It seems to work. These are the config changes I ended up making. Do they seem sane?
To /etc/config/vpn-policy-config:
config policy
option interface 'wan'
option name 'Mysa Thermostats'
option src_addr 'AB:CD:8E:FG:B2:CA AB:CD:8E:FG:4A:3A'
option src_port '67 68 123 443 57959'
To /etc/config/firewall:
config redirect
option src 'wan'
option name 'MysaPortForwarding'
option src_dport '67 68 123 443 57959'
option target 'DNAT'
option dest_mac 'AB:CD:8E:FG:B2:CA AB:CD:8E:FG:4A:3A'
option dest 'lan'
One major problem I've noticed is that the changes made to the VPN Policy Routing cause an error when doing a fresh reboot of the router; I then have to go in and start the errored-out service, and then everything magically works fine. Obviously I can't be around to do this every time the router should happen to reboot.
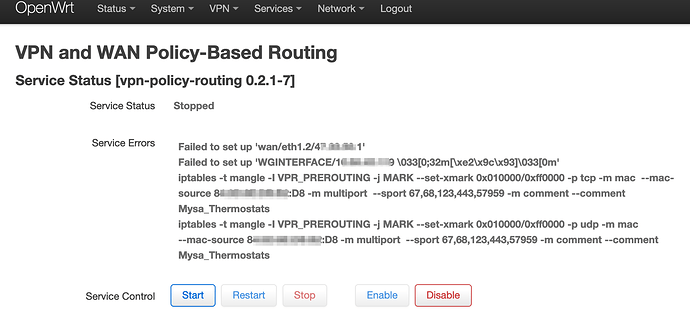
When I do a fresh reboot the router and go to the 'VPN Policy Routing' page in Luci, it shows this ugly error:
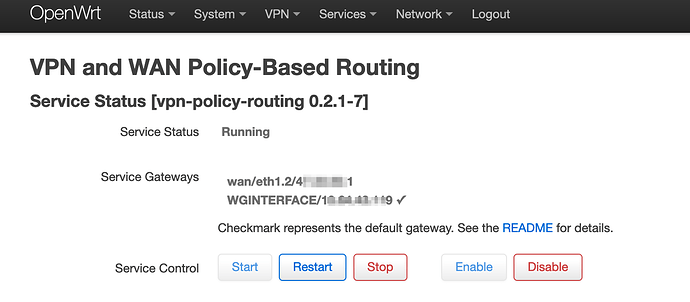
When I then click 'Start' to re-start the service, it works:
From a ssh session into the router, the command-line corroborates this behavior; before reloading vpn-policy-support, none of the Mysa rules are shown in the VPN_PREROUTING chain. After issuing the reload command, they appear. This appears in the output I'm attaching to the end of this message.
In other words, whenever the router reboots, I have to go in and manually (re)start the vpn-policy-support service, which has initially errored out. I wonder if it's a timing issue, since it takes some time to establish my wireguard vpn connection during a fresh router reboot.
