Hi
i like to set up passphrase based auth/vlan dumb AP on HaP AC2
DSA is working well
ports are correctly tagged/untagged (tested)
but wireless is not working
i could connect to AP with various passwords, and WIFI interfaces are added to bridge with correct PVID
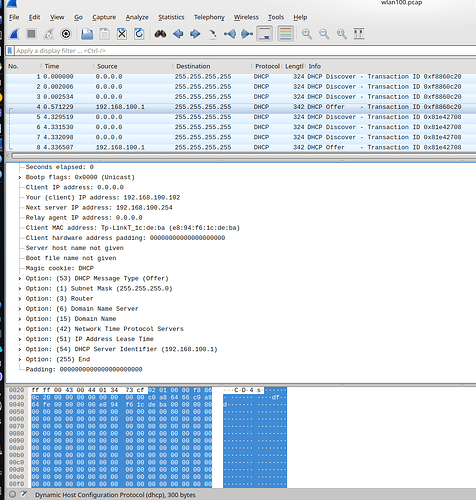
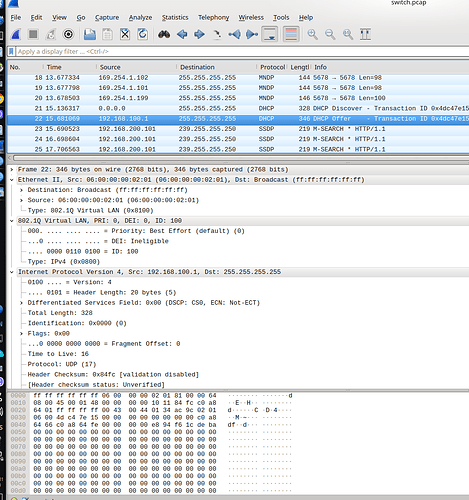
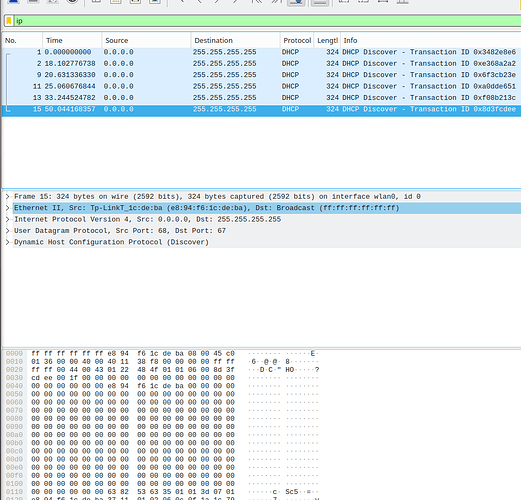
but clients newer got IP from dhcp server
i tried with CT and nonCT wifi drivers
same result
any idea how to solve this ???
edit: distro info
DISTRIB_RELEASE='SNAPSHOT'
DISTRIB_REVISION='r23827-ef76b6ff3e'
DISTRIB_TARGET='ipq40xx/mikrotik'
DISTRIB_ARCH='arm_cortex-a7_neon-vfpv4'
DISTRIB_DESCRIPTION='OpenWrt SNAPSHOT r23827-ef76b6ff3e'
here is relevant info
bridge vlan show
port vlan-id
lan4 255 PVID Egress Untagged
lan3 200 PVID Egress Untagged
lan2 100 PVID Egress Untagged
lan1 2 PVID Egress Untagged
wan 1 PVID Egress Untagged
2
100
200
255
switch 1
2
100
200
255
wlan1-vlan255 255 PVID Egress Untagged
wlan1-vlan200 200 PVID Egress Untagged
wlan1-vlan100 100 PVID Egress Untagged
wlan1-vlan2 2 PVID Egress Untagged
wlan1-vlan1 1 PVID Egress Untagged
wlan0-vlan255 255 PVID Egress Untagged
wlan0-vlan200 200 PVID Egress Untagged
wlan0-vlan100 100 PVID Egress Untagged
wlan0-vlan2 2 PVID Egress Untagged
wlan0-vlan1 1 PVID Egress Untagged
brctl show
bridge name bridge id STP enabled interfaces
switch 7fff.0855317e66ff no wlan1-vlan1
wlan0-vlan2
wlan0-vlan200
lan4
lan2
wlan0-vlan255
wlan1-vlan2
wan
wlan1-vlan200
wlan0-vlan100
wlan1-vlan255
wlan0-vlan1
lan3
wlan1-vlan100
lan1
config wifi-iface 'wifinet0'
option device 'radio0'
option mode 'ap'
option ssid 't-WIFI'
option encryption 'psk2+aes'
option wmm '1'
option short_preamble '1'
option disassoc_low_ack '0'
option max_inactivity '120'
option isolate '1'
option disabled '0'
option key 'SomeUnusedPass'
option ifname 'wlan0'
option macaddr '0e:01:99:00:01:99'
config wifi-iface 'wifinet1'
option device 'radio1'
option mode 'ap'
option ssid 't5-WIFI'
option encryption 'psk2+aes'
option wmm '1'
option short_preamble '1'
option disassoc_low_ack '0'
option max_inactivity '120'
option isolate '1'
option disabled '0'
option key 'SomeUnusedPass'
option ifname 'wlan1'
option macaddr '0e:01:99:01:01:99'
config wifi-vlan
option name 'vlan1'
option network 'vlan1'
option vid '1'
config wifi-station
option key 'tst1-vlan1'
option vid '1'
config wifi-vlan
