Hello everyone,
May someone please explain to me how I can change my firewall zone settings / iptable rules such that a vLan can be connected to the internet yet remain isolated from all other vLans?
My current set up consists of 3 vLans, each with their own subnets and interfaces. Devices on these subnets successfully obtain the correct static ip, but when I use nmap -sV 192.168.0-255.0/24, regardless of which subnet I am on, I see all my hosts even on different subnets. I am also able to access my openWrt LuCi interface on the 192.168.1.X subnet while my device is on other subnets. I would like to fix these issues.
To get each vLan isolated, able to access the internet, and is not able to access the OpenWrt LuCi web user interface, i've read that default OpenWrt config has it such that the router allows cross communication via firewall zones.
Can anyone explain the exact settings to achieve this please? Thank you for the help in advance. 
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd8:ca6b:447b::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0.1 eth0.22'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '1c:3b:f3:3d:f9:0d'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option description 'vLan7'
option vid '7'
option ports '0t 5'
config interface 'vLan7'
option proto 'static'
option ifname 'eth0.7'
option netmask '255.255.255.0'
option ipaddr '192.168.7.1'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '6'
option description 'Vlan6'
option ports '0t 4'
config interface 'vLan6'
option ifname 'eth0.6'
option proto 'static'
option ipaddr '192.168.6.3'
option netmask '255.255.255.0'
option gateway 'X.X.X.X'
option broadcast '192.168.6.255'
config switch_vlan
option device 'switch0'
option vlan '5'
option vid '22'
option description 'vLan22'
option ports '0t 3'
config interface 'VLAN22'
option proto 'static'
option ipaddr '192.168.22.1'
option netmask '255.255.255.0'
option ifname 'eth0.22'
config include
option path '/etc/firewall.user'
option reload '1'
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
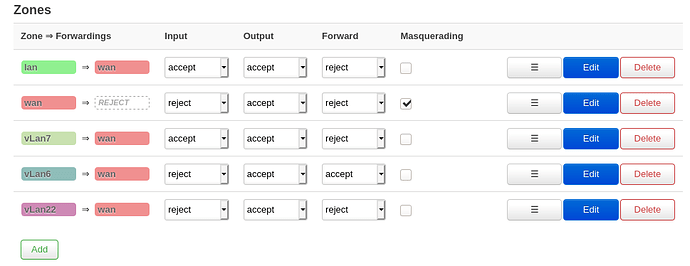
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option network 'lan'
option forward 'REJECT'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'vLan7'
option network 'vLan7'
option output 'ACCEPT'
option forward 'REJECT'
option input 'ACCEPT'
config forwarding
option src 'vLan7'
option dest 'wan'
config zone
option name 'vLan6'
option output 'ACCEPT'
option network 'vLan6'
option input 'REJECT'
option forward 'ACCEPT'
config forwarding
option src 'vLan6'
option dest 'wan'
config zone
option name 'vLan22'
option network 'VLAN22'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
config forwarding
option src 'vLan22'
option dest 'wan'
firewall.user file
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
iptables -A FORWARD -s 192.168.6.1/24 -d 192.168.1.0/24 -j REJECT
iptables -A FORWARD -s 192.168.1.1/24 -d 192.168.6.0/24 -j REJECT