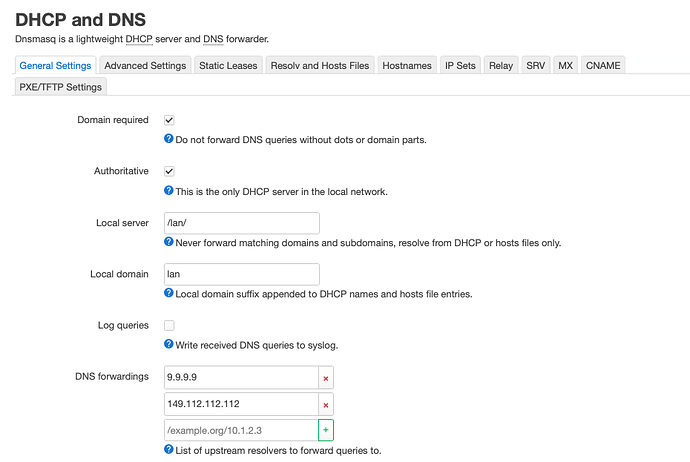
Hi, I've configurated stubby and it works correctly with cloudflare.9.9.9.9 and 149.112.112.112
config stubby 'global'
option manual '0'
option trigger 'wan'
# option triggerdelay '2'
list dns_transport 'GETDNS_TRANSPORT_TLS'
option tls_authentication '1'
option tls_query_padding_blocksize '128'
# option tls_connection_retries '2'
# option tls_backoff_time '3600'
# option timeout '5000'
# option dnssec_return_status '0'
option appdata_dir '/var/lib/stubby'
# option trust_anchors_backoff_time 2500
# option dnssec_trust_anchors '/var/lib/stubby/getdns-root.key'
option edns_client_subnet_private '1'
option idle_timeout '10000'
option round_robin_upstreams '1'
list listen_address '127.0.0.1@5453'
list listen_address '0::1@5453'
# option log_level '7'
# option command_line_arguments ''
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
# Upstream resolvers are specified using 'resolver' sections.
config resolver
option address '2606:4700:4700::1111'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '2606:4700:4700::1001'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '1.1.1.1'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '1.0.0.1'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
I configured DHCP and DNS in this way without stubby and it seems to work in the same way.
frollic
September 3, 2023, 8:42am
3
it's not encrypted that way ...
https-dns-proxy would probably be easier to configure, than stubby.
1 Like
AndrewZ
September 3, 2023, 8:48am
4
You can take the necessary data from the source:
####### IPv6 addresses ######
### Test servers ###
# The getdnsapi.net server
- address_data: 2a04:b900:0:100::38
tls_auth_name: "getdnsapi.net"
tls_pubkey_pinset:
- digest: "sha256"
value: foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9Q=
############################ OPTIONAL UPSTREAMS ###############################
####### IPv4 addresses ######
### Anycast services ###
## Quad 9 'secure' service - Filters, does DNSSEC, doesn't send ECS
# - address_data: 9.9.9.9
# tls_auth_name: "dns.quad9.net"
# - address_data: 149.112.112.112
# tls_auth_name: "dns.quad9.net"
## Quad 9 'secure w/ECS' service - Filters, does DNSSEC, DOES send ECS
## See the entry for `edns_client_subnet_private` for more details on ECS
# - address_data: 9.9.9.11
1 Like
Quad9 is quite slow for me, but if you like it (for example, unlike others, it doesn't pass EDNS Client Subnet)...
/etc/config/stubby:
config stubby 'global'
option manual '0'
option trigger 'wan'
option tls_authentication '1'
option tls_cipher_list 'EECDH+CHACHA20'
option tls_ciphersuites 'TLS_CHACHA20_POLY1305_SHA256'
option tls_min_version '1.2'
option tls_max_version '1.3'
list dns_transport 'GETDNS_TRANSPORT_TLS'
list listen_address '127.0.0.1@5453'
list listen_address '0::1@5453'
option tls_query_padding_blocksize '256'
config resolver
option address '9.9.9.9'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '149.112.112.112'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '2620:fe::9'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '2620:fe::fe'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
/etc/config/dhcp (add to your existing one in respective section):
config dnsmasq
...
option noresolv '1'
list server '127.0.0.1#5453'
list server '::1#5453'
/etc/config/network (add to your existing one in respective section):
config interface 'wan'
...
option peerdns '0'
list dns '127.0.0.1'
config interface 'wan6'
...
option peerdns '0'
list dns '::1'
All comes from official README (extended to support IPv6).
