This HOWTO is intended for the relatively new users who have some experience with general computing and system administration but are not (yet) comfortable with flashing firmware and need some friendly handholding to get through the process. Some potentially necessary general education will be provided along the way.
Variants of this HOWTO have been tested on the following models:
- FG-50E
- FWF-50E-2R
- FWF-51E
In addition, this HOWTO, with trivial modifications, should work for the following related models:
- FG-30E
- FG-51E
- FG-52E
The modifications needed should be obvious from the context.
An abbreviated (and written specifically for the FWF-50E-2R) version of this HOWTO has been incorporated into the device page for the FWF-50E-2R:
https://openwrt.org/toh/fortinet/fortinet_fortiwifi_50e-2r
A quick word on versioning
As of this writing, there's only one model, FG-50E, for which OpenWrt is available in release (the current release is 23.05.5). Firmware for that model can be downloaded from this page:
https://downloads.openwrt.org/releases/23.05.5/targets/mvebu/cortexa9/
Firmware for all other models mentioned above (as well as for the FG-50E) is available in snapshots and can be downloaded from this page:
https://downloads.openwrt.org/snapshots/targets/mvebu/cortexa9/
In case you're new to OpenWrt, a "release" is a regular version deemed ready for normal everyday use; a "snapshot" is a version in development, usually updated daily (this is why firmware that is in release is also available in snapshots, but not necessarily the other way around; development continues after release, toward the next release). Note that release builds are fully functional, while snapshot builds are minimal; specifically, they exclude LuCI (OpenWrt's Web-based management interface). However, LuCI (as well as any other package not included in the snapshot but available in the repository) is installable on demand (we will discuss it later).
The hardware
All devices referenced above are built on the Marvell 88F6820 processor. It is a dual-core ARM Cortex-A9 chip running at 1.6 GHz.
FG-30E is the entry-level wired-only device. It has 1 GB RAM, a 128 MB Flash storage device, one WAN port, and four LAN ports in a switch configuration.
FG-50E is the next step up. It has 2 GB RAM, a 128 MB Flash storage device, two WAN ports, and five LAN ports in a switch configuration.
The remaining devices are variants of FG-50E that may feature SSD storage and/or wireless hardware (a single N-standard wireless card or dual N- and AC-standard wireless cards). All wireless cards are Qualcomm Atheros. The N-standard cards use the ath9k driver; the AC-standard cards use the ath10k-ct driver with ath10k-firmware-qca988x-ct firmware.
A mildly frustrating feature of these devices is that they have two-pin Molex connectors for power, rather than the more typical barrel connectors. As a result, power supplies can be hard to find or, when found, more expensive. Electrically, however, they are very typical, requiring 12 V / 2 A DC power.
Preparations
To install OpenWrt on one of these devices, you will need:
- A computer ("administrator's workstation") with software capable of console connection (in terms of software for console connection, I used
screenon Linux, but you can use Putty on Linux or Windows and probably many other terminal emulation programs) - A console cable (I used the kind that connects the RJ-45 console port on the router to a USB port on the administrator's workstation)
- An Ethernet cable
- A TFTP server (I used a separate computer, but you can deploy the TFTP server software on your administrator's workstation)
Begin by setting up the TFTP server. Incidentally, TFTP stands for Trivial File Transfer Protocol. It is a simple, no-frills (and no-security) way for one machine to share files with another. A typical use case for TFTP is network boot, often used by thin clients and, occasionally, by fat servers. We'll use TFTP to boot our router into OpenWrt.
On most Linux flavors, spinning up a TFTP server involves a one-line command to the package manager and a glance at the newly created configuration file. My designated TFTP server was an Ubuntu Server 22.04, so I elevated myself to root and installed the TFTP server software:
apt install tftpd-hpa
When installation is complete, you can check how your new TFTP server is doing:
systemctl status tftpd-hpa
In my case, under Ubuntu, the output of this command contains a line stating Active: active (running), indicating that the TFTP service is ready for use.
Next, take a look at your TFTP configuration file:
cat /etc/default/tftpd-hpa
Find the line that starts with TFTP_DIRECTORY; this is where you will need to put files that you want to be accessible via TFTP. In my case, it was /srv/tftp. Write it down for future reference.
