dloop
August 21, 2022, 10:22pm
1
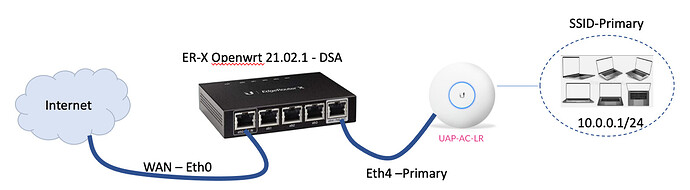
Apologize for the long post. I have this basic configuration, and it is working fine.
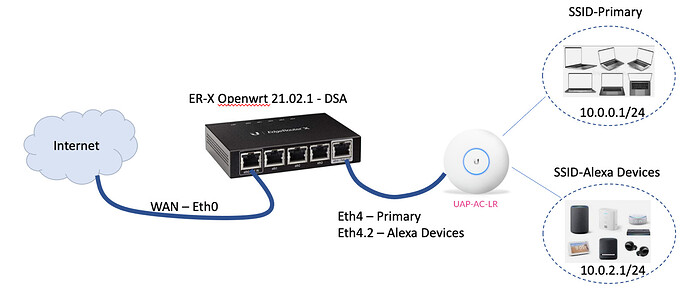
I would like to add to this a separate VLAN (Vlan ID:2 )for several Alexa devices that are in our home. I want the Alexa devices to be able to see each other but kept separate from the primary LAN. Something like this:
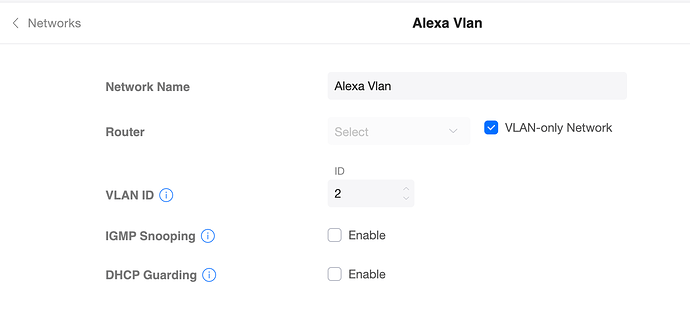
In the configuration for the Unifi AP. I create VLAN 2.
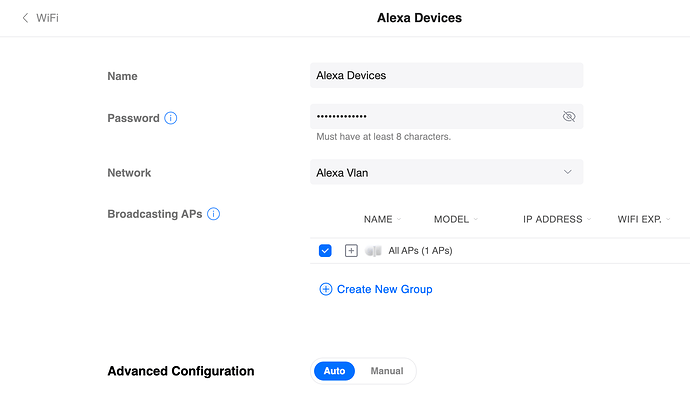
Then I create a new Wifi zone for the Alexa Devices and associate it with the VLAN above:
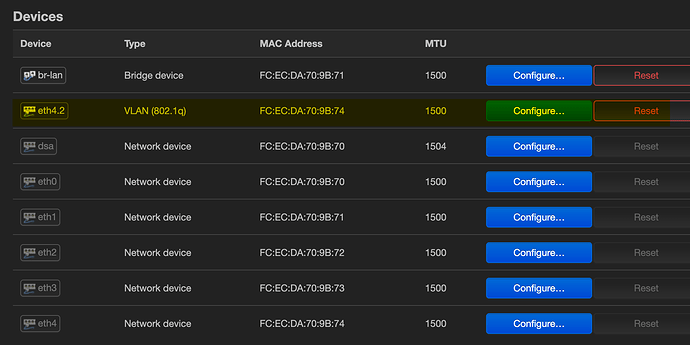
On the Openwrt/ER-X, I create eth4.2:
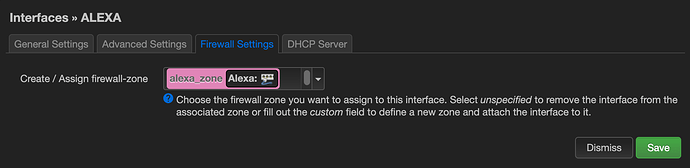
Then the new Alexa interface using eth4.2:
I'm clearly doing something wrong. The Primary wireless is not affected and computers connecting to it continue to work fine. But when connecting to the Alexa Devices SSID it doesn't appear to get into a DHCP conversation and no network connection is established.
