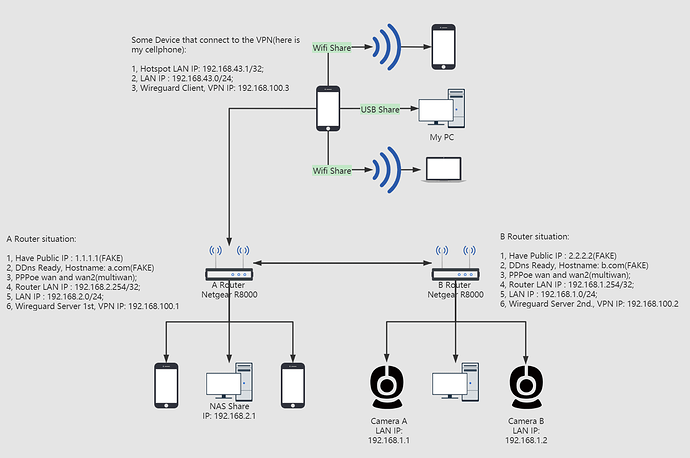
My Network Topology
My Purples
- No matter where I am, as long as the devices connected to the VPN, they can access NAS(behind Router A) and Cameras(behind Router B);
- No need to install wireguard on the LAN device, and it can be directly accessed by LAN IP on the Client side. For example, using my cellphone, open foobar2000, type in the LAN IP(192.168.2.1) + Port , it can directly access the foobar2000 UPNP service on the NAS. In short, use the least installed wireguard to access all the devices behind routers.
My Network and Firewall Setting
- Here is network config :
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'aaaa:bbbb:cccc::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.254'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr 'aa:bb:cc:dd:ee:ff'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'oo:pp:qq:xx:yy:zz'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option password 'hereismypppoepswd'
option ipv6 'auto'
option username 'hereismypppoeaccount'
option metric '40'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 5t'
config device 'veth0'
option name 'veth0'
option ifname 'eth0.2'
option type 'macvlan'
config interface 'wan2'
option ifname 'veth0'
option proto 'pppoe'
option password 'hereismypppoepswd'
option metric '41'
option username 'hereismypppoeaccount'
option ipv6 '0'
option delegate '0'
config interface 'wg0'
option proto 'wireguard'
option private_key 'hereismywireguardserverprivatekey'
option mtu '1300'
option delegate '0'
option listen_port '10240'
list addresses '192.168.100.1/24'
config wireguard_wg0
option public_key 'hereismypcpublickey-usingfortest'
option persistent_keepalive '25'
option route_allowed_ips '1'
option description 'MyPc'
list allowed_ips '192.168.100.2/32'
config wireguard_wg0
option public_key 'hereismycellphone'
option description 'MyCellphone'
option route_allowed_ips '1'
option persistent_keepalive '25'
list allowed_ips '192.168.100.3/32'
config route
option gateway '192.168.2.254'
option netmask '255.255.255.0'
option interface 'wg0'
option target '192.168.100.0/24'
- Here is the firewall config :
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg0'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan2'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'ss_rules'
option path '/etc/firewall.ss-rules'
option reload '1'
config redirect
option dest_port '3389'
option src 'wan'
option name 'remote desktop'
option src_dport '00000'
option target 'DNAT'
option dest_ip '192.168.2.1'
option dest 'lan'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option proto 'udp'
option target 'ACCEPT'
option family 'ipv4'
option dest_port '10240'
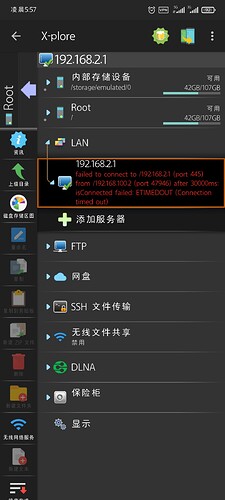
Current situation
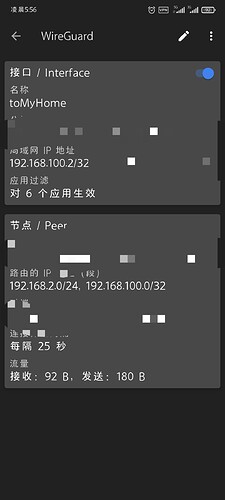
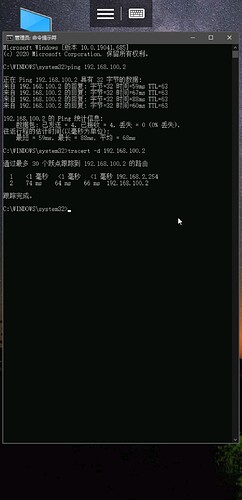
I can ping the Router A (either 192.168.2.254 or 192.168.100.1) with my PC, Here's my PC wireguard config:
[Interface]
PrivateKey = hereismypcprivatekey
Address = 192.168.100.4/32
MTU = 1300
[Peer]
PublicKey = hereismyrouterApublickey
AllowedIPs = 192.168.100.0/32, 192.168.2.0/24
Endpoint = a.com:port
PersistentKeepalive = 25
HOPE FOR A HELP!!