option name 'vlan2'
option network 'vlan2'
option vid '2'
config wifi-station
option key 'tst2-guest'
option vid '2'
config wifi-vlan
option name 'vlan100'
option network 'vlan100'
option vid '100'
config wifi-station
option key 'tst100-prn'
option vid '100'
config wifi-vlan
option name 'vlan200'
option network 'vlan200'
option vid '200'
config wifi-station
option key 'tst200-lan'
option vid '200'
config wifi-vlan
option name 'vlan255'
option network 'vlan255'
option vid '255'
config wifi-station
option key 'tst255-vlan255'
option vid '255'
config device
option type 'bridge'
option name 'switch'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'wan'
config bridge-vlan
option device 'switch'
option vlan '1'
list ports 'wan:u*'
config bridge-vlan
option device 'switch'
option vlan '2'
list ports 'lan1:u*'
list ports 'wan:t'
config bridge-vlan
option device 'switch'
option vlan '100'
list ports 'lan2:u*'
list ports 'wan:t'
config bridge-vlan
option device 'switch'
option vlan '200'
list ports 'lan3:u*'
list ports 'wan:t'
config bridge-vlan
option device 'switch'
option vlan '255'
list ports 'lan4:u*'
list ports 'wan:t'
config interface 'vlan1'
option device 'switch.1'
option proto 'none'
config interface 'vlan2'
option proto 'none'
option device 'switch.2'
config interface 'vlan100'
option proto 'none'
option device 'switch.100'
config interface 'vlan200'
option proto 'none'
option device 'switch.200'
config interface 'vlan255'
option proto 'static'
option device 'switch.255'
option ipaddr '169.254.1.199'
option netmask '255.255.255.0'
option gateway '169.254.1.1'
option dns '169.254.1.1'
edit2: wifi log
Mon Sep 4 15:59:06 2023 daemon.info hostapd: wlan0: STA 38:fb:14:81:a2:0f IEEE 802.11: authenticated
Mon Sep 4 15:59:06 2023 daemon.info hostapd: wlan0: STA 38:fb:14:81:a2:0f IEEE 802.11: associated (aid 1)
Mon Sep 4 15:59:06 2023 daemon.notice hostapd: Assigned VLAN ID 100 from wpa_psk_file to 38:fb:14:81:a2:0f
Mon Sep 4 15:59:06 2023 daemon.notice hostapd: wlan0: AP-STA-CONNECTED 38:fb:14:81:a2:0f auth_alg=open
Mon Sep 4 15:59:06 2023 daemon.info hostapd: wlan0: STA 38:fb:14:81:a2:0f RADIUS: starting accounting session 01E9E84997870D25
Mon Sep 4 15:59:06 2023 daemon.info hostapd: wlan0: STA 38:fb:14:81:a2:0f WPA: pairwise key handshake completed (RSN)
Mon Sep 4 15:59:06 2023 daemon.notice hostapd: wlan0: EAPOL-4WAY-HS-COMPLETED 38:fb:14:81:a2:0f