Hello, I am looking for some help in creating vLans for my basic home network. My goal is to create 3 vLans, one for my gaming device, another for my work pc, a third for a shared pc.
I think the best way to approach this is to lay out my understanding and settings and if there are any mistakes can someone please point them out, thank you!
—————-
My scheme is:
ONT ->
TP-Link Archer C7 v5 with OpenWrt as router. ->
TP-Link sg108e switch. ->
User devices obtain networking capabilities from switch.
————————
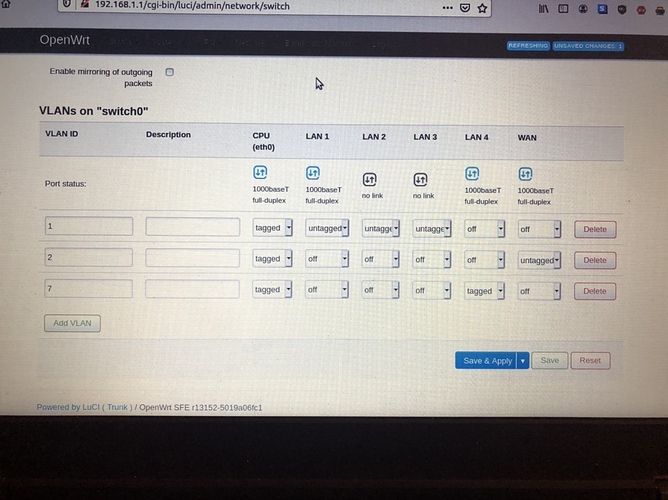
Since I am connecting a router to a switch, if I understand correctly, the port connecting the two has to be tagged? I did this on vLan 4, I left eth0 as tagged as well, but I think that might be wrong because why would the connection between router and switch involve eth0 on this network level.
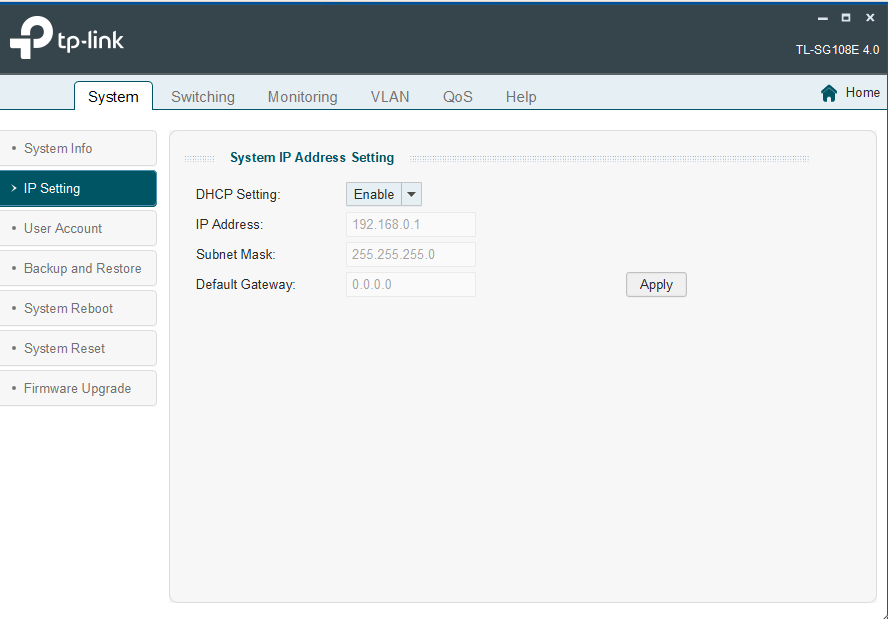
Next I believe I need to manage the vLans in the switch interface. I left DHCP settings as enabled in the DHCP settings.
