No, I just wanted to know how this configuration would look on stock firmware. So far as I can tell gl.inet builds official firmware, and then adds a different management UI on top of it.
Apparently that's too much to ask. But whatever, I don't want to argue with you about whether or not it's supported. All I was hoping for was just to be told "here's what it would look like on the stock firmware", not to get an argument about whether or not my firmware could be supported.
I've raised it with gl.inet previously - I came here because their forum wasn't quick enough in getting me any guidance. I've now taken it directly to their support e-mail. But this has left a really bad taste in my mouth for this project.
Like I said, I'm no stranger to doing open source support. I've been doing it myself for the openSUSE project for over 20 years. If someone comes into our forums and asks about an old version or a downstream distribution, we still try to help, because there's enough knowledge around still, and enough commonality that we can help. We will advise that they should try running a current version, but we won't generally tell them to 'pound sand'.
I know that what I'm asking for is not a typical request, but I also know that the general spirit of open source communities is to provide guidance and assistance to the extent that it is possible. And in my experience, the type of question that I'm asking here isn't outside that realm of expectation. It's a firewall/routing question. Get packets from A to B.
I'm not trying to get some sort of proprietary driver working (like their multi-wan driver). I'm not asking for help fixing a CORS issue in their nginx reverse proxy that's installed on the router.
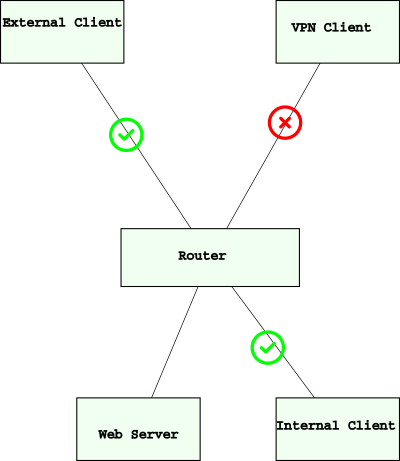
I"m asking for help with a simple routing question. That's it.
This is likely a simple network routing/configuration issue, and I simply don't know how to get the same result that NAT loopback gives me going from LAN-WAN-LAN when going from VPN-WAN-LAN.
I didn't come here looking for a fight or an argument. Really, truly, I did not. I came here because this community has been helpful to me in the past.
You don't know that your answers aren't meaningful - you're just assuming that the gl.inet firmware varies wildly from the official project (even though the build string says that it IS the official project's code and not their own fork, as far as I can see - the fact that the commit hash is valid in the openwrt source tree on github points very strongly that at least the core functionality is from the offical 21.03 build).
But you just saw "gl.inet firmware" and said "nope, sorry, can't help you there" without even considering that my question is a simple routing configuration question. You assumed that an answer about how it should have worked with iptables on that release would not be meaningful to me. Now, granted, you don't know that I've got decades of experience working with networking equipment and operating systems, and that, if pointed in the right direction, I'll probably find the answer I'm looking for.
No offer to say "hey, while you can run official code here, let's look at your zone configurations, your firewall configurations, and see if we can get you pointed in the right direction."
I'm not asking for surgery here. I'm asking for a pointer in the right direction.
But what I've learned that the people who are "leaders" and "gurus" here would rather argue about whether or not something is supported or not than just provide a simple answer to what ultimately is probably a simple question and I'm just vapor-locked on what the next step is to fix it.