dunnos
September 23, 2023, 4:30am
1
How to forward a port without using "Masquerading"?
the "Port Forwards" section for some reason does not want to work without the "Masquerading" functions
In the keenetic router, the original "client IP address is saved instead of being replaced with 192.168.1.1".
Why is there such a problem with saving the original IP address in openwrt?
Chose tcp as protocol and you're be able to select port 22.
dunnos
September 23, 2023, 9:06am
8
When I turn on port 443 forwarding, it stops accessing all sites, that is, I lose the ability to use the browser normally.
Finn
September 23, 2023, 9:30am
9
Hi.
grrr2
September 23, 2023, 9:53am
10
what you want to achieve actually?
2 Likes
dunnos
September 23, 2023, 10:17am
11
If I enable this feature, then I will not be able to use the browser (I will not be able to log in to other sites except local ones)
dunnos
September 23, 2023, 10:19am
12
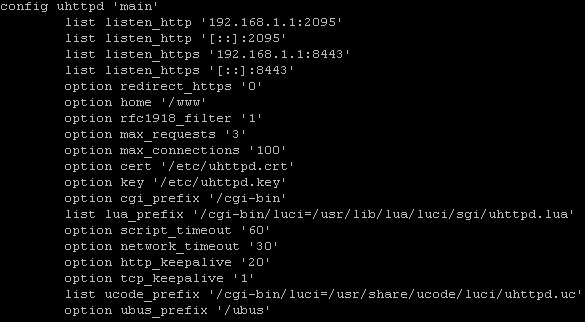
192.168.1.168 - This is the address of the virtual machine, A website using ports 80/443 is running on the virtual machine, some kind of conflict with openwrt turns out for some reason, although I moved "luci" to 192.168.1.1:2095/8443 instead of 0.0.0.0:80/443.
Finn
September 23, 2023, 10:51am
13
As grrr2 is asking - from where are You trying to access Your webpage ?
Is it from the internet or from another Pc on same network or..
1 Like
krazeh
September 23, 2023, 11:01am
14
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/firewall
2 Likes
This thread might be relevant:
How to forward a port without using "Masquerading"?
[ScreenShot_20230923072837]
the "Port Forwards" section for some reason does not want to work without the "Masquerading" functions
In the keenetic router, the original "client IP address is saved instead of being replaced with 192.168.1.1".
Why is there such a problem with saving the original IP address in openwrt?
dunnos
September 23, 2023, 11:31am
16
From the external Internet, I'm trying to access the site located on port 80/443, about the IP address: the address is white, so the provider does not block anything from its side.
dunnos
September 23, 2023, 11:38am
17
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'lan'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
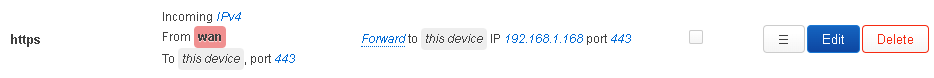
config redirect
option dest 'lan'
option target 'DNAT'
option name 'ssh'
option src 'wan'
option src_dport '23'
option dest_ip '192.168.1.168'
option dest_port '22'
list proto 'tcp'
config nat
option name 'SNAT'
option src '*'
option target 'SNAT'
option snat_ip 'wan ip'
list proto 'all'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DB'
list proto 'tcp'
option src 'wan'
option src_dport '3306'
option dest_ip '192.168.1.168'
option dest_port '3306'
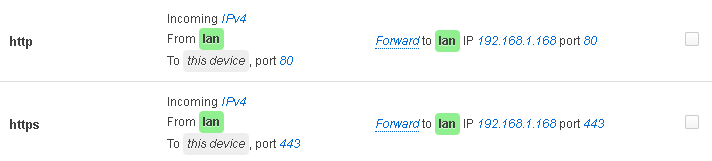
config redirect
option target 'DNAT'
option name 'http'
option src 'lan'
option src_dport '80'
option dest_ip '192.168.1.168'
option dest_port '80'
option dest 'lan'
option enabled '0'
config redirect
option target 'DNAT'
option name 'https'
option src 'lan'
option src_dport '443'
option dest_ip '192.168.1.168'
option dest_port '443'
option dest 'lan'
option enabled '0'
krazeh
September 23, 2023, 11:41am
18
option src for both of these rules should be wan, not lan. And you can leave uhttpd on the default ports.
