Hi all,
I am trying really hard to solve issue of clients never get resolution from the router's DNS.
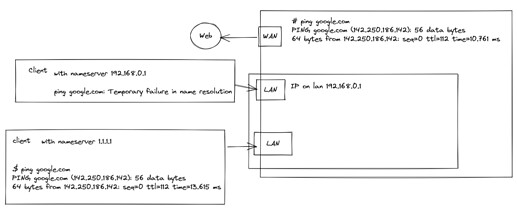
Simplified router schema
I'm very confused why the dnsmasq is not doing anything. The router can access and resolve using the ISP's DNS or custom ones.
But any client attempting to use 192.168.0.1:53 as a DNS server fails.
System info
| Hostname | frdm-nat |
|---|---|
| Model | FriendlyElec NanoPi R2S |
| Architecture | ARMv8 Processor rev 4 |
| Target Platform | rockchip/armv8 |
| Firmware Version | OpenWrt SNAPSHOT r17859-70c12d26ca / LuCI Master git-21.295.63883-63034c3 |
| Kernel Version | 5.10.75 |
# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Support-UDP-Traceroute'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='33434:33689'
firewall.@rule[9].proto='udp'
firewall.@rule[9].family='ipv4'
firewall.@rule[9].target='REJECT'
firewall.@rule[9].enabled='0'
firewall.@include[0]=include
It's empty
firewall.@include[0].path='/etc/firewall.user'
# uci show dhcp
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].ednspacket_max='1232'
dhcp.@dnsmasq[0].noresolv='1'
dhcp.@dnsmasq[0].cachesize='200'
dhcp.@dnsmasq[0].boguspriv='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].confdir='/tmp/dnsmasq.d'
dhcp.@dnsmasq[0].nonegcache='0'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv4='server'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_flags='managed-config' 'other-config'
dhcp.lan.dhcp_option='6,192.168.0.1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.wan.ra_flags='none'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
# opkg list-installed
adblock - 4.1.3-3
base-files - 1454-r17859-70c12d26ca
busybox - 1.34.1-1
ca-bundle - 20210119-1
cgi-io - 2021-09-08-98cef9dd-20
coreutils - 8.32-6
coreutils-sort - 8.32-6
dnsmasq - 2.86-3
dropbear - 2020.81-2
e2fsprogs - 1.45.6-2
firewall - 2021-08-14-40e5f6a2-1
fstools - 2021-08-25-e1b68111-2
fwtool - 2019-11-12-8f7fe925-1
getrandom - 2021-08-03-205defb5-2
ip6tables - 1.8.7-1
iptables - 1.8.7-1
jshn - 2021-08-19-d716ac4b-2
jsonfilter - 2018-02-04-c7e938d6-1
kernel - 5.10.75-1-264820106908f0aaa363581a4589efa7
kmod-crypto-hash - 5.10.75-1
kmod-gpio-button-hotplug - 5.10.75-3
kmod-ip6tables - 5.10.75-1
kmod-ipt-conntrack - 5.10.75-1
kmod-ipt-core - 5.10.75-1
kmod-ipt-nat - 5.10.75-1
kmod-ipt-offload - 5.10.75-1
kmod-lib-crc-ccitt - 5.10.75-1
kmod-mii - 5.10.75-1
kmod-nf-conntrack - 5.10.75-1
kmod-nf-conntrack6 - 5.10.75-1
kmod-nf-flow - 5.10.75-1
kmod-nf-ipt - 5.10.75-1
kmod-nf-ipt6 - 5.10.75-1
kmod-nf-nat - 5.10.75-1
kmod-nf-reject - 5.10.75-1
kmod-nf-reject6 - 5.10.75-1
kmod-nls-base - 5.10.75-1
kmod-ppp - 5.10.75-1
kmod-pppoe - 5.10.75-1
kmod-pppox - 5.10.75-1
kmod-slhc - 5.10.75-1
kmod-usb-core - 5.10.75-1
kmod-usb-net - 5.10.75-1
kmod-usb-net-rtl8152 - 5.10.75-1
libblkid1 - 2.37-1
libblobmsg-json20210819 - 2021-08-19-d716ac4b-2
libc - 1.2.2-3
libcomerr0 - 1.45.6-2
libext2fs2 - 1.45.6-2
libf2fs6 - 1.14.0-1
libgcc1 - 11.2.0-3
libip4tc2 - 1.8.7-1
libip6tc2 - 1.8.7-1
libiwinfo-data - 2021-07-11-a0a0e02d-1
libiwinfo-lua - 2021-07-11-a0a0e02d-1
libiwinfo20210430 - 2021-07-11-a0a0e02d-1
libjson-c5 - 0.15-2
libjson-script20210819 - 2021-08-19-d716ac4b-2
liblua5.1.5 - 5.1.5-9
liblucihttp-lua - 2021-06-11-3dc89af4-1
