I need for my clients to have a WI-FI that works for teleworking and that their children can play at the console at the same time or not, I have to assign the dhcp and static to the PCs in lan and wifi
And my PS4 console in lan but several scenarios can play if their child plays in wifi is enough to assign in wifi the ps4 is it right?
this is my config 
i'm precise is important for me have the wifi and lan for gaming and teleworking  thanks for help in advance @segal_72 @dlakelan @EXREYFOX @moeller0 @dtaht
thanks for help in advance @segal_72 @dlakelan @EXREYFOX @moeller0 @dtaht
this is my config of firewall
config include
option path '/etc/firewall.user'
config rule
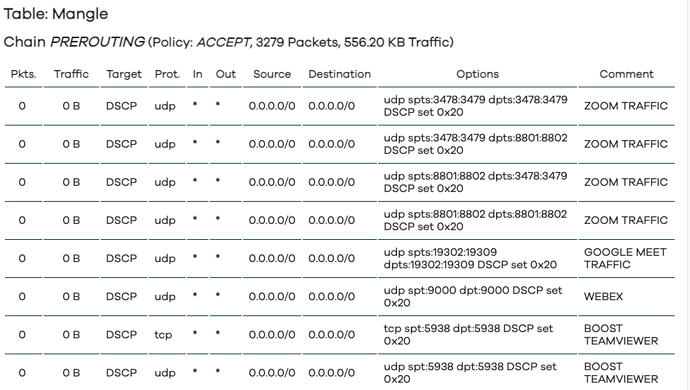
option name 'ZOOM TRAFFIC '
list proto 'udp'
option src 'wan'
option src_port '3478-3479 8801-8802'
option dest '*'
option dest_port '3478-3479 8801-8802'
option target 'DSCP'
option set_dscp 'CS4'
config redirect
option target 'DNAT'
option name 'DMZ'
option src 'wan'
option src_dport '1-65535'
option dest 'lan'
option dest_ip '192.168.2.167'
option dest_port '1-65535'
config rule
option name 'GOOGLE MEET TRAFFIC'
list proto 'udp'
option src 'wan'
option src_port '19302-19309'
option dest '*'
option dest_port '19302-19309'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'WEBEX'
list proto 'udp'
option src 'wan'
option src_port '9000'
option dest_port '9000'
option target 'DSCP'
option set_dscp 'CS4'
option dest '*'
config rule
option name 'BOOST TEAMVIEWER'
option src 'wan'
option src_port '5938'
option dest '*'
option dest_port '5938'
option target 'DSCP'
option set_dscp 'CS4'
config rule
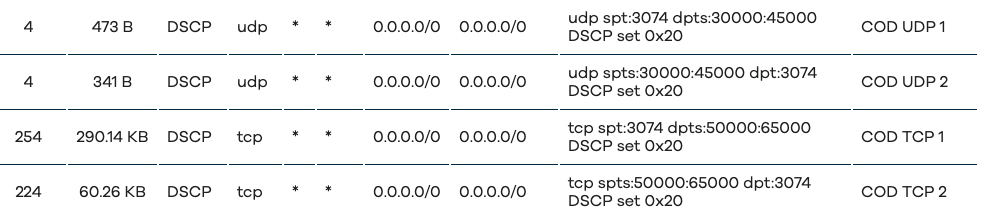
option name 'COD UDP 1'
option family 'ipv4'
list proto 'udp'
option src 'wan'
option src_port '3074'
option dest '*'
option dest_port '30000-45000'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'COD UDP 2'
list proto 'udp'
option src 'wan'
option src_port '30000-45000'
option dest '*'
option dest_port '3074'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'COD TCP 1'
option family 'ipv4'
list proto 'tcp'
option src 'wan'
option src_port '3074'
option dest '*'
option dest_port '50000-65000'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'COD TCP 2'
option family 'ipv4'
list proto 'tcp'
option src 'wan'
option src_port '50000-65000'
option dest '*'
option dest_port '3074'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'FIFA 20'
option family 'ipv4'
list proto 'udp'
option src 'wan'
option src_port '3659'
option dest '*'
option dest_port '3659'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'FIFA UDP 3'
option family 'ipv4'
list proto 'udp'
option src 'wan'
option src_port '9999'
option dest '*'
option dest_port '9999'
option target 'DSCP'
option set_dscp 'CS4'
config rule
option name 'FORNITE UDP 1'
option family 'ipv4'
option src 'wan'
option src_port '9000-10000'
option dest '*'
option dest_port '50000-65000'
option target 'DSCP'
option set_dscp 'CS4'
list proto 'udp'
config rule
option name 'FORNITE UDP 2'
option family 'ipv4'
list proto 'udp'
option src 'wan'
option src_port '50000-65000'
option dest_port '9000-10000'
option target 'DSCP'
option set_dscp 'CS4'
option dest '*'
config rule
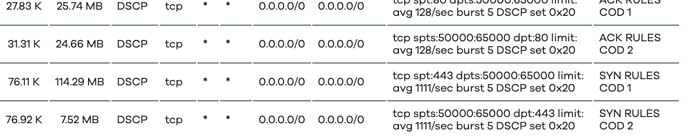
option name 'ACK RULES COD 1'
list proto 'tcp'
option src 'wan'
option src_port '80'
option dest '*'
option dest_port '50000-65000'