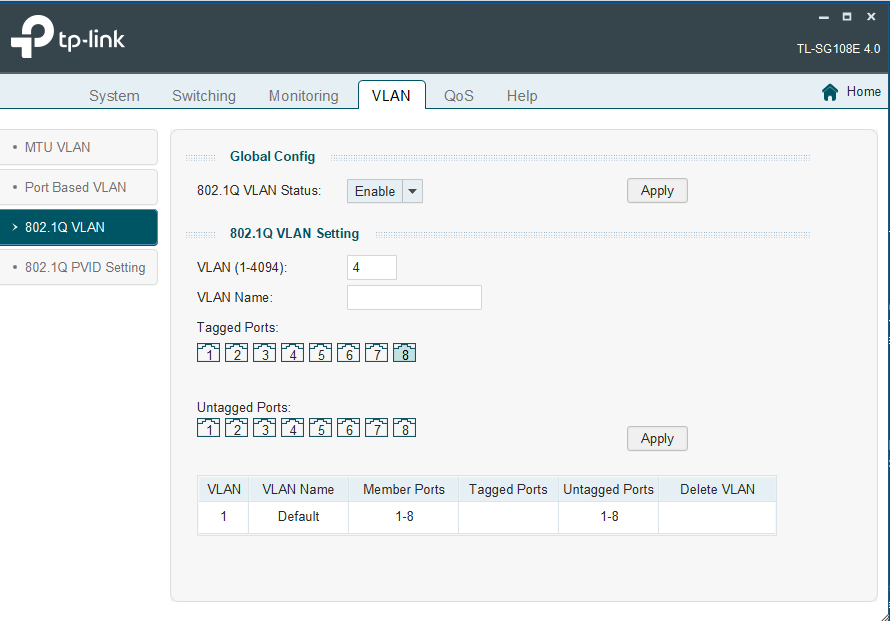
In the 802.1q vLan settings, here I would create 1 vLan for a tagged connection to the router and 3 untagged vLan connections to my end point user devices?
Connection between switch and router:
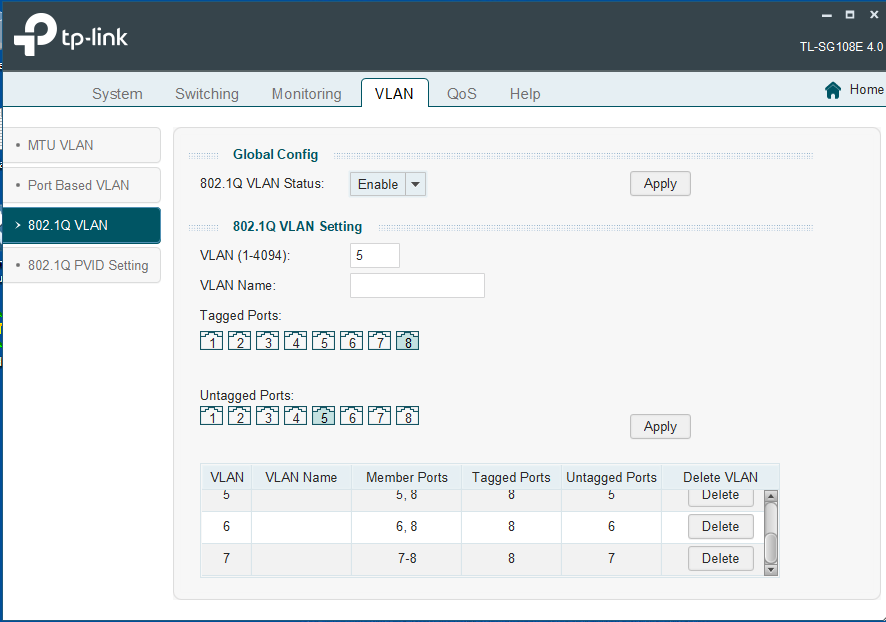
Then create 3 untagged vLans for each for my desired devices.
Example connection from switch to user device:
After this I would have to add the vLans to the 802.1Q PVID settings and create an interface for each vLan in the openwrt interface settings.
Does this set up seem correct? Can someone please point out any errors or misunderstandings. I’ve been trying to apply vLans to my network for a while now and keep bringing my network down and we all rely heavily on the network now, so I’m trying to avoid bringing the network down again.
Thank you,
Mateusz