liblucihttp0 - 2021-06-11-3dc89af4-1
libnl-tiny1 - 2020-08-05-c291088f-2
libpthread - 1.2.2-3
librt - 1.2.2-3
libsmartcols1 - 2.37-1
libss2 - 1.45.6-2
libubox20210819 - 2021-08-19-d716ac4b-2
libubus-lua - 2021-06-30-4fc532c8-2
libubus20210630 - 2021-06-30-4fc532c8-2
libuci20130104 - 2021-10-22-f84f49f0-6
libuclient20201210 - 2021-05-14-6a6011df-1
libustream-wolfssl20201210 - 2020-12-10-68d09243-2
libuuid1 - 2.37-1
libwolfssl4.8.1.62348c2b - 4.8.1-stable-6
libwolfssl4.8.1.d8795272 - 4.8.1-stable-6
libxtables12 - 1.8.7-1
logd - 2021-08-03-205defb5-2
lua - 5.1.5-9
luci - git-20.074.84698-ead5e81
luci-app-adblock - git-21.282.00731-0c4dfc9
luci-app-firewall - git-21.243.76516-19c66ef
luci-app-opkg - git-21.079.58548-3bcbcbf
luci-base - git-21.295.63883-63034c3
luci-lib-base - git-20.232.39649-1f6dc29
luci-lib-ip - git-20.250.76529-62505bd
luci-lib-jsonc - git-19.317.29469-8da8f38
luci-lib-nixio - git-20.234.06894-c4a4e43
luci-mod-admin-full - git-19.253.48496-3f93650
luci-mod-network - git-21.298.68972-3165d5e
luci-mod-status - git-21.265.39600-b5464a3
luci-mod-system - git-21.292.76186-07569c5
luci-proto-ipv6 - git-21.148.48881-79947af
luci-proto-ppp - git-21.158.38888-88b9d84
luci-ssl - git-20.244.36115-e10f954
luci-theme-bootstrap - git-21.298.79142-37e40e0
mkf2fs - 1.14.0-1
mtd - 26
netifd - 2021-10-21-f78bdec2-1
odhcp6c - 2021-07-14-94adc8bb-18
odhcpd-ipv6only - 2021-08-11-01b4e604-1
openwrt-keyring - 2021-02-20-49283916-2
opkg - 2021-06-13-1bf042dd-3
partx-utils - 2.37-1
ppp - 2.4.9.git-2021-01-04-3
ppp-mod-pppoe - 2.4.9.git-2021-01-04-3
procd - 2021-10-22-1c36d3d0-1
procd-seccomp - 2021-10-22-1c36d3d0-1
procd-ujail - 2021-10-22-1c36d3d0-1
px5g-wolfssl - 3
rpcd - 2021-07-13-1fa35765-1
rpcd-mod-file - 2021-07-13-1fa35765-1
rpcd-mod-iwinfo - 2021-07-13-1fa35765-1
rpcd-mod-luci - 20210614
rpcd-mod-rrdns - 20170710
uboot-envtools - 2021.01-41
ubox - 2021-08-03-205defb5-2
ubus - 2021-06-30-4fc532c8-2
ubusd - 2021-06-30-4fc532c8-2
uci - 2021-10-22-f84f49f0-6
uclient-fetch - 2021-05-14-6a6011df-1
uhttpd - 2021-03-21-15346de8-3
uhttpd-mod-ubus - 2021-03-21-15346de8-3
urandom-seed - 3
urngd - 2020-01-21-c7f7b6b6-1
usign - 2020-05-23-f1f65026-1
note: adblock is installed but it does not matter if it's enabled or not. The result is the same no DNS server resolution or caching happening. After I get this dnsmasq fixed I will use the LAN zone interceptor on port 53 to use it.
# cat /etc/resolv.conf
# Interface wan
nameserver 1.1.1.1
nameserver 1.0.0.1
# cat /etc/config/network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix '<redacted>'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan'
config device 'lan_eth1_dev'
option name 'eth1'
option macaddr '<redacted>'
config interface 'wan'
option proto 'dhcp'
option device 'eth0'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config device 'wan_eth0_dev'
option name 'eth0'
option macaddr '<redacted>'
config interface 'wan6'
option proto 'dhcpv6'
option device 'eth0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
Any ideas? I've already attempted so many things but without any luck.  It's like a miss a key knowledge about how to use basic LAN DNS server on the outer.
It's like a miss a key knowledge about how to use basic LAN DNS server on the outer.
 You saved me.
You saved me.