It's the well-known problem: Android devices use hardcoded Google DNS 8.8.8.8, so local names cannot be resolved except the local name of the router itself. Other devices from lan can resolve names perfectly.
Proposal for solution from a post from 2018:
Therefore @eduperez suggest to use
iptables -t nat -A PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 192.168.1.1
iptables -t nat -A PREROUTING -i br-lan -p tcp --dport 53 -j DNAT --to 192.168.1.1
However this doesn't work for me. First of all, after reading why opkg upgrade is so awful I was hesitating to install anything at all. So I tried with Luci first:
First attempt:
I added a rule in Network > Firewall > NAT Rules and I will provide the resulting config via uci:
=> uci show firewall.@nat[0]
firewall.cfg0e93c8=nat
firewall.cfg0e93c8.name='DNSReroute'
firewall.cfg0e93c8.proto='tcp' 'udp'
firewall.cfg0e93c8.dest_port='53'
firewall.cfg0e93c8.target='SNAT'
firewall.cfg0e93c8.snat_ip='192.168.1.1'
firewall.cfg0e93c8.snat_port='53'
firewall.cfg0e93c8.device='br-lan'
firewall.cfg0e93c8.src='*'
There is no DNAT available, hence SNAT. I cleared the Google Chrome cache on my Android phone at chrome://net-internals/#dns and reconnected to the Wi-Fi with DHCP enabled.
Second attempt:
To try eduperez's approach I disabled what Luci did (firewall.cfg0e93c8.enabled='0') and installed iptables v1.8.7 (opkg install iptables). The options are different in this version. There is no --to option or a --to-destination like on https://linux.die.net/man/8/iptables. However --destination did work but I got the error
iptables v1.8.7 (nf_tables): Chain 'DNAT' does not exist
Third attempt:
Didn't work either:
=> nft list ruleset
table inet fw4 {
[...]
chain dstnat_lan {
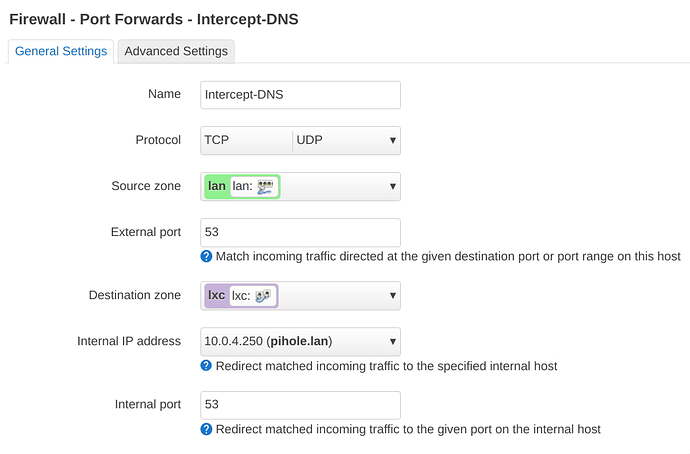
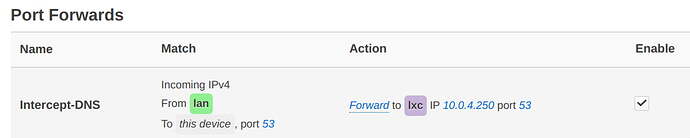
meta nfproto ipv4 tcp dport 53 counter packets 0 bytes 0 redirect to :53 comment "!fw4: Intercept-DNS"
meta nfproto ipv4 udp dport 53 counter packets 1 bytes 60 redirect to :53 comment "!fw4: Intercept-DNS"
}
[...]
=> uci show firewall.@redirect[0]
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].name='Intercept-DNS'
firewall.@redirect[0].src='lan'
firewall.@redirect[0].src_dport='53'
# Intercept IPv6 DNS traffic
=> uci set firewall.dns_int.family="any"
uci: Invalid argument
From here I don't know what to try next. I know some Linux but never understood iptables. I'm wondering if I should put wlan1 together with lan inside br-lan?
Additional information:
This is a very fresh installation of the current OpenWrt 22.03 on a Linksys MR8300. I did not change anything regarding br-lan, vlan or firewall. The device has three wlan devices and my phone is connected via wlan1:
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.path='platform/soc/a000000.wifi'
wireless.radio1.band='2g'
wireless.radio1.htmode='HT20'
wireless.radio1.channel='10'
wireless.radio1.country='DE'
wireless.radio1.cell_density='0'
wireless.default_radio1=wifi-iface
wireless.default_radio1.device='radio1'
wireless.default_radio1.network='lan'
wireless.default_radio1.mode='ap'
wireless.default_radio1.ssid='MyWiFi'
wireless.default_radio1.encryption='psk2'
wireless.default_radio1.key='redacted'
This might also be interesting:
=> uci show firewall.cfg0892bd
firewall.cfg0892bd=rule
firewall.cfg0892bd.name='Allow-DHCPv6'
firewall.cfg0892bd.src='wan'
firewall.cfg0892bd.proto='udp'
firewall.cfg0892bd.dest_port='546'
firewall.cfg0892bd.family='ipv6'
firewall.cfg0892bd.target='ACCEPT'
I'm aware that there are many threads regarding the same issue with Android devices and local DNS resolving. At this point I'm lost. Is there some kind of logfiles or "Wireshark" in OpenWrt that can use to watch the route of DNS traffic? Any help will be appreciated.