Appreciate any guidance you can provide.
Let's look at your OpenWrt config (in text form):
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
mk24
August 22, 2022, 12:35am
3
Put the management and trusted wifi on a VLAN as well. Don't try to mix tagged and untagged packets on the same cable.
On the OpenWrt router, create two bridge-vlans 1 and 2 and designate eth4 as a tagged port in each, the other LAN ports (eth1 eth2 and eth3) as untagged in VLAN 1. Change the lan device from br-lan to br-lan.1. As you set up bridge-vlans the extra interfaces and 802.1q stuff is automatically done.
dloop
August 22, 2022, 2:49am
4
Thanks Peter.
etc/config/network
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.0.1'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config device
option type '8021q'
option ifname 'eth4'
option vid '2'
option name 'eth4.2'
config interface 'Alexa'
option proto 'static'
option device 'eth4.2'
option ipaddr '10.0.2.1'
option netmask '255.255.255.0'
/etc/config/wireless
can't open '/etc/config/wireless': No such file or directory
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option confdir '/tmp/dnsmasq.d'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
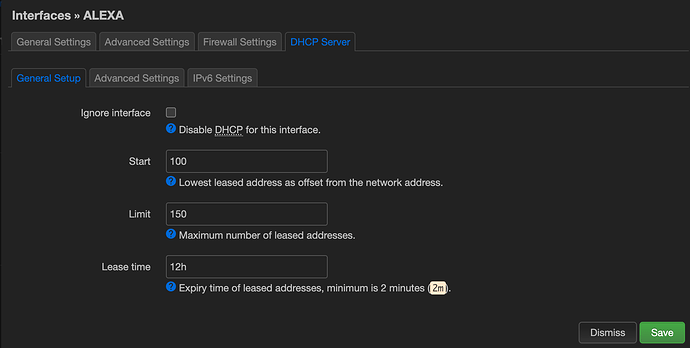
config dhcp 'Alexa'
option interface 'Alexa'
option start '100'
option limit '150'
option leasetime '12h'
list ra_flags 'none'
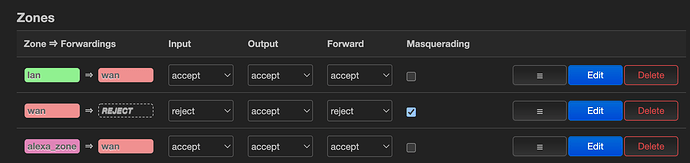
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
list network 'Alexa'
option forward 'ACCEPT'
option name 'alexa_zone'
config forwarding
option src 'alexa_zone'
option dest 'wan'
dloop
August 22, 2022, 2:51am
5
Good idea Mike. I should have thought of putting them both in a VLAN.
You appear to be mixing older (swconfig, previous OpenWrt versions) config syntax with newer stuff. This won't work as configured now.
You'll want it to look something like this, instead:
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan4:t'
config interface 'Alexa'
option proto 'static'
option device 'br-lan.2'
option ipaddr '10.0.2.1'
option netmask '255.255.255.0'
papdee
August 22, 2022, 7:18am
7
Generally I avoid using vlan 2 and consider it a reserved VLAN ID just like 0, 1, and 4096. The reasons are some routers and APs utilize vlan 2 internally hardcoded into their firmware. Not sure about Unifi stuff but could be same issue as other manufacturers.
When designing a network I generally have a set of reserved VLANs and IP addresses that should never be used:
reserved VLANs: 0, 1, 2, 4096