I have a very simple requirement (he says, knowing little about networking...) I want to have a separate VLAN for my IOT devices (number chosen: 30), separate from my LAN.
IOT devices can talk to WAN, but not the LAN.
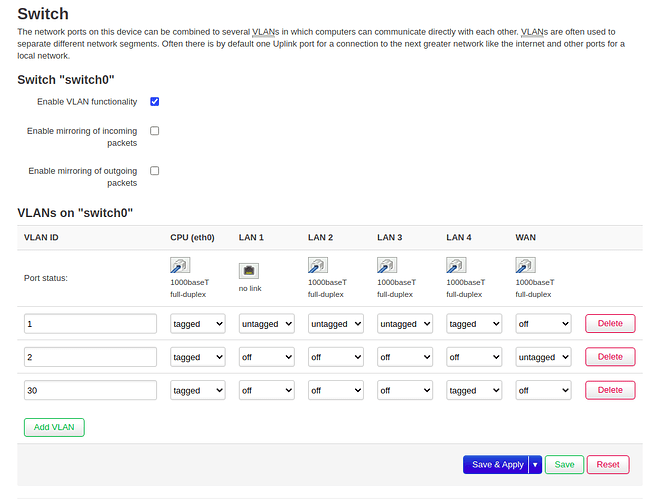
My Archer router has a 4-port switch. I want port 4 (actually written as 5 in the OpenWRT config) to be my "VLAN 30" port, i.e., port 4 only accepts tagged traffic.
Connected to port 4 is a TP link smart switch, which I use to tag the end-device traffic.
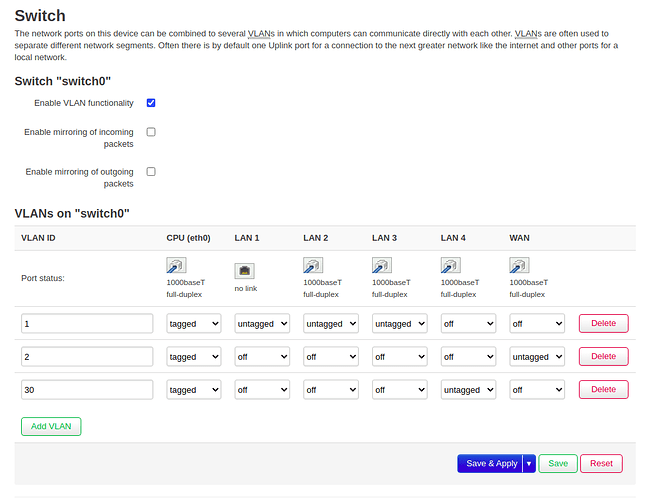
This is my general setup in OpenWRT
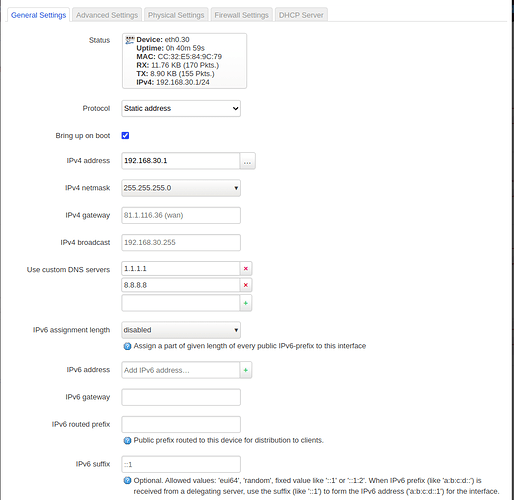
I create a new VLAN,
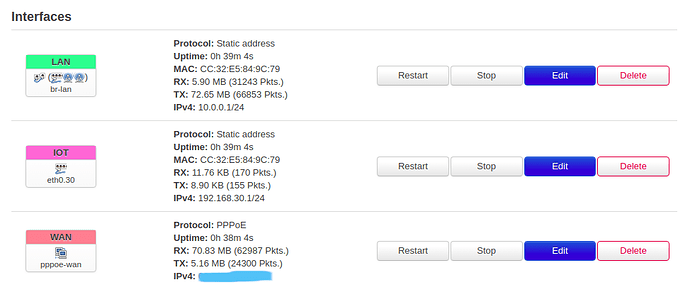
Add an a VLAN interface,
