No, you don't.
Again, see thread:
I think you're confusing an app on your devices, with setting up a VPN on your OpenWrt.
No, you don't.
Again, see thread:
I think you're confusing an app on your devices, with setting up a VPN on your OpenWrt.
I think you are right, i am confused what will be first step.. what i have to implement first
What is wcfg here?
This step is completed, now I have wgcf-profile.conf file which is working fine with WireGuard windows app. I can see my Ip from Cloudflare. many thanks @lleachii , Kindly suggest next step.
Applied it step by step with below guide, but not able to connect, its connecting fine with windows wireguard app but not with OpenWrt. here I am using configuration file which i have generated using wgcf. Thanks
You mean OpneVPN with Wireguard config? i am also using Cloudflare it this will work?
Any article/video do you want to refer?
It really isn't.
Nope. Cloudflare's VPN service only uses Wireguard.
Guys, Could you please guide me, what I missed, why my WireGuard + Cloudflare configuration not working on OpenWrt.
Thanks
We need to see your current configuration.
Please copy the output of the following command and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network; cat /etc/config/firewall; wg
cat /etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix '<an_ipv6>'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.0.1'
option ipaddr '192.168.1.1'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option metric '20'
option peerdns '0'
list dns '1.1.1.1'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
config interface 'wg0'
option proto 'wireguard'
option private_key '<wireguard-private-key>'
option peerdns '0'
list dns '1.1.1.1'
option metric '10'
list addresses '<cloudflareipv6>'
list addresses '<cloudflareipV4>'
config wireguard_wg0
option endpoint_port '2408'
option description 'Cloudflare'
option public_key '<peer-public-key>'
list allowed_ips '::/0'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '162.159.192.1'
cat /etc/config/firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
list network 'wg0'
option masq '1'
config forwarding
option src 'lan'
option dest 'vpn'
Your config seems fine.
To be clear
These can be removed.
Your OpenWrt is connected to the Internet, correct?
After enable interface 'wg0' : No, else connected.
** You're using the OpenWrt for Internet connectivity, correct?**
Yes
You disabled this key/config on your testing device, and you're only testing with OpenWrt, correct?
I am testing, after connecting, i will move on next step as we discussed ![]()
Removed
option peerdns '0'
list dns '1.1.1.1'
Thanks
Still not able to connect, same issue, no internet after enable interface 'wg0'
I'm actually not able to follow your progress.
This didn't answer my question.
???
Can you provide the output of the other command asked of you?
Nothing
This didn't answer my question.
Simply internet is working, when i tried to connect wireguard interface, No internet, currently interface 0 is disabled so internet is working, after enable wg0, no internet
Config is not loaded into Wireguard Kernel module.
![]() Reboot the router (or try hitting Restart button
Reboot the router (or try hitting Restart button ![]() ), then show output of command again.
), then show output of command again.
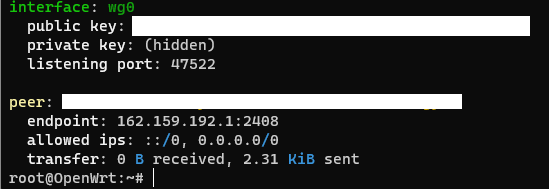
![]()
Only use config on OpenWrt!!!
Yes, just for your information I have connected it and given you screenshot. testing device not running anything.