I want to set Firewall IP whitelist and port whitelist,but i faild……I can't even access the internet!
I am sure what I did wrong but my English is so bad。I can't read the document very well.
this is my command:
iptables -F
iptables -X
iptables -P INPUT DROP
iptables -P OUTPUT DROP
iptables -P FORWARD ACCEPT
iptables -A INPUT -s 192.168.1.1 -p all -j ACCEPT #my computer
iptables -A OUTPUT -s 192.168.1.1 -p all -j ACCEPT
iptables -A INPUT -s 192.168.0.1 -p all -j ACCEPT #Superior router
iptables -A OUTPUT -s 192.168.0.1 -p all -j ACCEPT
iptables -A INPUT -p udp --dport 50000:50003 -j ACCEPT
iptables -A INPUT -p udp --dport 3478 -j ACCEPT
iptables -A INPUT -p udp --dport 53 -j ACCEPT
iptables -A INPUT -p udp --dport 5353 -j ACCEPT
iptables -A INPUT -p udp --dport 443 -j ACCEPT
iptables -A INPUT -p udp --dport 27000:27036 -j ACCEPT
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -j ACCEPT
iptables -A INPUT -p tcp --dport 8080 -j ACCEPT
iptables -A INPUT -p tcp --dport 8000 -j ACCEPT
iptables -A INPUT -p tcp --dport 27014:27050 -j ACCEPT
iptables -A INPUT -p tcp --dport 50050 -j ACCEPT
iptables -A INPUT -p tcp --dport 50000 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -j ACCEPT
iptables -A OUTPUT -p udp --dport 50000:50003 -j ACCEPT
iptables -A OUTPUT -p udp --dport 3478 -j ACCEPT
iptables -A OUTPUT -p udp --dport 53 -j ACCEPT
iptables -A OUTPUT -p udp --dport 5353 -j ACCEPT
iptables -A OUTPUT -p udp --dport 443 -j ACCEPT
iptables -A OUTPUT -p udp --dport 27000:27036 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 80 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 443 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 8080 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 8000 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 27014:27050 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 50050 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 50000 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 22 -j ACCEPT
Why do you use raw IPTABLES rules rather than FW3 which is built-in OpenWrt?
It works by default and you can customize it to your needs.
I suspect you have not enabled NAT on the wan interface.
Reload the firewall service firewall restart and post here it's configuration
uci show firewall; cat /etc/firewall.user to check what needs to be fixed.
Please use "Preformatted text </>" for logs, scripts, configs and general console output.
![]()
Is the firewall connected to the internet? I doubt it's a good idea to allow traffic from the internet to the openwrt devices on all those ports. And why only allow DNS (port 53) over UDP and not TCP in the OUTPUT chain? You also don't allow established and related packages which means you won't accept responses. And then you allow all forwarded packets which is questionable.
@ask133, welcome to the community!
Why are you flushing the fw3 rules?
The default out-of-the-box rules should get you to the Internet.
Also, see: https://openwrt.org/docs/guide-user/firewall/firewall_configuration
In your case, it would be appropriate to use ipset with iptables, otherwise there would be a lot of rules
sorry,i know ,I will follow the community rules.I really don't know what it is FW3, I will try to look at this entry in the documentation.
OK……I made a mistake,thanks
Becasue,The first few rules are to allow 0.0.0.0 access the Router
Because I only know this, I used my previous experience with CentOS Linux to configure this router.
If a rule allowing 0.0.0.0 to access the router existed by default, I'd advise that you ensure that you flashed an official OpenWrt firmware to your device.
No such rule exists by default in a official build.
Well recall, your router (unlike most servers and desktops) has mutiple interfaces, and one generally runs masquerade (NAT) - commonly the WAN.
These rules are wrong. the same IP 192.168.1.1 is both
- the source IP of the input rule (the "other" my computer)
- the source IP of the output rule (this router, as all output traffic originates from the router itself)
One of those is wrong. Likely it should be destination in the output rule.
Same goes for the next rules for 192.168.0.1
Additionally, as you have no NATing rules and still likely have different subnets (if you are using the standard /24 prefix for 192.168.1.x or alternatively 192.168.0.x), it looks wrong to have
For anybody to understand those, you should describe what is the IP of this router, your PC and the "superior router". And how they are connected, same subnet or not.
And default for forward should likely be drop, not accept. And likely you want to allow all traffic originating in the router itself (= OUTPUT). To me it looks like you may have misunderstood the input, output and forward chains...
You should just take the default built-in firewall (fw3) and stick to it until you understand more closely the fundamentals of creating routable iptables firewall/NAT rules.
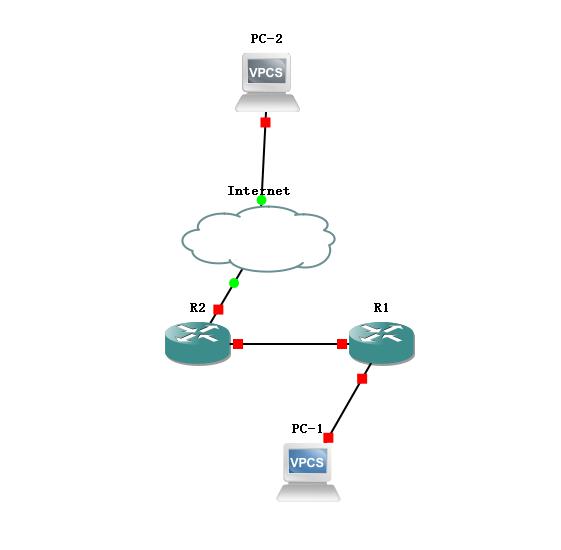
OK,I have a Simple topology……I'm not good at English,I have a problem with my description,sorry
The network below is my home network, and R2 is the openwrt router that needs to be configured with a firewall.
and R1 Subnet is 192.168.1.1/24,R2 Subnet is 192.168.0.1/24,Details of the device connected to R2 have been omitted.
I want PC1 only can use the port written above.
and the PC2 is I am at the school's computer(In the above description I wrote it as 192.168.1.1, which is indeed a big mistake.),I want this computer to be an exception can access PC1 all port.
Add traffic rules to allow the ports you wish PC-1 to access, from LAN to WAN. Then add one more rule at the end to DROP anything else.
Above the DROP ALL rule add a rule to allow from PC-1 to PC-2 all protocols.