Hello,
I need help configuring PBR so that OpenVpn and Wireguard can work at the same time. I have no idea how it is done. And I tried to create Policies, but I haven't got anything.
I have the following Network settings at home.
I have a FritzBox Cable 6591 YN, this is only in charge of passing the Internet to a FritzBox 4040. On the FritzBox 4040 I have installed at the moment OpenWrt 19.07.2.
In OpenWrt I have a Wireguard Tunnel for mobiles and OpenVpn for NordVpn servers.
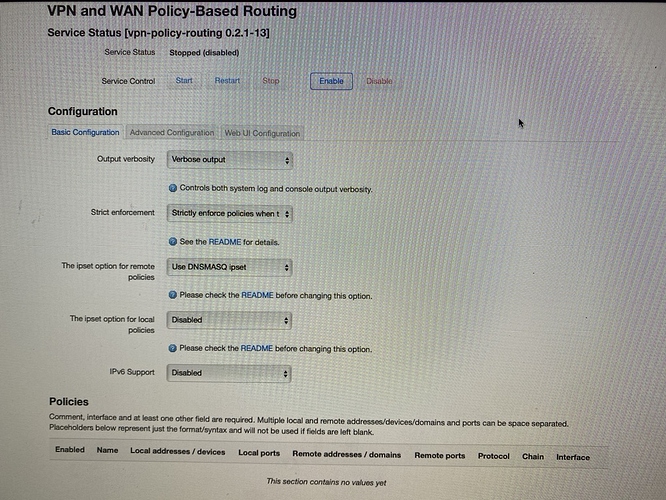
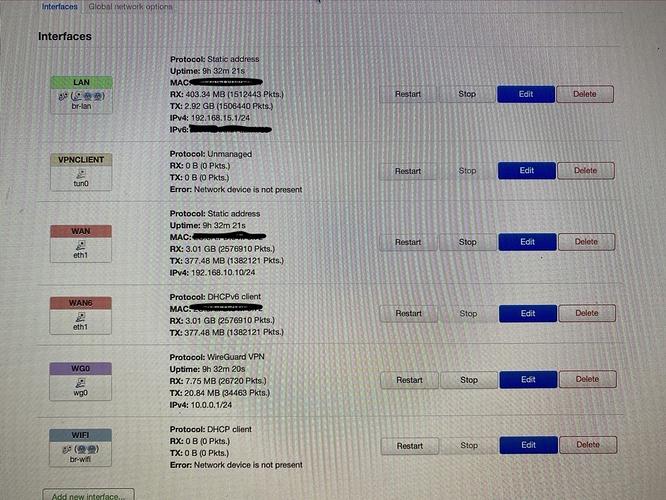
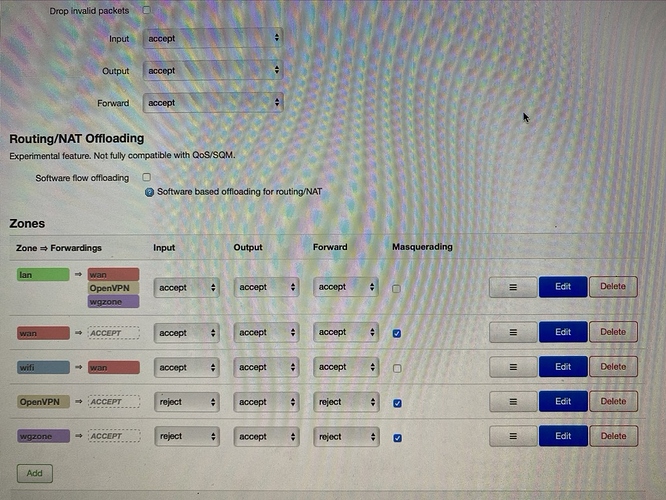
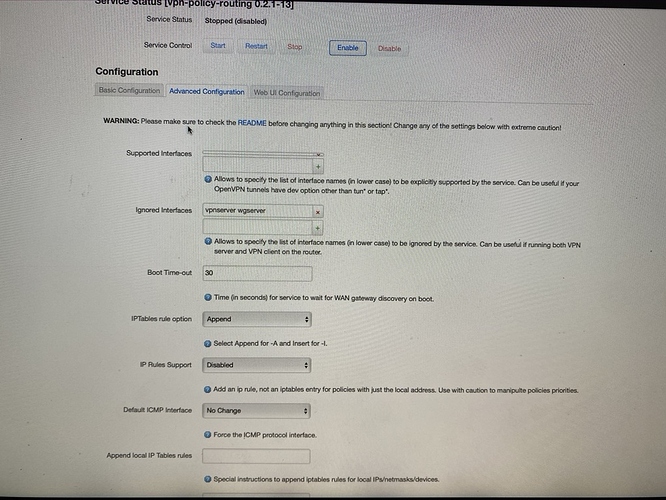
Here some photos of the Interface
You may want to allow traffic from WG to lan then.