What follows are the logfiles requested here, when reporting issues relating to vpn policy-based routing:
Contents of /etc/config/vpn-policy-routing
root@OpenWrt:~# cat /etc/config/vpn-policy-routing
config vpn-policy-routing 'config'
option verbosity '2'
option strict_enforcement '1'
option src_ipset '0'
option dest_ipset 'dnsmasq.ipset'
option ipv6_enabled '0'
list supported_interface ''
list ignored_interface 'vpnserver wgserver'
option boot_timeout '30'
option iptables_rule_option 'append'
option iprule_enabled '0'
option webui_enable_column '0'
option webui_protocol_column '0'
option webui_chain_column '0'
option webui_sorting '1'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list webui_supported_protocol 'all'
option enabled '1'
config include
option path '/etc/vpn-policy-routing.netflix.user'
option enabled '0'
config include
option path '/etc/vpn-policy-routing.aws.user'
option enabled '0'
config policy
option interface 'wan'
option name 'Mysa Thermostats'
option src_addr '8X:XX:XX:XX:XX:XX 8Y:YY:YY:YY:YY:YY'
option src_port '67 68 123 443 57959'
Contents of running vpn-policy-routing support -d (note there are no references to the Mysa devices here)
root@OpenWrt:/etc/init.d# ./vpn-policy-routing support -d
vpn-policy-routing 0.2.1-7 running on OpenWrt 19.07.1. WAN (IPv4): wan/dev/12.34.56.7.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default * 0.0.0.0 U 0 0 0 WGINTERFACE
12.34.56.7 * 255.255.255.0 U 0 0 0 eth1.2
89.01.23.456 047-033-050-001 255.255.255.255 UGH 0 0 0 eth1.2
192.168.99.0 * 255.255.255.0 U 0 0 0 br-lan
0: from all lookup local
32764: from all fwmark 0x20000/0xff0000 lookup 202
32765: from all fwmark 0x10000/0xff0000 lookup 201
32766: from all lookup main
32767: from all lookup default
IPv4 Table 201: default via 12.34.56.7 dev eth1.2
IPv4 Table 201 Rules:
32765: from all fwmark 0x10000/0xff0000 lookup 201
IPv4 Table 202: default via 10.64.43.119 dev WGINTERFACE
IPv4 Table 202 Rules:
32764: from all fwmark 0x20000/0xff0000 lookup 202
============================================================
IP Tables
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
VPR_INPUT all -- anywhere anywhere mark match 0x0/0xff0000
Chain FORWARD (policy ACCEPT)
target prot opt source destination
VPR_FORWARD all -- anywhere anywhere mark match 0x0/0xff0000
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN /* !fw3: Zone wan MTU fixing */ TCPMSS clamp to PMTU
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN /* !fw3: Zone WGZONE MTU fixing */ TCPMSS clamp to PMTU
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
VPR_OUTPUT all -- anywhere anywhere mark match 0x0/0xff0000
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
Chain VPR_FORWARD (1 references)
target prot opt source destination
Chain VPR_INPUT (1 references)
target prot opt source destination
Chain VPR_OUTPUT (1 references)
target prot opt source destination
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create WGINTERFACE hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]
Reloading and updated contents of vpn-policy-routing command (and now you will see they Mysa devices show up)
root@OpenWrt:/etc/init.d# ./vpn-policy-routing reload
Creating table 'wan/eth1.2/12.34.56.7' [✓]
Creating table 'WGINTERFACE/90.12.34.256' [✓]
Routing 'Mysa Thermostats' via wan [✓]
vpn-policy-routing 0.2.1-7 started with gateways:
wan/eth1.2/12.34.56.7
WGINTERFACE/90.12.34.256 [✓]
root@OpenWrt:/etc/init.d# ./vpn-policy-routing support
vpn-policy-routing 0.2.1-7 running on OpenWrt 19.07.1. WAN (IPv4): wan/dev/12.34.56.7.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
default * 0.0.0.0 U 0 0 0 WGINTERFACE
IPv4 Table 201: default via 12.34.56.7 dev eth1.2
IPv4 Table 201 Rules:
32763: from all fwmark 0x10000/0xff0000 lookup 201
IPv4 Table 202: default via 10.64.43.119 dev WGINTERFACE
IPv4 Table 202 Rules:
32762: from all fwmark 0x20000/0xff0000 lookup 202
============================================================
IP Tables PREROUTING
-N VPR_PREROUTING
-A VPR_PREROUTING -p udp -m mac --mac-source 88X:XX:XX:XX:XX:XX -m multiport --sports 67,68,123,443,57959 -m comment --comment Mysa_Thermostats -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -p tcp -m mac --mac-source 88X:XX:XX:XX:XX:XX -m multiport --sports 67,68,123,443,57959 -m comment --comment Mysa_Thermostats -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -p udp -m mac --mac-source 8Y:YY:YY:YY:YY:YY -m multiport --sports 67,68,123,443,57959 -m comment --comment Mysa_Thermostats -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -p tcp -m mac --mac-source 8Y:YY:YY:YY:YY:YY -m multiport --sports 67,68,123,443,57959 -m comment --comment Mysa_Thermostats -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -m set --match-set WGINTERFACE dst -c 0 0 -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan dst -c 0 0 -j MARK --set-xmark 0x10000/0xff0000
============================================================
IP Tables FORWARD
-N VPR_FORWARD
============================================================
IP Tables INPUT
-N VPR_INPUT
============================================================
IP Tables OUTPUT
-N VPR_OUTPUT
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create WGINTERFACE hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]
root@OpenWrt:/etc/init.d# ./vpn-policy-routing support -d
vpn-policy-routing 0.2.1-7 running on OpenWrt 19.07.1. WAN (IPv4): wan/dev/12.34.56.7.
