(Edit: this example makes reference to DHCP, because that was what I was looking at when I noticed it. Please ignore whether the rule makes any sense in the context of DHCP.)
I was slightly confused by this at first, but it makes sense once the mapping from the luci gui to the iptables rules is considered, but I think it's potentially opens the firewall more than intended.
If you create a rule like this;
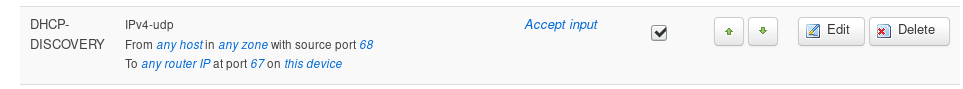
It generates /etc/config/firewall code like this...
config rule
option target 'ACCEPT'
option dest_port '67'
option name 'DHCP-DISCOVERY'
option family 'ipv4'
option src '*'
option src_port '68'
option proto 'udp'
The resulting iptables rule is like this;
3 972 ACCEPT udp -- any any anywhere anywhere udp spt:bootpc dpt:bootps /* !fw3: DHCP-DISCOVERY */
All good.
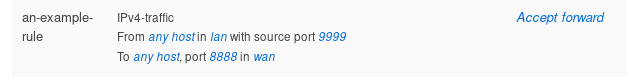
However if you go and set the rule to use the any protocol option like so;

The result looks like it would apply some form of fairly restrictive port filter to the rule...

It looks like it's going to be filtered on src and dest port;
The generated /etc/config/firewall still looks OK....
config rule
option target 'ACCEPT'
option dest_port '67'
option name 'DHCP-DISCOVERY'
option family 'ipv4'
option src '*'
option src_port '68'
option proto 'all'
But the final rule created ignores the port spec, (which makes sense, because iptables would need need the protocol to be specified as TCP or UDP to do anything useful with the port options);
63 6174 ACCEPT all -- any any anywhere anywhere /* !fw3: DHCP-DISCOVERY */
However the thing to notice is that it's now opened everything from anywhere into the router... which might not be what was intended or expected..
Possible the port spec fields need to be grayed out if the any protocol is used...