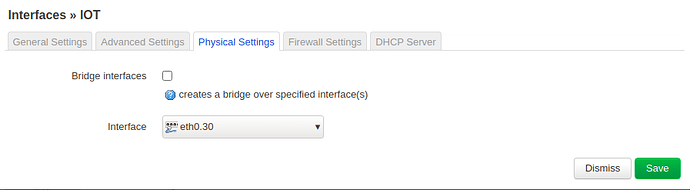
On the new VLAN,
Assign the right network,
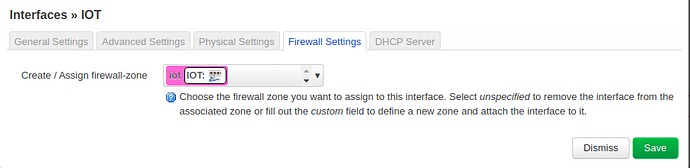
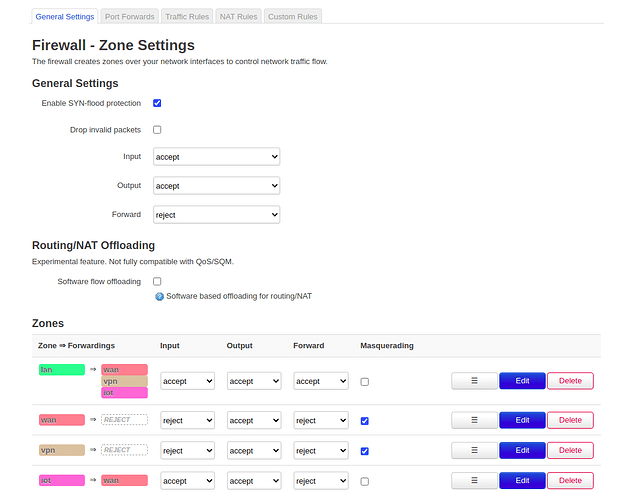
Create a firewall zone, allowing the LAN to connect to the IOT, and the IOT to access WAN,
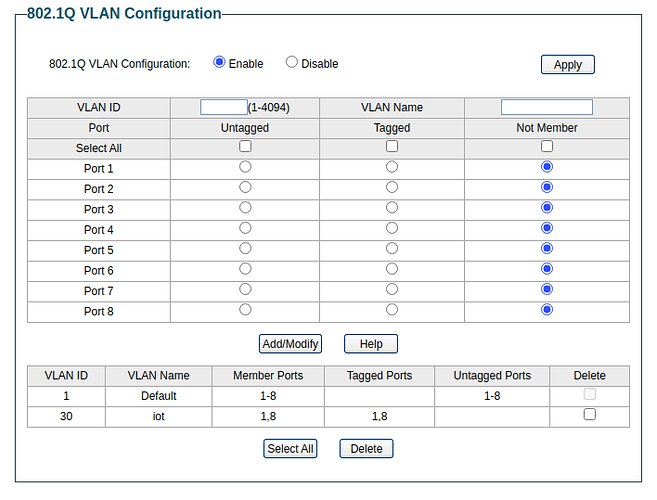
From the smart switch, I also setup VLAN, I want anything plugged to 1,8 ports to be in VLAN 30,
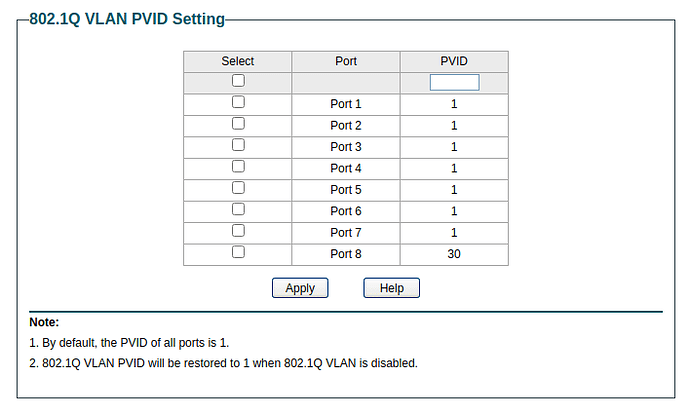
I have no idea what it is, but PVID settings too,
I can plug a machine into port 8 on the smart switch and get a DHCP assigned IP on the 192.168.30.0 network, but I can't access anything, not even the gateway on 192.168.30.1
Further, the smart switch doesn't get an IP address from what I can find.
