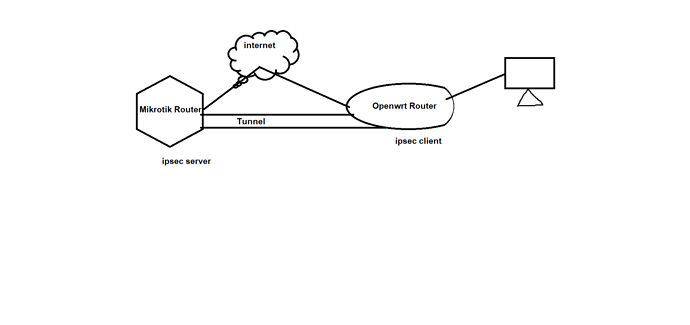
can anyone tell me how to setup ipsec site to site ipsec vpn by luci (GUI). i am unable to connect ipsec site to site vpn by CLI. here is the topology
here is my configuration
# cat /etc/config/ipsec
config 'ipsec'
list listen ''
config 'remote' 'nesecure'
option 'enabled' '1'
option 'gateway' 'IP Of SERVER'
option 'pre_shared_key' 'key'
option authentication_method 'psk'
option 'exchange_mode' 'main'
list 'p1_proposal' 'neprposal'
list 'tunnel' 'nesecure_lan'
config 'p1_proposal' 'neproposal'
option 'encryption_algorithm' 'des'
option 'hash_algorithm' 'sha1'
option 'dh_group' 'modp1024'
config 'tunnel' 'nesecure_lan'
option 'local_subnet' '192.168.2.0/24'
option 'remote_subnet' '10.234.152.176/28'
option 'p2_proposal' 'neproposal2'
config 'p2_proposal' 'neproposal2'
option 'pfs_group' '2'
option 'encryption_algorithm' 'des'
option 'authentication_algorithm' 'sha1'
# firewall config
# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option drop_invalid '1'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6 dongle wan2'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'ah'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option subnet '10.234.152.176/28'
option extra_src '-m policy --dir in --pol ipsec --proto esp'
option extra_dest '-m policy --dir out --pol ipsec --proto esp'
option mtu_fix '1'
config rule
option name 'Allow-IKE-input'
option src 'wan'
option proto 'udp'
option dest_port '500 4500'
option target 'ACCEPT'
config rule
option name 'Allow-ESP-input'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
config rule
option enabled '1'
option target 'ACCEPT'
option src 'wan'
option proto 'tcp'
option dest_port '80'
option name 'AllowWANWeb'