Hi There!
I would like to use openwrt not as usual router and I'm not comfortable with the Firewall zone system.
I wish to understand exactly what I'm doing here, so explanations are welcome 
First, let me explain what I want to do.
I am using a gl.inet device with USB, 2 Ethernet (eth0, eth1) and wifi (not used).
-USB is used with a LTE modem (interface "ncm wwan", Firewall Zone WWAN).
-eth0 is attached to firewall zone LAN
-eth1 is attached to firewall zone WAN (It will not be exactly used as WAN but will be connected to WAN port of my main router).
I would like to use this openwrt device as a LTE gateway connected on WAN port of my main router.
I want to use eth0 LAN as a maintenance access and this port will be connected to my LAN as 192.168.1.253.
I will use this to access luci and manage the gateway ( I assume it's possible to access also from WAN through my router, but I prefer do this on LAN side: it's also an opportunity to learn how to isolate Zone on openwrt).
eth1 will be connected to WAN port of my router and will be a gateway to the LTE modem.
So, now let's come to the firewall settings:
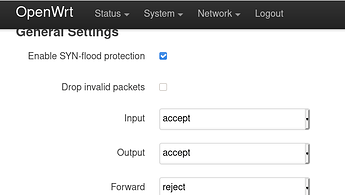
It's not clear to me what's the meaning of "input, output, forward" and also this masquerading check box ?
Here:
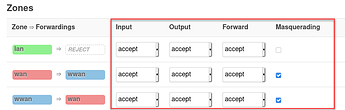
And Here:
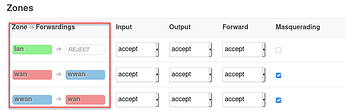
Then, it's also not clear how work this "zone forwarding" area:
Explanations welcome ! 
At the end, I wish to have a path WAN<->WWAN, but LAN side shall be fully isolated from WAN and WWAN side. LAN side shall be a dead-end except for Luci/SSH from LAN.