option target 'DSCP'
option set_dscp 'CS4'
option family 'ipv4'
option limit '128/second'
config rule
option name 'ACK RULES COD 2'
list proto 'tcp'
option src 'wan'
option src_port '50000-65000'
option dest '*'
option dest_port '80'
option target 'DSCP'
option set_dscp 'CS4'
option family 'ipv4'
option limit '128/second'
config rule
option name 'SYN RULES COD 1'
list proto 'tcp'
option src 'wan'
option src_port '443'
option dest '*'
option dest_port '50000-65000'
option target 'DSCP'
option set_dscp 'CS4'
option family 'ipv4'
option limit '1024/second'
config rule
option name 'SYN RULES COD 2'
option family 'ipv4'
list proto 'tcp'
option src 'wan'
option src_port '50000-65000'
option dest '*'
option dest_port '443'
option target 'DSCP'
option set_dscp 'CS4'
option limit '1024/second'
root@OpenWrt:~#
my config SQM now
root@OpenWrt:~# cat /etc/config/sqm
config queue 'eth1'
option interface 'eth1'
option qdisc 'cake'
option script 'piece_of_cake.qos'
option ingress_ecn 'ECN'
option egress_ecn 'ECN'
option itarget 'auto'
option etarget 'auto'
option enabled '1'
option download '0'
option upload '16000'
option debug_logging '0'
option verbosity '5'
option qdisc_advanced '1'
option squash_dscp '1'
option squash_ingress '1'
option qdisc_really_really_advanced '1'
option iqdisc_opts 'nat dual-dsthost ingress'
option eqdisc_opts 'nat dual-srchost ack-filter'
option linklayer 'ethernet'
option overhead '44'
option linklayer_advanced '1'
option tcMTU '2047'
option tcTSIZE '128'
option tcMPU '0'
option linklayer_adaptation_mechanism 'cake'
config queue
option enabled '1'
option download '0'
option upload '56000'
option debug_logging '0'
option verbosity '5'
option qdisc 'cake'
option script 'piece_of_cake.qos'
option qdisc_advanced '1'
option squash_dscp '1'
option squash_ingress '1'
option ingress_ecn 'ECN'
option egress_ecn 'NOECN'
option qdisc_really_really_advanced '1'
option iqdisc_opts 'nat dual-dsthost ingress'
option eqdisc_opts 'nat dual-srchost ack-filter'
option linklayer 'ethernet'
option overhead '44'
option linklayer_advanced '1'
option tcMTU '2047'
option tcTSIZE '128'
option tcMPU '0'
option linklayer_adaptation_mechanism 'cake'
option interface 'eth0'
config queue
option enabled '1'
option interface 'radio0.network1'
option download '0'
option upload '56000'
option debug_logging '0'
option verbosity '5'
option qdisc 'cake'
option script 'piece_of_cake.qos'
option qdisc_advanced '1'
option squash_dscp '1'
option squash_ingress '1'
option ingress_ecn 'ECN'
option egress_ecn 'NOECN'
option qdisc_really_really_advanced '1'
option iqdisc_opts 'nat dual-dsthost ingress'
option eqdisc_opts 'nat dual-srchost ack-filter'
option linklayer 'ethernet'
option overhead '44'
option linklayer_advanced '1'
option tcMTU '2047'
option tcTSIZE '128'
option tcMPU '0'
option linklayer_adaptation_mechanism 'cake'
root@OpenWrt:~#
i playing often to COD and FPS and with this test and settings my gameplay is very very speed
i have never a gameplay fluide before my settings than use now
Test bufferbloat with my PC in wifi with my ps4 pluged and mode on
now my pc in lan always ps4 connected
i'm use a settings for COD and is very powerfull  but just i'm not sure for ack rules but cod udp and cod TCP very fast when rules enabled
but just i'm not sure for ack rules but cod udp and cod TCP very fast when rules enabled