Please don't post photos. Post instead the configuration files.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
uci export vpn-policy-routing; \
head -n -0 /etc/firewall.user; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*
where i have to put these commands to get the results. I don't have much idea of how to get it
Use ssh to connect to the device and run the commands.
I've a Problem. when I type in the Terminal from my iMac , have this response:
xxxxxxxxxxxxxxxxxx@iMacxxxxxxx ~ % ssh root@192.168.15.1
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the RSA key sent by the remote host is
SHA256:30EiBd1pH5cCT6Yz+U+BxIe3Mv8dyFNAlWMGjqF6zvY.
Please contact your system administrator.
Add correct host key in /Users/xxxxxxxxxxxxxxxxxx/.ssh/known_hosts to get rid of this message.
Offending RSA key in /Users/xxxxxxxxxxxxxxxxxxxxx/.ssh/known_hosts:1
RSA host key for 192.168.15.1 has changed and you have requested strict checking.
Delete the first line from that file.
what line?
The first line from this file.
ubus call system board; \
> uci export network; uci export wireless; \
> uci export dhcp; uci export firewall; \
> uci export vpn-policy-routing; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
> ls -l /etc/resolv.* /tmp/resolv.*; head -n -0 /etc/resolv.* /tmp/resolv.*
{
"kernel": "4.14.171",
"hostname": "Heimnetz",
"system": "ARMv7 Processor rev 5 (v7l)",
"model": "AVM FRITZ!Box 4040",
"board_name": "avm,fritzbox-4040",
"release": {
"distribution": "OpenWrt",
"version": "19.07.2",
"revision": "r10947-65030d81f3",
"target": "ipq40xx/generic",
"description": "OpenWrt 19.07.2 r10947-65030d81f3"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd91:31ed:87d2::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.10.1'
option ipaddr '192.168.15.1'
config interface 'wan'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.10.10'
option gateway '192.168.10.1'
list dns '192.168.10.1'
option metric '0'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 4'
option vid '1'
config interface 'wifi'
option ifname 'radio0.network1 radio1.network1'
option type 'bridge'
option proto 'dhcp'
config interface 'wg0'
option proto 'wireguard'
option private_key '
option listen_port '52466'
list addresses '10.0.0.1/24'
config wireguard_wg0
option public_key '
option description '
option persistent_keepalive '25'
list allowed_ips '10.0.0.2'
option route_allowed_ips '1'
option endpoint_host '
option endpoint_port '52466'
config wireguard_wg0
option public_key '
option description
option persistent_keepalive '25'
option endpoint_port '52466'
list allowed_ips '10.0.0.3'
option route_allowed_ips '1'
option endpoint_host '
config interface 'vpnclient'
option ifname 'tun0'
option proto 'none'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'platform/soc/a000000.wifi'
option htmode 'HT20'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option key '
option ssid ''
option encryption 'psk-mixed'
config wifi-device 'radio1'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'platform/soc/a800000.wifi'
option htmode 'VHT80'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option key ''
option ssid '
option encryption 'psk-mixed'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option start '100'
option limit '150'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'wifi'
option leasetime '12h'
option interface 'wifi'
option start '150'
option limit '100'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'wifi'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option network 'wifi'
config forwarding
option dest 'wan'
option src 'wifi'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '51820'
option name 'Allow-Wireguard-Inbound'
config zone
option name 'OpenVPN'
option mtu_fix '1'
option masq '1'
option output 'ACCEPT'
option network 'vpnclient'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option dest 'OpenVPN'
option src 'lan'
package vpn-policy-routing
config include
option path '/etc/vpn-policy-routing.aws.user'
option enabled '0'
config include
option path '/etc/vpn-policy-routing.netflix.user'
option enabled '0'
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option dest_ipset 'dnsmasq.ipset'
list supported_interface ''
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option src_ipset '0'
option webui_enable_column '1'
option webui_protocol_column '1'