============================================================
Dnsmasq version 2.80 Copyright (c) 2000-2018 Simon Kelley
Compile time options: IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth DNSSEC no-ID loop-detect inotify dumpfile
============================================================
Routes/IP Rules
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default * 0.0.0.0 U 0 0 0 WGINTERFACE
12.34.56.7 * 255.255.255.0 U 0 0 0 eth1.2
89.10.23.45 047-033-050-001 255.255.255.255 UGH 0 0 0 eth1.2
192.168.99.0 * 255.255.255.0 U 0 0 0 br-lan
0: from all lookup local
32762: from all fwmark 0x20000/0xff0000 lookup 202
32763: from all fwmark 0x10000/0xff0000 lookup 201
32766: from all lookup main
32767: from all lookup default
IPv4 Table 201: default via 47.33.50.1 dev eth1.2
IPv4 Table 201 Rules:
32763: from all fwmark 0x10000/0xff0000 lookup 201
IPv4 Table 202: default via 10.64.43.119 dev WGINTERFACE
IPv4 Table 202 Rules:
32762: from all fwmark 0x20000/0xff0000 lookup 202
============================================================
IP Tables
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
VPR_PREROUTING all -- anywhere anywhere mark match 0x0/0xff0000
Chain INPUT (policy ACCEPT)
target prot opt source destination
VPR_INPUT all -- anywhere anywhere mark match 0x0/0xff0000
Chain FORWARD (policy ACCEPT)
target prot opt source destination
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN /* !fw3: Zone wan MTU fixing */ TCPMSS clamp to PMTU
TCPMSS tcp -- anywhere anywhere tcp flags:SYN,RST/SYN /* !fw3: Zone WGZONE MTU fixing */ TCPMSS clamp to PMTU
VPR_FORWARD all -- anywhere anywhere mark match 0x0/0xff0000
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
VPR_OUTPUT all -- anywhere anywhere mark match 0x0/0xff0000
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
Chain VPR_FORWARD (1 references)
target prot opt source destination
Chain VPR_INPUT (1 references)
target prot opt source destination
Chain VPR_OUTPUT (1 references)
target prot opt source destination
Chain VPR_PREROUTING (1 references)
target prot opt source destination
MARK udp -- anywhere anywhere MAC 8X:XX:XX:XX:XX:XX multiport sports bootps,bootpc,ntp,https,57959 /* Mysa_Thermostats */ MARK xset 0x10000/0xff0000
MARK tcp -- anywhere anywhere MAC 8X:XX:XX:XX:XX:XX multiport sports bootps,bootpc,ntp,https,57959 /* Mysa_Thermostats */ MARK xset 0x10000/0xff0000
MARK udp -- anywhere anywhere MAC 8Y:YY:YY:YY:YY:YY multiport sports bootps,bootpc,ntp,https,57959 /* Mysa_Thermostats */ MARK xset 0x10000/0xff0000
MARK tcp -- anywhere anywhere MAC 8Y:YY:YY:YY:YY:YY multiport sports bootps,bootpc,ntp,https,57959 /* Mysa_Thermostats */ MARK xset 0x10000/0xff0000
MARK all -- anywhere anywhere match-set WGINTERFACE dst MARK xset 0x20000/0xff0000
MARK all -- anywhere anywhere match-set wan dst MARK xset 0x10000/0xff0000
============================================================
Current ipsets
create wan hash:net family inet hashsize 1024 maxelem 65536 comment
create WGINTERFACE hash:net family inet hashsize 1024 maxelem 65536 comment
============================================================
Your support details have been logged to '/var/vpn-policy-routing-support'. [✓]