Android system testing engineer ,our Android devices test VPN feature always by using native Android VPN profile due to from our customer's requirement .
Recently, devices upgrade from Android 11 to Android 12/13 encounter as below:
- Only have three kinds of VPN profile as my above mentions in Android12/13 , and need to drop outdated VPN tyep as below

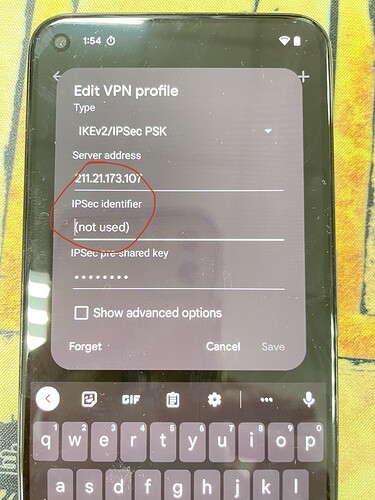
- Must to type in some values in "IPSec indentifier" filed otherwise can't save the VPN profile in Android 13.
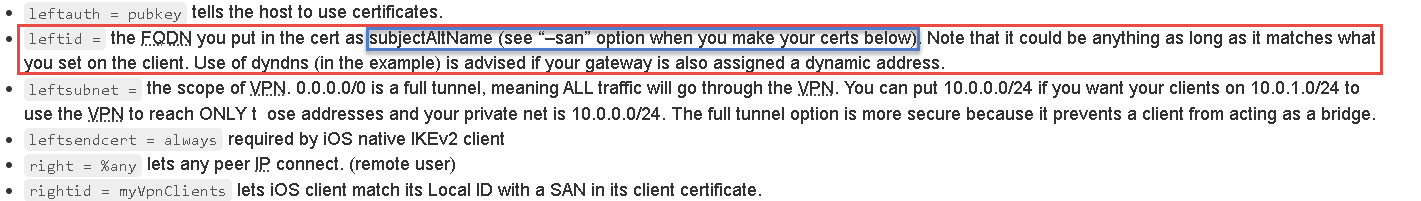
So far by my survey, seam related "cert as subjectAltName" and Unfortunately I don't have any background or senses for the cert as DNS.
Hope can get your kindly help , and excuse my poor English and new hand in OpenWRT.
You realize that the router side would get a tad more complex than that?
On the one hand you have:
- VPN 'server' (for road-warrior clients like your phones to connect)
- VPN client (to use some commercial VPN)
- site2site VPN
In the VPN server case, you will need some way to create and manage the certificates - in the client case you need some way to import them. In all cases you may need to transpose them from one container format to another.
On OpenWrt, strongswan is split into many tiny plugin packages for size reasons, reacting dynamically to this isn't going to be trivial (both in the sense of not breaking when necessary parts are not installed, as well as helping the user what to install for their use case).
Of course this is all imaginable, just far from trivial to design, write and maintain (over time there will be changes, strongswan has already changed quite significantly in recent months).
In comparison, wireguard is trivial to set up - and has native kernel support on recent (android-) devices.
It might be useful if you can tell us the nature of the testing that you need to perform using a VPN. Maybe we can help you with the information to provide to your customer about why another VPN protocol is okay. Obviously if the details are confidential, we don't want you to expose any sensitive information. But maybe you can provide something of a generic explanation about what you need to achieve, as well as why it specifically has to work only the native VPN protocols.
As @slh has described, IKEv2/IPSec VPNs are quite a bit more complex than WG or even OpenVPN (FWIW, I can personally help with WG and OpenVPN, but I've never setup an IPSec VPN, so I won't be able to help if you need IKEv2 supported protocols).
Another approach is to simply buy a ready-made VPN appliance that has support for these protocols. That would obviously not be an OpenWrt thing, but then you don't have to spend tons of time learning how to configure a VPN server for your testing.
Meanwhile, regarding Strongswan... take a look at the documentation:
From personal experience (srx5308, various revisions of the fvs-318, quite a few Lancom devices, interoperability with Cisco ASA, NCP, greenbow , Microsoft, and shrewsoft, …), commercial appliances don't make the situation that much easier, unless you're running their branded VPN clients (at best, the used configuration parameters (and certificate format requirements) that would make other VPN clients work are horribly underdocumented, if you're 'lucky' you'll encounter various bugs or limits (only support for old cyphers)). While IPsec is technically standardized (and an open industry standard at that), the details can drive you mad, really mad.
strongswan is a proven implementation which supports most of those protocol flavours, but that also means a very, very complex configuration at times (and tunnel supervision did change since I last used it on OpenWrt).