2 Likes
dunnos
September 23, 2023, 11:50am
19
config redirect
option target 'DNAT'
option name 'http'
option src 'wan'
option src_dport '80'
option dest_ip '192.168.1.168'
option dest_port '80'
option dest 'lan'
option enabled '0'
config redirect
option target 'DNAT'
option name 'https'
option src 'wan'
option src_dport '443'
option dest_ip '192.168.1.168'
option dest_port '443'
option dest 'lan'
option enabled '0'
In this way?
This is a major issue:
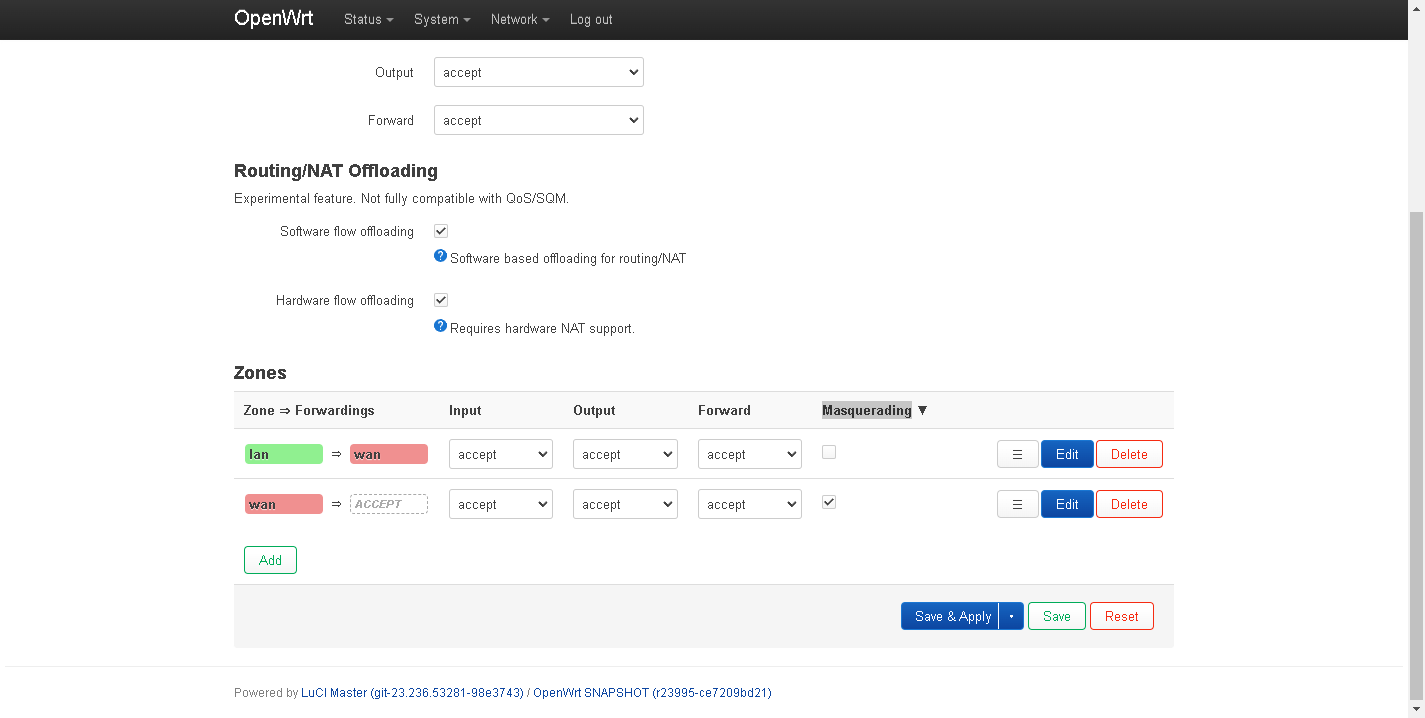
Remove the lan network from the wan firewall zone.
Also, masquerading must be enabled on the wan zone in most cases.
3 Likes
dunnos
September 23, 2023, 11:56am
21
if enable "Masquerading" then the players on the server will have the ip address 192.168.1.1, so "Masquerading" is not suitable.
Ok… so does your upstream router have a static route defined?
1 Like