What you want cannot be done with what you have.
You have only one public IP (the 217.160.X.Y) and many private IPs in the LAN.
You can either do 1:1 NAT (or DMZ) where everything from the public IP will be forwarded to only one private IP, or individual DNATs where you can select which protocol/port will be forwarded to which private IP.
If you had IPv6 you could have public IPs all the way and you would do what you want.
Thank you @trendy, this is a clear answer and it explains why I cannot find any how-to for this.  I will brace for lots of NAT rules then!
I will brace for lots of NAT rules then!
If I understand correctly, DNAT rules allow multiple ports in a single line, would you know if this can contain portranges or do DNAT rules require each individual port defined?
Thanks again, sorry for my somewhat frustrated communication yesterday; meanwhile I have slept well and today I'm in a much more constructive mindset again.. 
Cheers, Igor
I will mark this a solution to close the thread, thanks for the effort, much appreciated!
Well, if you must thing it, then you must thing it right. It's OpenWrt-thing, and it's case sensitive... Very sensitive!

yeah, I sensed I should cAsE it correct, OpenWrt. I have not given up on my concept with OpenWrt and made some progress! I removed my OpenVPN client from OpenWrt, so this box is basically just a plain router now, taking care of my Server-LAN(192.168.1.0/24). I fired up a client in this LAN, assigned IPv4 address 192.168.1.2 and configured this as the new OpenVPN client and now this dedicated OpenVPN client acts as the gateway for my whole Server-LAN. My Home-LAN 192.168.0.0/24 is still virtually untouched, unaffected and working just as usual which is most important..
With this setup and without any further ado, I can now (reverse-)proxy ANY incoming requests that are coming in to the OpenVPN Server at 217.160.X.Y to ANY server in my LAN at will and without adding or changing rules in OpenWrt. Basically I'm piercing my VPN tunnel THROUGH the OpenWrt router instead of FROM the router and this works as I intended!
The drawback: I bought my OpenWrt box carefully to support AES-encryption for my VPN traffic and this is now basically by-passed. Also it costs added recourse for the VPN client machine which I had not anticipated. I will now pursue a trial to see if I can manage to setup a virtual machine on the OpenWrt box and see if I can get that to work instead of a dedicated machine in the network.
This is all very heavy lifting for me though as I Am really novice to networking, vpn and linux in general. I might be back in a separate new post asking for some help and support, or -if I get this solved- I will post the solution that works for me..
I Am still intrigued about the OpenWrt-thing, but I have to thing-it and will see how to wing it! 


Thanks and cheers, Igor
If you explain more in detail what have you done there, we can help you migrate it to OpenWrt and take advantage of the hardware crypto machine.
Ok, here goes..
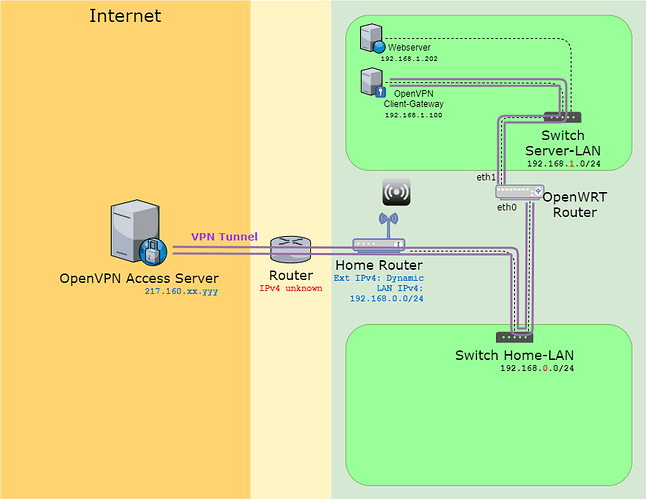
I will first add a diagram of my working Proof of Concept:
I have removed all traces from my initial OpenVPN client configuration (removed tun0 interface and zone 'VPN_zone'), now the OpenWrt box serves my Server-LAN (192.168.1.0/24) directly through the wan interface 192.168.0.2.
Proof of Concept: (working as desired)
In ServerLAN, I have an OpenVPN box 192.168.1.100 which connects to the OpenVPN Access Server 217.160.xx.yyy (fixed IPv4 on the internet). The client is configured as a VPN client-gateway for network 192.168.1.0/24. I have an webserver in the same Server-LAN on 192.168.1.201 serving the default webserver testpage.
On the OpenVPN AS 217.160.xx.yyy I have NGINX running with:
server {
listen 80;
listen [::]:80;
root /var/www/html;
index index.html;
server_name testmyopenwrt.myfirewall.org;
location / {
proxy_pass http://192.168.1.201:80;
try_files $uri $uri/ =404;
}
}
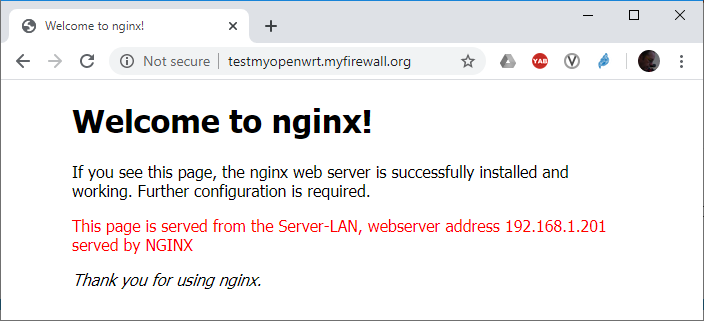
The domain testmyopenwrt.myfirewall.org has an A-Record with 217.160.xx.yyy.
http://testmyopenwrt.myfirewall.org opens:
I can fire up any amount of new webservers and access those with a corresponding NGINX serverblock on the OpenVPN AS without the need to add any NAT rules or such on OpenWrt.
