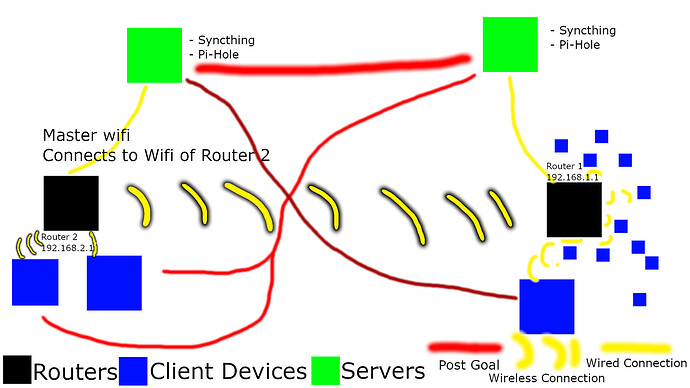
Hello,
I had been trying to figure out if there is a way to achieve this without using a bridge, while making sure both routers use their own dhcp server, aren't making anything available to the internet, and while being on a separate subnet. I am trying to make it so I can access the syncthing and pihole admin interfaces while being connected to router 2 and viceversa.
Is this possible?
Router 2 is an openwrt router that I can carry anywhere tunnels all traffic through my wireguard vpn. It is directly connected to my computer and provides a wireless signal to my mobile device. It's also directly connected to a raspberry pi. Router 2's subnet is 192.168.2.1
Router 1 is also an openwrt router that doesn't have a vpn installed. It's located at home and it's directly connected to a raspberry pi. It broadcasts a wireless signal for many devices to connect to, with one of them being router 2. Router 1's subnet is 192.168.1.1
Router 2 is wirelessly connected to router 1. It's not possible to use a wire to connect it to router 1
I had made this image to more clearly show what I am trying to do and what my network looks like.
The red lines show the kind of connections I want to make. I want my phone on router 2 to have access to the server on my other network.
Here's the configuration files for router 2.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'CF:5C:26:D2::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
list dns '192.168.2.15'
list dns '192.168.1.96'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
option auto '0'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
config interface 'wgclient'
option proto 'wireguard'
option private_key 'Ca5rzz5zUoj'
list addresses '100.120.156.107/32'
list dns '192.168.2.15'
list dns '192.168.1.96'
config wireguard_wgclient
option public_key 'APBj9Ukk3Y'
option preshared_key 'CLHkKo2RIt'
option endpoint_host 'www.random.org'
option endpoint_port '1194'
option route_allowed_ips '1'
option description 'Alaska'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option persistent_keepalive '25'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wgclient'
option output 'ACCEPT'
option masq '1'
list network 'wgclient'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wgclient'
config redirect 'dns_int'
option src 'lan'
option src_dport '53'
option proto 'tcp udp'
option target 'DNAT'
option family 'any'
option src_mac '!58:34:3C:8A:B3:34'
option name 'Redirect-DNS'
option src_ip '!192.168.2.15'
option dest_ip '192.168.2.15'
config ipset 'doh'
option name 'doh'
option family 'ipv4'
option match 'net'
option loadfile '/var/ipset-doh'
config rule 'doh_fwd'
option name 'Deny-DoH'
option src 'lan'
option dest 'wan'
option dest_port '443'
option proto 'tcp udp'
option family 'ipv4'
option ipset 'doh dest'
option target 'REJECT'
config ipset 'doh6'
option name 'doh6'
option family 'ipv6'
option match 'net'
option loadfile '/var/ipset-doh6'
config rule 'doh6_fwd'
option name 'Deny-DoH'
option src 'lan'
option dest 'wan'
option dest_port '443'
option proto 'tcp udp'
option family 'ipv6'
option ipset 'doh6 dest'
option target 'REJECT'
config rule 'dot_fwd'
option name 'Deny-DoT'
option src 'lan'
option dest 'wan'
option dest_port '853'
option proto 'tcp udp'
option target 'REJECT'
config nat 'dns_masq'
option name 'Masquerade-DNS'
option src 'lan'
option dest_ip '192.168.2.15'
option dest_port '53'
option proto 'tcp udp'
option target 'MASQUERADE'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.2.15'
list server '192.168.1.96'
list server '192.168.2.16'
option strictorder '1'
config dhcp 'lan'
option interface 'lan'
option dhcpv4 'server'
option start '0'
option limit '20'
option leasetime '6h'
list dhcp_option '6,192.168.2.15,192.168.1.96,192.168.2.16'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Router 1 partial configuration files
/etc/config/network
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
list dns '192.168.1.96'
list dns '192.168.2.16'
config interface 'wwan'
option proto 'dhcp'
option peerdns '0'
list dns '192.168.1.96'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config redirect 'dns_int'
option src 'lan'
option src_dport '53'
option proto 'tcp udp'
option target 'DNAT'
option family 'any'
option name 'Redirect-DNS1'
option src_ip '!192.168.1.96'
option dest_ip '192.168.1.96'
list src_mac '!00:E0:4C:36:00:61'
option dest 'lan'
option dest_port '53'
config nat 'dns_masq'
option name 'Masquerade-DNS1'
option src 'lan'
option dest_ip '192.168.1.96'
option dest_port '53'
option proto 'tcp udp'
option target 'MASQUERADE'
option src_ip '192.168.1.1/24'
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.1.96'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv4 'server'
option start '0'
option limit '99'
list dhcp_option '6,192.168.1.96'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config host
option name 'Server1'
option dns '1'
option mac '00:00:00:00'
option ip '192.168.1.96'
config host
option dns '1'
option mac '00:00:00:00'
option ip '192.168.1.64'
option name 'Router2'