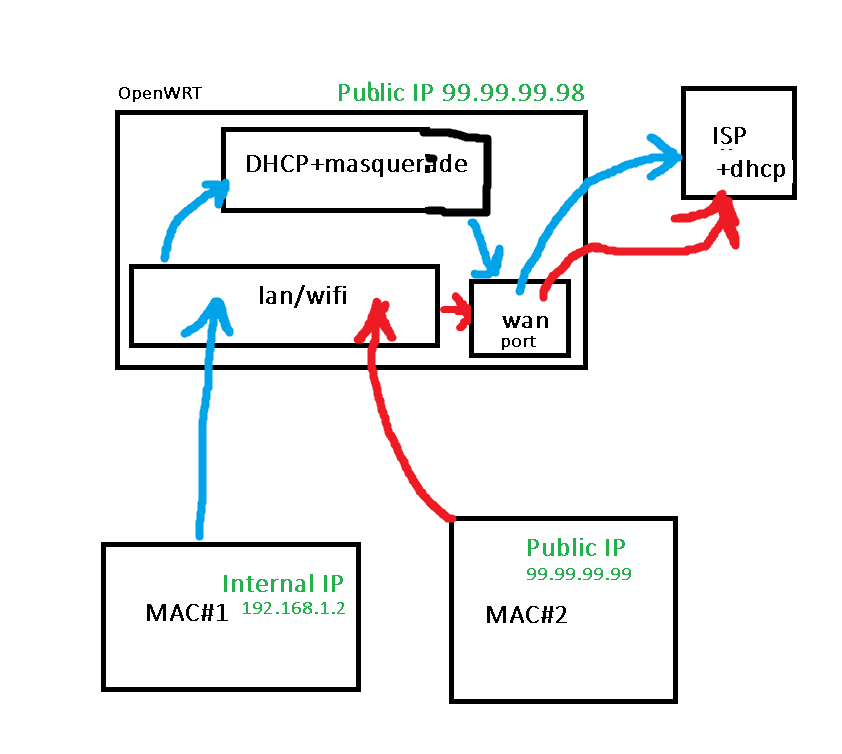
Is there any way by OpenWRT to have DHCP Client enabled for wan port, DHCP server for lan ports/wifi but by client MAC's to decide if traffic should go by NAT way or by transparent bridge? Depends on client MAC client will get IP from router and traffic through with masquerade or for other MAC's it will be white/external IP which got by dhcp outside wan port from ISP and transparent traffic.
What kind of transparent bridge are you talking about? For IPv4, most ISP's only issue a single address to each subscriber (for residential accounts). In those cases (which covers the vast majority of ISPs, at least those that issue public IPs; it may be different for CG-NAT based ISPs), you need router with NAT masquerading enabled in order to have more than one device online, and you can't have any other devices that are not behind the router online because there isn't another IP address available. Therefore, if you had a 'transparent bridge' setup, the devices assigned to said bridge would have no IPv4 connectivity at all. (this applies unless you do actually get multiple IPv4 addresses).
IPv6 is a different story, of course, but then you're not usually talking about masquerading.
I can have several public IP's. Diagram is updated.
As long as this is the case (from the ISP), you can create a bridge, but you can't selectively steer hosts from behind the router. They would need to request a DHCP lease directly from the ISP, and would therefore not be on the same network as your other devices. The simple way to think of this is that you would put a switch between your ISP connection and your router. With most routers, you could even use the built-in switch to achieve the same goal... but the port(s) that connect to the wan via the bridge would not be serviced at all by your router.
Alternatively, you could theoretically setup a dual wan on your router and then use policy based routing to steer the hosts on your network to send traffic through one or the other of the wan connections (i.e. WAN IPs).
EDIT: With a more sophisticated managed switch in front of the router, you could use MAC based VLAN approaches to get the behavior you seem to be describing, but this would still necessarily mean that those hosts would not be part of your main network. OTOH, with VLANs, if those hosts are VLAN aware, you could also provide them a LAN connection... but this could be risky since they also have a direct connection to the internet, so any vulnerability in your hosts could effectively bridge the internet to your trusted lan.
I had try to simplify the task. To use lan ports and wifi, to split kinda "physically" areas.