What is your eventual end product? i.e. what are you intending to use this setup for when it's complete?
I will explore- and learn how to setup a load-balanced and scalable videoconferencing solution using the opensource solution of Jisti-Meet..
Consider it a test-bed. I'm using my home-connection and some private infrastructure with the VPN tunnel as a necessary 'evil' since I'm double-natted behind a Carrier Grade Network (this is how my isp hooks me up to the internet). Over time and with more knowledge (and sufficient budget), I may consider alternative service provider options. 
This is something you could do with your previous setup. You can move the OpenVPN endpoint to the OpenWrt and nothing will change in the way you can communicate from the internet.
But it anyway is not the same as your initial demand:
Here in the best case you can have multiple web servers, but for almost everything else you can have one port DNAT to an internal server/port.
Hello Trendy, thank you for not giving up on me!
I thought that I really know how important good communication is, especially about being clear and specific when asking technical questions. I was not clear, or at least not specific indeed!
As to my previous setup: are you sure I would be able to reverse-proxy same as with my shown NGINX example to my webservers in the Server-LAN? In my current 'proof-of-concept' setup I can ping my servers in the Server-LAN from my OpenVPN AS and -if I remember correctly- I tried that also in my previous setup but it failed. Is that such an example where I would need DNAT rules for ICMP?
As an example, I just tried in an ssh-session (ssh as root to my OpenVPN AS) to ssh into 192.168.1.201 which works. So currently I can ping and I can also ssh into my Server-LAN from my VPN server, would I also be able to do this in my previous setup?
Don't get me wrong: I WILL try to go back to previous setup, I just want to better understand the system before I let myself get into this..
You haven't really done anything with your 'proof of concept' other than bypass the firewall, which isn't really a great idea. You'd be far better off learning how to use the firewall properly, i.e. open/forward ports that need to be opened.
Yes, I Am very much aware of that! I thought I'd be able to do that as I progressed, but it is much harder (for me) than I thought and especially I find it difficult to use the right search-terms for what I try to accomplish.. I'm not giving up on it. I want to be much better aware when I implement my webserver related configs and something doesn't work, if can focus troubleshooting on the server part or if the issue at hand is network related. It's all so much new material to me that I have difficult times to continue with good motivation if I cannot find a resolution in a reasonable time.. 
So I'm really grateful for the support I got so far! 
I think the question for you is:
Do you want to enable full access for yourself only or for the whole internet?
You can have full access for yourself. Just connect to the VPN server from the internet and route the packets internally. Then you will be able to reach all your internal infrastructure without limitations.
If you want to allow anyone from the internet, then my previous reply applies.
Ok.. Done, I throw it in the ring and give up. I've spent the best part op last 3 hours trying to get it to work with the OpenWrt VPN-client to no avail.
I have reverted to my original setup, done in 10 minutes to get that working again. I'm facing the same challenges of course, but for the heck of me I can not understand how to configure it. In prvious answers in this thread, I get feedback like: "Just connect to the VPN server from the internet and route the packets internally".. or I should use: "individual DNATs where you can select which protocol/port will be forwarded to which private IP"..
And then I sit here, trying my way in, searching this forum, scratching my head, searching google, how to route packets with OpenWrt, or how to configure individual DNATs, trying again to reconfigure my OpenWrt, changing yet something else and NEVER any bit of success. I'm not a network guy, at least not on the level of packets that's for sure. I have a basic understanding of the topology and I will have to work with that because I'm not going to buy books and start a study in networking packets.
On this forum I would say: for me, there is a lack of clear examples. I can see some people trying to help me and I greatly appreciate the effort, but the help does not match what I need.
I will see if I can find another box with decent hardware AES encryption as a dedicated VPN box within my network, so I can make my 'Proof of Concept' the real deal. Or I re-purpose my current OpenWrt box to serve as the OpenVPN client (ignoring the second onboard nic) in my network because it is massively over-dimensioned to serve as just a plain, simple OpenWrt router.
Thanks, cheers, Igor
Still, you didn't answer my question, so I cannot help you further.
You need to understand that this is not something that one can find in an example somewhere. You are trying to implement something that very few people will even think of. Moreover there is the OpenVPN Server with some unknown to us OS, which makes it harder.
Typically a static route is enough to route packets to the right interface so they can find their way.
You already have one and it is not utilized, what good will it come from the second?
@ikerstges - there are lots of examples of various types of configurations in the wiki and the forums. And users are encouraged to contribute.
I think the issue here is that nobody really understands exactly what you are trying to achieve.
It still is not clear if you are trying to access your network for yourself (i.e. through a VPN), or if you are trying to serve stuff to anyone/everyone on the internet as a whole. And if you are tying to serve to the internet as a whole, it isn't clear exactly what you want to serve (you can't just arbitrarily provide complete unfettered access to multiple hosts via a single IPv4 address).
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.