I have installed Jellyfin server on a old laptop, I want to access it from outside my home network, I tried forwarding port 8096 to the old laptop that I installed Jellyfin on, which is the default port for Jellyfin, but I cannot seem open that port. If I add the configuration to forward that port in LuCI, and do a nmap scan from my PC, of my public IP, port 8096 does not appear. What am I missing here?
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
Also, port scans from inside your network (even if you use the external IP address), are not reliable. Better use an external scan service, or some app on your phone.
Where I am putting ---- it means sensitive information or stuff that I'm unsure if I should share or not..
Output for cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '----'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr '----'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option password '----'
option ipv6 'auto'
option username '----'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
Output for cat /etc/config/firewall
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config redirect
option dest_port '8096'
option src 'wan'
option name 'Jellyfin-Server'
option src_dport '8096'
option target 'DNAT'
option dest_ip '192.168.1.240'
option dest 'lan'
list proto 'tcp'
Have you restarted firewall? Post also iptables-save -c -t nat
Output of iptables-save -c -t nat
# Generated by iptables-save v1.8.3 on Wed Mar 17 17:04:38 2021
*nat
:PREROUTING ACCEPT [2860:167017]
:INPUT ACCEPT [411:31851]
:OUTPUT ACCEPT [342:23638]
:POSTROUTING ACCEPT [2:236]
:MINIUPNPD - [0:0]
:MINIUPNPD-POSTROUTING - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[2860:167017] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[1029:109625] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[1831:57392] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[820:74181] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[818:73945] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.240/32 -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin-Server (reflection)" -j SNAT --to-source 192.168.1.1
[1029:109625] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d ----/32 -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin-Server (reflection)" -j DNAT --to-destination 192.168.1.240:8096
[818:73945] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[818:73945] -A zone_wan_postrouting -j MINIUPNPD-POSTROUTING
[818:73945] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[1831:57392] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 8096 -m comment --comment "!fw3: Jellyfin-Server" -j DNAT --to-destination 192.168.1.240:8096
[1831:57392] -A zone_wan_prerouting -j MINIUPNPD
COMMIT
# Completed on Wed Mar 17 17:04:38 2021
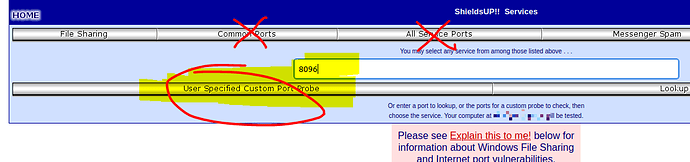
Try using an external scanning service instead. Two useful ones which I use regularly are grc.com's ShieldsUP! - https://www.grc.com/x/ne.dll?bh0bkyd2 - and pentest-tools.com's Online Port Scanner - https://pentest-tools.com/network-vulnerability-scanning/tcp-port-scanner-online-nmap
Be aware that grc.com takes a particularly histrionic approach with its reporting; it will scream an "OMG THE SKY IS FALLING!" failure report if it detects an open port. Of course, if you want that port to be open, then it's not a failure.
https://www.grc.com/x/ne.dll?bh0bkyd2 reports
THE EQUIPMENT AT THE TARGET IP ADDRESS
DID NOT RESPOND TO OUR UPnP PROBES!
and https://pentest-tools.com/network-vulnerability-scanning/tcp-port-scanner-online-nmap reports only one port open which is not for Jellyfin. When I do a nmap scan it shows 4-5 ports open.
By default, GRC scans the first 1024 ports. If you want to scan a higher port number, you need to specify the port manually.
As for pentest-tools, my apologies. I'd forgotten that the custom port number probe requires an account; it's not part of the free scan. Sorry about that.
Hmm. That's pretty conclusive.
By any chance, is there another router/firewall in the way? Maybe one which you don't have control over?
Does the IP address shown by ifconfig.co match the IP address shown on OpenWRT's status page?
Please check the firewall of host 192.168.1.240. If there is a firewall rule rejecting/dropping incoming traffic outside the lan, the port scanner should not show port 8096 as open.
The laptop that I'm hosting the server on had already installed UFW but I have allowed port 8096/tcp on it. Do I need to make some other changes as well?
There are no hits, nothing reached the firewall. Check your internet provider that they don't block something.
OpenWRT has an optional tcpdump package which may help here.
If you set tcpdump to listen to the WAN interface on port 8096, it should produce some output if you do another external port scan.
If it does, then you know the incoming traffic is reaching your router, and you can then direct your troubleshooting at your router and your internal network.
If it doesn't, then you know that the incoming traffic isn't reaching your router. Depending on the reason why not, it may be something you can correct, or it may be out of your control.
I have installed tcpdump, how to set it to listen to port 8096?
Identify which interface is your WAN interface. On my test installation here it's eth1 - yours may be different.
Then issue the command tcpdump -ni <interface> port 8096
Replace <interface> with the name of your WAN interface. For example, on mine it would be tcpdump -ni eth1 port 8096.
I ran this command, and tried connecting to my public IP with port 8096 in Jellyfin app from my phone over LTE, and it did not throw any output.
In which case, I can only refer you back to this post: How to port forward to my Jellyfin server? - #10 by iplaywithtoys
Also this post: How to port forward to my Jellyfin server? - #13 by trendy
If nothing's hitting your WAN interface, then there's a good chance that something else might be blocking the incoming traffic.
Do you have a public IP address on your WAN interface?
How to check that?