Hi All,
I'm new to OpenWRT, and have basic knowledge of networking ( I understand Ip ranges etc and the concepts of vlans).
What I want is the following:
I have my current Broadband Router - Currently Sky soon to move
That is connected to a Gs724T V4, which is then connected to another Gs724T v3. Both are capable of vlans but not currently in use.
I have Pi Hole running on a VM, running on a physical PC
I have Home assistant running on a VM, running on a physical PC.
I have a Synology which hosts the iscsi for the above PC's
Multiple wired and wireless devices, mixture of tablets etc and "Smart devices"
What I am looking for:
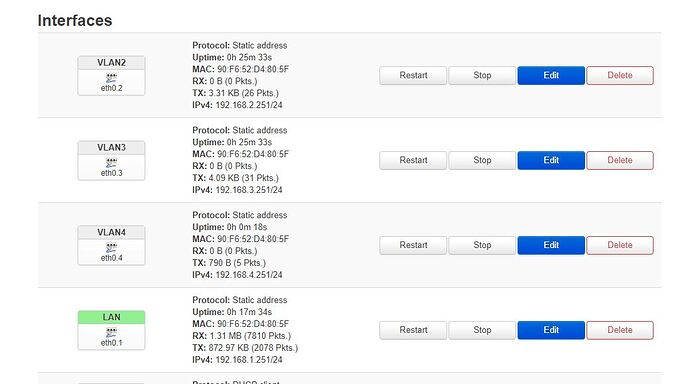
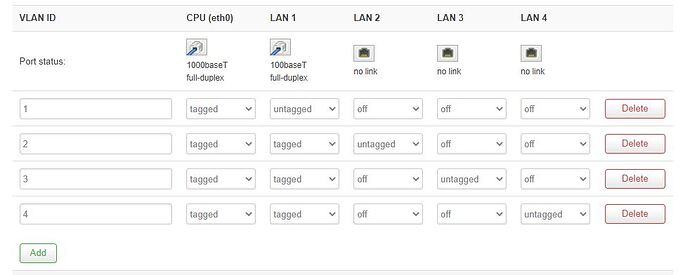
on my OpenWRT (TL-WR743ND) I want to run multiple DHCP servers, using the PI-Hole for DNS, and pointing to the sky router for gateway.
A) VLAN will be for the home automation + Home Assistant (Smart devices and the Home Assistant) - Home Assistant needs internet access but the smart devices do not.
B) VLAN for security - CCTV/ALARM etc which will need to feed into home Assistant (On VLAN A) - (may be better to be merged between the two?) Ideally also viewable from mobile devices which would be on the C vlan
C) VLAN for home desktop etc - main computing use
D) VLAN for guest devices (may not be needed if the broadband provider network allows connection straight out without being able to come back into one of the VLANS above).
The TL-WR743ND wont be connecting to the internet directly, and wont be used for WIFI - purely just DHCP for multiple VLANS.
I would then hang off an old router to act as wifi AP on each vlan as required (A and C and possibly D), disabling the WIFI on the OpenWRT and the providers router.
So firstly, would this work, and is there a better/easier way at minimal/no cost?
secondly, can someone give me high level steps on how to implement? I have found a few you-tube guides on creating vlans on OpenWRT but high level steps of the entire process would be good - things to look out for?
The OpenWRT install is fresh - only thing i have changed is the default password.