1 Like
Thank you. Do you think it’s better cloudflare?
1 Like
Try it yourself. Quad9 doesn't have servers in my country. But AFAIK it is the only one who doesn't share ECS. Cloudflare used to do the same but now the DO share it (I stress it because there are many places where people claim that it doesn't share).
It didn't worked for me.
config stubby 'global'
option manual '0'
option trigger 'wan'
# option triggerdelay '2'
list dns_transport 'GETDNS_TRANSPORT_TLS'
option tls_authentication '1'
option tls_query_padding_blocksize '128'
# option tls_connection_retries '2'
# option tls_backoff_time '3600'
# option timeout '5000'
# option dnssec_return_status '0'
option appdata_dir '/var/lib/stubby'
# option trust_anchors_backoff_time 2500
# option dnssec_trust_anchors '/var/lib/stubby/getdns-root.key'
option edns_client_subnet_private '1'
option idle_timeout '10000'
option round_robin_upstreams '1'
list listen_address '127.0.0.1@5453'
list listen_address '0::1@5453'
# option log_level '7'
# option command_line_arguments ''
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
# Upstream resolvers are specified using 'resolver' sections.
config resolver
option address '2606:4700:4700::1111'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '2606:4700:4700::1001'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '1.1.1.1'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '1.0.0.1'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '9.9.9.9'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '149.112.112.112'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '2620:fe::9'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '2620:fe::fe'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
I changed it.
config stubby 'global'
option manual '0'
option trigger 'wan'
# option triggerdelay '2'
list dns_transport 'GETDNS_TRANSPORT_TLS'
option tls_authentication '1'
option tls_query_padding_blocksize '128'
# option tls_connection_retries '2'
# option tls_backoff_time '3600'
# option timeout '5000'
# option dnssec_return_status '0'
option appdata_dir '/var/lib/stubby'
# option trust_anchors_backoff_time 2500
# option dnssec_trust_anchors '/var/lib/stubby/getdns-root.key'
option edns_client_subnet_private '1'
option idle_timeout '10000'
option round_robin_upstreams '1'
list listen_address '127.0.0.1@5453'
list listen_address '0::1@5453'
# option log_level '7'
# option command_line_arguments ''
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
# Upstream resolvers are specified using 'resolver' sections.
config resolver
option address '2606:4700:4700::1111'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '1.1.1.1'
option tls_auth_name 'cloudflare-dns.com'
# option tls_port 853
# list spki 'sha256/yioEpqeR4WtDwE9YxNVnCEkTxIjx6EEIwFSQW+lJsbc='
# option tls_cipher_list 'EECDH+AESGCM:EECDH+CHACHA20'
# option tls_ciphersuites 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256'
# option tls_min_version '1.2'
# option tls_max_version '1.3'
config resolver
option address '9.9.9.9'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
config resolver
option address '2620:fe::fe'
option tls_auth_name 'dns.quad9.net'
list spki 'sha256//SlsviBkb05Y/8XiKF9+CZsgCtrqPQk5bh47o0R3/Cg='
AndrewZ
September 3, 2023, 5:12pm
10
If you have IPv6 upstream connectivity then you can keep IPv6 resolver(s) only. If you're limited to IPv4, then it is safe to delete IPv6 resolvers.
1 Like
Thank you. I’ll delete them.
It definitely works on dual stack. Just comment out IPv6 related stuff. What if your provider rolls out IPv6
Dual stack installations should leave both active. Who will serve DNSv6 requests if no servers running? Ever wondered why many IPv6 tests fail to detect IPv6? Broken DNS is the reason.
system
September 13, 2023, 8:27pm
14
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.