option webui_chain_column '1'
option ipv6_enabled '0'
option enabled '0'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
inet 192.168.10.10/24 brd 192.168.10.255 scope global eth1
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.15.1/24 brd 192.168.15.255 scope global br-lan
valid_lft forever preferred_lft forever
7: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
inet 10.0.0.1/24 brd 10.0.0.255 scope global wg0
valid_lft forever preferred_lft forever
default via 192.168.10.1 dev eth1 table 1
10.0.0.0/24 dev wg0 table 1 proto kernel scope link src 10.0.0.1
10.0.0.2 dev wg0 table 1 proto static scope link
10.0.0.3 dev wg0 table 1 proto static scope link
192.168.10.0/24 dev eth1 table 1 proto kernel scope link src 192.168.10.10
192.168.15.0/24 dev br-lan table 1 proto kernel scope link src 192.168.15.1
default via 192.168.10.1 dev eth1 proto static
10.0.0.0/24 dev wg0 proto kernel scope link src 10.0.0.1
10.0.0.2 dev wg0 proto static scope link
10.0.0.3 dev wg0 proto static scope link
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.10
192.168.15.0/24 dev br-lan proto kernel scope link src 192.168.15.1
broadcast 10.0.0.0 dev wg0 table local proto kernel scope link src 10.0.0.1
local 10.0.0.1 dev wg0 table local proto kernel scope host src 10.0.0.1
broadcast 10.0.0.255 dev wg0 table local proto kernel scope link src 10.0.0.1
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.10.0 dev eth1 table local proto kernel scope link src 192.168.10.10
local 192.168.10.10 dev eth1 table local proto kernel scope host src 192.168.10.10
broadcast 192.168.10.255 dev eth1 table local proto kernel scope link src 192.168.10.10
broadcast 192.168.15.0 dev br-lan table local proto kernel scope link src 192.168.15.1
local 192.168.15.1 dev br-lan table local proto kernel scope host src 192.168.15.1
broadcast 192.168.15.255 dev br-lan table local proto kernel scope link src 192.168.15.1
0: from all lookup local
1001: from all iif eth1 lookup 1
2001: from all fwmark 0x100/0x3f00 lookup 1
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
lrwxrwxrwx 1 root root 16 Feb 27 22:05 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jun 22 06:00 /tmp/resolv.conf
-rw-r--r-- 1 root root 40 Jun 20 09:23 /tmp/resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface wan
nameserver 192.168.10.1
root@Heimnetz:~#`Preformatted text`
I don't think, that it is possible due to UDP. However @krazeh wrote, that it can be done. @krazeh, it is the same question, I've asked you! So it will be interesting to see solution.
Please use the "Preformatted text </>" button for logs, scripts, configs and general console output.
![]()
Please edit your post accordingly. Thank you! 
Does the data serve you?
Try to add wan policy for UDP 51820 local port (OUTPUT chain, you should initially enable chain column in general settings). See also Readme for PBR: https://github.com/stangri/openwrt_packages/blob/master/vpn-policy-routing/files/README.md Local Wireguard Server + Wireguard Client (Scenario 1)
This guide does not help me personally to solve the problem. I need help to create the specific policies for me and if it can be step by step what I have to do
Create some policy in LuCI, and give config of PBR.
I have previously tried to create Policies in PBR, but I cannot, I do not have enough knowledge to create them correctly
Press 'Add' button, and give screenshot.
Much better, yes!
Now first step is to declare in VPN-PBR the interfaces to ignore. wg0 is your server so this needs to be in the ignore list. vpnclient should be in the supported interface list. You'll find these both in the advanced tab of VPN-PBR.
Other than that I don't see the wg0 interface in any zone in the firewall. You can add that in the lan firewall zone for simplicity.
Regarding the rules, what do you want to achieve?
What I want to achieve is, when I use NordVpn in OpenVpn do not lose the Wireguard Vpn connection with my mobiles and they keep working on the router.
I don't know if I explained it well?
Now I have the problem that while OpenVpn is deactivated my connection Router-Mobile Phone is perfect and when I activate OpenVpn the connection no longer exists
Yes, I understood what you want to say.
Do you switch the OpenVPN on and off all the time? Or do you want to keep it always connected and route some devices through VPN and the others through WAN?