I already had try kmod-trelay for wifi. Wifi with transparent bridge and public IP is working with it.
But once i start trelay then NAT clients have no internet.
And another way had try to use inbuild bridge methods.
Had bridged wifi to wan but after wifi connected over transparent bridge and after like a minute NAT clients are going offline. Once i stop bridge interface(wifi-wan) then NAT clients up.
I'm not sure that I'm following your description there, but regardless, another question for you:
- do you really want your host to be directly connected to the internet/public IP? This is generally not recommended for most normal hosts -- it is almost always better to have a firewall appliance (such as a router/firewall like OpenWrt or others) protecting the host from unsolicited connections on the internet. )Of course, if you're setting up an additional router/firewall, obviously it's fine to connect it to the internet directly, provided it's properly configured.)
yes
(Post must be at least 10 characters ![]() )
)
I think that the best way for you to achieve the goal is to use a switch in front of the router. As I said earlier, you'd do this on a physical port basis, or you could use a managed switch to handle MAC based VLANs which would connect them to the ISP connection.
One more physical device? Task is to use one OpenWRT device without one more external physical device....
two ethernet cables from ISP router to my Openwrt device? I don't have this way...
About vlan i think i have some limitations about that my wifi devices can't use vlan tag....(if i have right vlan technology understanding)
ok... so you can split some of the ports of your router to be connected to the wan instead of the lan.
I can advise about specifics with the network file:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
This could be done with one, just as it is. But you won't get a true transparent bridge in this scenario. You can create another wan interface and it will be able to get another IP. Then, you can use mwan3 or PBR to steer traffic accordingly. Your hosts on your network would still have RFC1918 addresses and be behind the firewall (they wouldn't be truly exposed to the internet), but they would 'appear' to be using the 2nd wan if you wanted.
VLANs are really a wired concept only (802.1q). But understanding VLANs isn't necessarily a requirement here unless you'd be setting up a managed switch in front of your router.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd5:d25d:2f39::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'XX:XX:XX:XX:XX:XX'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
- default config.
Had try to use mwan3 and kmod-macvlan but failed by first try...
I don't know the mapping of the physical ports on your device to the logical ports shown below... but the change you want is really simple...
note that VLAN 1 has ports 2-5, and 0t... 0t is the processor, the others are logical lan ports. So we need to remove one of the lan ports and put it under VLAN 2 (which is used your your wan, along with logical port 1 which almost certainly translates to the physical WAN port)... I'll use logical port 2 here... you may choose to use a different port depending on how this physically maps to the ports on your device.
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 2 0t'
That's all you need to do.
but what about wifi?
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option network 'wan'
is not helping to get public IP by dhcp
WiFi should never be associated with wan under normal circucmstances.
How many IPs does your ISP grant? Do you really want wifi to be directly connected to the wan?
If you want to do this, it will require a bit of rethinking... it's highly unusual, so I'm not going to work thorugh the process unless you can provide some clarification or confirmation first.
several
yes
Change the network configuration like this.
config device
option name 'br-wan'
option type 'bridge'
list ports 'eth0.2'
config interface 'wan'
option device 'br-wan'
option proto 'dhcp'
config interface 'wan6'
option device 'br-wan'
option proto 'dhcpv6'
Create a dedicated wifi network for this purpose, and if you're not behind CGNAT, make sure the wireless devices that will be using it have their own reliable firewalls.
I would say that even if you are behind cgnat, your devices should all have robust local firewalls enabled. Even though cgnat networks won’t be as vulnerable as the open internet with public ips, it still should be treated as a hostile network (much like public WiFi at a cafe or hotel).
But beyond that, what @pavelgl recommended is right on point with the bridge.
by this way no public IP for the router, no public IP for wifi device.
/etc/config/wireless
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option network 'wan'
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd5:d25d:2f39::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr 'xxx'
config interface 'wan'
option proto 'dhcp'
option type 'bridge'
option device 'br-wan'
config interface 'wan6'
option proto 'dhcpv6'
option type 'bridge'
option device 'br-wan'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 3 4 5'
option vid '1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 1'
config device
option type 'bridge'
option name 'br-wan'
list ports 'eth0.2'
Remove the bridge option from both interface sections and restart the network service.