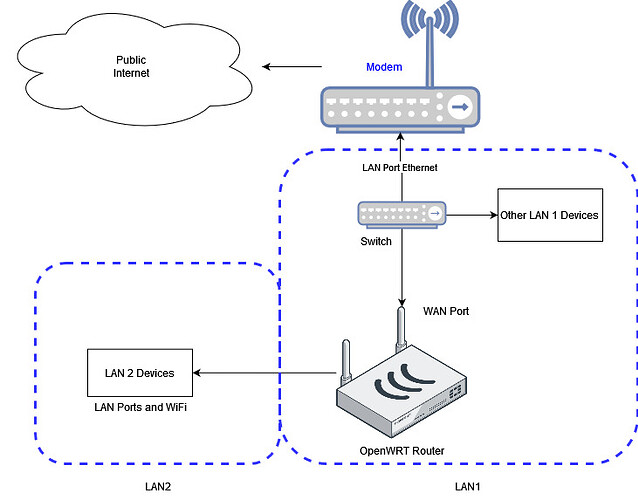
In this case, you should probably connect directly rather than via the VPS.
As long as you have a public IP (even if it is dynamic), direct connections are easy... just use a ddns service.
This is reasonable... but, it's more complex, and therefore maybe a good thing to play with after you've got a setup working in the direct connection method.
However, right off the bat... I see a few things happening.
remove the all of the lines below the list address (keep that line). DNS settings on this interface won't actually do anything.
Next, remove the /8 from the address. Just make it 10.8.0.3 pure and simple.
From the peer config, it appears that you are tunneling all your traffic through the VPS. Is that your goal? If you're simply looking for remote access, your current config is not the most efficient method. But if you intend to prevent your ISP (and maybe government) from observing the traffic between your network and the VPS, obviously this will do what you want.
Next, let's talk firewall...
Because the WG0 interfcae is currently associated with the wan zone, there will be no inbound connecftion capability in the default config, and this is by design (and I'd recommend that you don't alter the wan zone behaviors). remove the WG0 network from the wan zone and create a new zone for your WG network.
Now, assuming you control the VPS and it is considered trusted, you can make the VPN zone work like this:
config zone 'vpn'
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'WG0'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
Reboot your router and try again. If that doesn't work, we'll have to look at the VPS and the remote peer.