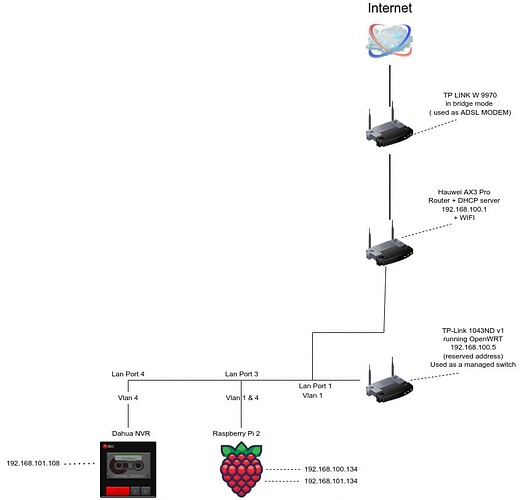
I'm using Dahua IP cameras (with NVR), i've been hacked (the camera sent outgoing requests and an attacker used it to connect/reset other devices).
The hack was possible since the NVR somehow was able to figure out the gateway/DNS.
To fix this i'm using an openWRT router (TP LINK 1043 v1) as a managed swich.
I've created two VLANs:
1 - home network and all devices
2 - unused
4 - NVR + Raspberry Pi
The Raspberry PI is required to be on both networks, since it is used as a NTP server and more tasks (VPN server and some more).
Is this config is enough (it is working for me, but not sure if I missed something)?
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd24:42ff:89fe::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'dhcp'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
option enable_vlan4k '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option description 'home network'
option ports '0 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5t'
config switch_vlan
option device 'switch0'
option description 'NVR-prevent internet access'
option vlan '4'
option ports '3t 4 5t'
config device
option name 'eth0.4'
option type '8021q'
option ifname 'eth0'
option vid '4'
option ipv6 '0'
config interface 'NVR'
option device 'eth0.4'
option proto 'static'
option ipaddr '192.168.101.1'
option netmask '255.255.255.0'
config device
option type 'bridge'
option name 'br-4-1'
list ports 'eth0.1'
list ports 'eth0.4'
config bridge-vlan
option device 'br-4-1'
option vlan '1'
list ports 'eth0.1'
list ports 'eth0.4'
config bridge-vlan
option device 'br-4-1'
option vlan '4'
list ports 'eth0.1'
list ports 'eth0.4'