Next, change your network settings so that the Ethernet port to which the router will be connecting has a fixed IP address, 192.168.1.168. Your router will look for files to use at boot at this IP address (it is possible to change that, and we will discuss it later; it is also possible that this default setting has been changed by a previous user of your router). In my case, I changed the TFTP server's IP address by editing the Netplan configuration file, which resides at:
/etc/netplan/00-installer-config.yaml
In your case... check your OS documentation.
Next, change to the TFTP files directory you identified earlier and wrote down for future reference:
cd /srv/tftp
and download the initial boot file (also known as initramfs) for your device. To download current firmware, go to the appropriate downloads page (see A quick word on versioning above). Find the appropriate initramfs file for your device; it will be one of the following (note model numbers included in file names):
fortinet_fg-30e-initramfs-kernel.bin
fortinet_fg-50e-initramfs-kernel.bin
fortinet_fg-51e-initramfs-kernel.bin
fortinet_fg-52e-initramfs-kernel.bin
fortinet_fwf-50e-2r-initramfs-kernel.bin
fortinet_fwf-51e-initramfs-kernel.bin
Once you found the file you need, download it to your TFTP server. The easiest way to do that is to copy a URL to clipboard and then paste it into the terminal accessing the TFTP server after manually typing wget. It is also a good idea to give the file a shorter name. By default, during the TFTP install, your router will look for a file named image.out, but it is a setting that can be changed (we will discuss changing it later).
For example, if you wanted to get the snapshot initramfs file for the FG-50E and store it under the name image.out, you would do:
wget -O image.out https://downloads.openwrt.org/snapshots/targets/mvebu/cortexa9/openwrt-mvebu-cortexa9-fortinet_fg-50e-initramfs-kernel.bin
Leave the browser window open; you will need another URL from it fairly soon.
Before booting the router
Make sure you have the following in place:
- The router is off (there's no power switch on the router, so plug the power supply into the wall, but don't plug it into the router yet)
- The WAN and LAN ports on the router are not connected to anything
- The Console port on the router is connected to the administrator's workstation
Next, start a console connection at 9600 bps on the administrator's workstation. In my case, this was done on the command line:
sudo screen /dev/ttyUSB0 9600
Now plug the router in. Be sure to start watching the console output immediately.
The actual installation
Almost immediately after you power up the router, it will output something along these lines:
FortiGate-50E (17:37-01.31.2017)
Ver:05000016
Serial number:
CPU(00): 1600MHz
Total RAM: 2GB
Initializing boot device...
Initializing MAC...
Please wait for OS to boot, or press any key to display configuration menu.
At this point, the router will pause for a few seconds to let you decide whether you want to interrupt the boot process. You do, so press Enter. You will be shown the boot menu that looks like this:
[C]: Configure TFTP parameters.
[R]: Review TFTP parameters.
[T]: Initiate TFTP firmware transfer.
[F]: Format boot device.
[I]: System information.
[B]: Boot with backup firmware and set as default.
[Q]: Quit menu and continue to boot.
[H]: Display this list of options.
Enter C,R,T,F,I,B,Q,or H:
From here, there are at least three ways to go:
- You can use option
Rto see what TFTP settings the router expects, then go back to your TFTP server and adjust its settings to what the router expects, then use optionTto boot into OpenWrt, or - You can use option
Cto adjust the router's TFTP settings to match the settings you already have on your TFTP server, then use optionTto boot into OpenWrt, or - You can use option
G(for some reason, it doesn't appear on the menu) to configure TFTP boot interactively.
In the opinion of this writer, the last option is the most straightforward, so let's use it. Press G on the keyboard (do not follow it by Enter). You will be asked to specify TFTP connection settings one by one. The interaction will look like this:
Please connect TFTP server to Ethernet port 'WAN1'.
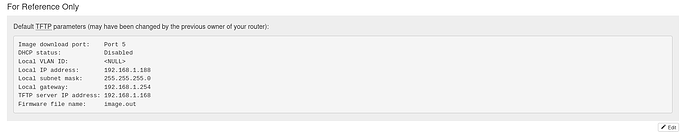
Enter TFTP server address [192.168.1.168]:
Enter local address [192.168.1.188]:
Enter firmware image file name [image.out]:
In the example above, the user agreed to all default settings (given in square brackets) by pressing Enter every time. (Note that "local address" refers to the IP address of the router, to be used for TFTP connection only.) Alternatively, the user could have entered different settings on any or all of the lines. Note also that the first thing you have been asked to do is to connect the TFTP server to a specific port on the router (in this example, WAN1), so don't forget to do that.