Thanks for @psherman and @slh kindly reply and comments
I know it's difficult for create and manage the certificates/anything in server or client ,But I still have to build up the VPN server by my self.
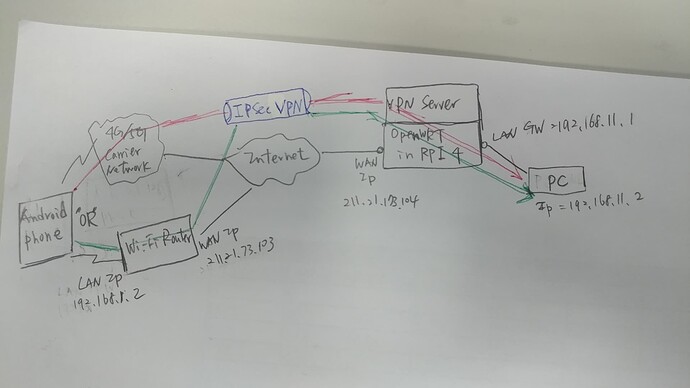
I re-summarize my question and requirement and draw a schematic diagram as below
Requirement :
-
Android Phone based on Android AOSP 12 or 13 ,like Google Pixel 5,6
-
The Phone can connect to Internet via 4G/5G carrier network or wireless through Wi-Fi Router
-
The phone must / have to create IKEv2/IPsec MSCHAPv2,IKEv2/IPsec PSK,IKEv2/IPsec RSA VPN profiles in native Android 12 or 13, don't use any VPN client app.
-
When the VPN tunnel establish between Phone and PC(as diagram show red path or green path), the phone can ping to PC and PC can reply to phone in order to confirm the two endpoints are connecting. (Will execute ping command via adb shell in phone)
Questions:
- I study and research many information by google, know OpenVPN,WireGuard,OpenConnect,strongSwan / IPsec these server package might to arrive my requirement .Which one will easy to build up quickly?
And it would be better to have a GUI(LuCI) setting . As @psherman 's above relply, Will WireGuard be easy for build up the server quickly ?? - Due to configuration , seem to establish(or configure?) DNS server first in OpenWRT?
- Whatever red path or green path , are all the two path belong to site to site VPN ?
wireguard is much easier to set up, but it doesn't speak the IPsec protocol(s) and needs its VPN app (but it can use the wireguard kernel modules, if your android vendor ships them and a recent enough kernel, otherwise it falls back transparently to a userspace implementation written in go(lang)). Native wireguard support is provided in recent Linux distributions, native FreeBSD support is close - Windows and MacOS (userspace-) apps exist.
What isn't clear to me is why the customer requires this limitation. You don't necessarily need to explain it to me/us, but it might be worth revisiting this in your conversations with them. Setting up the VPN protocols they are requiring is going to be a ton of extra work for you (and/or your team), whereas WG can be setup in less than 10 minutes if you know what you're doing. Usually, the VPN protocol doesn't matter for applications running on a device -- it is typically transparent (or nearly so) because the OS is actually handling the tunnel at a lower level than the applications.
There is nothing in your diagram that explicitly requires the use of one VPN protocol over another... therefore, my recommendation would be to ask the customer why they care what VPN method is used.
Thanks for @psherman 's reply. Sorry about my incomplete information for this issue.
Actually, the customer's product is the Android handheld enterprise device which develop based on Android ASOP, and customer don't care /mind how to build up the VPN server and what's kind VPN protocol , just care the native VPN client function is work correctly or not.
Well, I guess that means you’ll have to learn to setup those ipsec vpns. As I mentioned before, I have never done it, so I can’t help on this front. But I hope someone who is experienced with strongswan can give you some pointers.
Strongswan ikev2 ipsec is quite complex to config,but not that difficult because you can leave most of the parameters default,You can find all you need in this article:https://openwrt.org/docs/guide-user/services/vpn/strongswan/roadwarrior