network config,
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.0.0.1'
option ifname 'eth0.1'
config interface 'IOT'
option proto 'static'
option delegate '0'
option ipaddr '192.168.30.1'
option netmask '255.255.255.0'
option ifname 'eth0.30'
list dns '1.1.1.1'
list dns '8.8.8.8'
config interface 'wan'
option proto 'pppoe'
option username xxx
option delegate '0'
option ipv6 '0'
option password 'xxx'
option ifname 'eth0.2'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xxx
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 5t'
option vid '30'
config route
option target '10.42.0.0'
option netmask '255.255.0.0'
option gateway '10.0.0.145'
option interface 'lan'
config route
option target '192.168.1.0'
option gateway '192.168.1.1'
option netmask '255.255.255.0'
option interface 'lan'
firewall config,
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
list device 'tun+'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'tun0'
option network 'wan'
config forwarding 'lan_wan'
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option enabled '0'
config include
option path '/etc/firewall.user'
config zone 'vpn'
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding 'lan_vpn'
option src 'lan'
option dest 'vpn'
config rule 'ovpn'
option name 'Allow-OpenVPN'
option src 'wan'
option proto 'udp'
option target 'ACCEPT'
option dest_port '1195'
config redirect
option dest_port '1989'
option src 'wan'
option name 'ssh'
option src_dport '1989'
option target 'DNAT'
option dest_ip '10.0.0.1'
option dest 'lan'
config redirect
option src 'wan'
option name 'web'
option src_dport '80'
option target 'DNAT'
option dest_ip '10.0.0.220'
option dest 'lan'
list proto 'tcp'
config zone
option network 'IOT'
option input 'ACCEPT'
option forward 'REJECT'
option name 'iot'
option output 'ACCEPT'
list device 'eth0.30'
config forwarding
option dest 'iot'
option src 'lan'
config forwarding
option dest 'wan'
option src 'iot'
dhcp
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
list dhcp_option '6,10.0.0.6'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'IOT'
option leasetime '12h'
option interface 'IOT'
option start '10'
option limit '50'
root@OpenWrt:~# swconfig dev switch0 help
switch0: mdio-bus.0(Atheros AR8337), ports: 7 (cpu @ 0), vlans: 4096
--switch
Attribute 1 (int): enable_vlan (Enable VLAN mode)
Attribute 2 (none): reset_mibs (Reset all MIB counters)
Attribute 3 (int): ar8xxx_mib_poll_interval (MIB polling interval in msecs (0 to disable))
Attribute 4 (int): ar8xxx_mib_type (MIB type (0=basic 1=extended))
Attribute 5 (int): enable_mirror_rx (Enable mirroring of RX packets)
Attribute 6 (int): enable_mirror_tx (Enable mirroring of TX packets)
Attribute 7 (int): mirror_monitor_port (Mirror monitor port)
Attribute 8 (int): mirror_source_port (Mirror source port)
Attribute 9 (int): arl_age_time (ARL age time (secs))
Attribute 10 (string): arl_table (Get ARL table)
Attribute 11 (none): flush_arl_table (Flush ARL table)
Attribute 12 (int): igmp_snooping (Enable IGMP Snooping)
Attribute 13 (int): igmp_v3 (Enable IGMPv3 support)
Attribute 14 (none): apply (Activate changes in the hardware)
Attribute 15 (none): reset (Reset the switch)
--vlan
Attribute 1 (int): vid (VLAN ID (0-4094))
Attribute 2 (ports): ports (VLAN port mapping)
--port
Attribute 1 (none): reset_mib (Reset single port MIB counters)
Attribute 2 (string): mib (Get port's MIB counters)
Attribute 3 (int): enable_eee (Enable EEE PHY sleep mode)
Attribute 4 (none): flush_arl_table (Flush port's ARL table entries)
Attribute 5 (int): igmp_snooping (Enable port's IGMP Snooping)
Attribute 6 (int): vlan_prio (Port VLAN default priority (VLAN PCP) (0-7))
Attribute 7 (int): pvid (Primary VLAN ID)
Attribute 8 (unknown): link (Get port link information)
Can anyone help me with my conceptual misunderstandings here, I'm really lost and confused. Been trying to get this to work for several days and I'm feeling very desperate! TIA