When you enter (or confirm, as the case may be) all settings, the router will attempt to retrieve the initramfs from the TFTP server in accordance with the settings you provided. If successful, it will ask you how you want to run the firmware:
Connect to tftp server 192.168.1.168 ...
###########
Image Received.
Checking image... OK
Save as Default firmware/Backup firmware/Run image without saving:[D/B/R]?
Choose option R; this will tell the router to boot into OpenWrt but not to save it to storage. You will see the familiar OpenWrt boot sequence. When the boot sequence is complete, press Enter to gain OpenWrt command prompt.
At this point, OpenWrt is running in-memory, so you need to write it to the persistent storage. To do that, you need to perform a sysupgrade. Disconnect your router from the TFTP server and connect one of the router's WAN ports to your upstream device. Test your Internet connection, by, say, pinging Google:
ping -c 3 google.com
If the connection is active, perform sysupgrade. Remember, all the way back in Preparations, we left a browser window open? Go back to that window and find the sysupgrade file for your router; it will be right next to the initramfs file you downloaded earlier. Copy the file's URL to clipboard, then go to your terminal and use it with the sysupgrade command. For example, to sysupgrade OpenWrt on FWF-50E-2R, you would do:
sysupgrade https://downloads.openwrt.org/snapshots/targets/mvebu/cortexa9/openwrt-mvebu-cortexa9-fortinet_fwf-50e-2r-squashfs-sysupgrade.bin
Sysupgrade will commence. After firmware is downloaded and written to persistent storage, your router will reboot, most likely, into OpenWrt. Why most likely? Because your router has dual firmware layout, so OpenWrt occasionally gets written as backup firmware rather than default firmware. If that happens, the device will boot with stock firmware following sysupgrade. So if you notice that the device is booting with stock firmware, reboot the device, interrupt the boot to gain access to the boot menu, and use option [B]: Boot with backup firmware and set as default; this will tell the router to boot with OpenWrt and set OpenWrt as the default firmware.
Post-install
At this time, it is difficult to give a coherent set of directions for what you need to do post-install. Depending on your router model, you could have installed a release or a snapshot. If you installed a release, there's not a whole lot to do; you have a fully functional firmware, so you can go ahead, log in (login name root, empty password), and start configuring your router. If you installed a snapshot, you may want to install some additional packages. Which ones? Probably luci, if you need the Web management interface (most people do). If you have a wireless router, you may need a driver and possibly firmware for the Wi-Fi card(s) (kmod-ath9k driver if you have an N-standard card or kmod-ath10k-ct driver with ath10k-firmware-qca988x-ct firmware if you have an AC-standard card), although chances are, they will be included even in the snapshot.
To make things even more confusing for a new user, OpenWrt is in the process of changing package managers. As of this writing, the most recent release uses the opkg package manager, while in snapshots, there's been a changeover to the apk package manager. As a result, the procedure for installing packages will differ depending on what package manager you have at your disposal. For example, if you want to install luci and luci-ssl (an optional helper package that allows LuCI to run securely using SSL) with opkg, you would do
opkg update && opkg install luci luci-ssl
With apk, it's the same general idea, but the implementation is slightly different:
apk update && apk add luci luci-ssl
You can also use your package manager to check whether a specific package is already installed (and you can use wildcards for it). For example, to see what you have available for ath10k, you can do
opkg list-installed *ath10k*
or
apk list --installed *ath10k*
Note the difference in syntax: opkg has a list-installed command, while in apk, you must use the list command with the --installed option (without the option, apk will show you a list of packages available anywhere it is allowed to look for packages: in the repositories and on your local system).
Notes on the future
I have next to no visibility into the development process, but from the publicly available information, it appears that release 24.10 is coming out relatively soon (most likely, before the end of 2024). I suspect that at least some of the devices we discussed will be in release at that point, in addition to the FG-50E that is in release already. I am also aware of a plan to add support for FWF-50E (which is basically FG-50E plus an N-standard Wi-Fi card), although I've been told that there is no firm timeline on that.
On a related note, opkg will reportedly remain the package manager for 24.10, while snapshots will have apk. Some time in 2025, the changeover will be complete, and apk will become the sole package manager in OpenWrt.