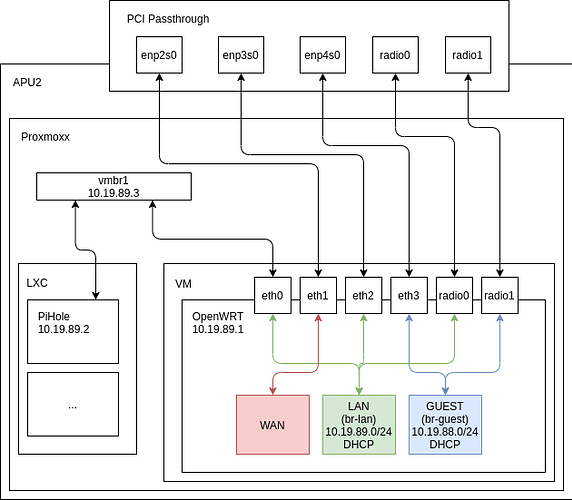
Hi,
I basically want to do the same as @AGL in his Topic: Creating a second network on single router for VPN
I want LAN traffic to go through the VPN and a guest network fully detached from LAN and the VPN.
My Setup:
Editable: APU2 setup
So I disabled route_allowed_ips:
uci set network.wgserver.route_allowed_ips="0"
uci commit network
/etc/init.d/network restart
But I still can't get Internet Access from the Guest network.
Also if I'm not setting Input, Output and Forward to 'ACCEPT' in the Guest to WAN rule, the clients in the Guest Network won't get an IP Adress from the DHCP Server:
openwrt Error sending DHCP packet to 10.19.88.176: Operation not permitted
I'm pretty inexperienced with most "low level" network/IP-Tables stuff. I'm eager to learn it, but after googling for 6 hours I think I may need a hint 
uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fda8:2149:e3a8::/48'
network.WAN=interface
network.WAN.proto='dhcp'
network.WAN.macaddr='00:0D:B9:4C:A3:44'
network.WAN.ifname='eth1'
network.LAN=interface
network.LAN.proto='static'
network.LAN.type='bridge'
network.LAN.netmask='255.255.255.0'
network.LAN.ipaddr='10.19.89.1'
network.LAN.ifname='eth0 eth2'
network.MULLVAD=interface
network.MULLVAD.proto='wireguard'
network.MULLVAD.addresses='X.X.X.X/32'
network.MULLVAD.private_key='***'
network.MULLVAD.force_link='1'
network.@wireguard_MULLVAD[0]=wireguard_MULLVAD
network.@wireguard_MULLVAD[0].persistent_keepalive='25'
network.@wireguard_MULLVAD[0].endpoint_port='51820'
network.@wireguard_MULLVAD[0].allowed_ips='0.0.0.0/0'
network.@wireguard_MULLVAD[0].endpoint_host='nl4-wireguard.mullvad.net'
network.@wireguard_MULLVAD[0].public_key='hnRyse6QxPPcZOoSwRsHUtK1W+APWXnIoaDTmH6JsHQ='
network.@wireguard_MULLVAD[0].description='nl4-wireguard.mullvad.net'
network.GUEST=interface
network.GUEST.type='bridge'
network.GUEST.proto='static'
network.GUEST.ipaddr='10.19.88.1'
network.GUEST.netmask='255.255.255.0'
network.GUEST.ifname='eth3'
uci show wireless
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.channel='36'
wireless.radio0.hwmode='11a'
wireless.radio0.path='pci0000:00/0000:00:10.0'
wireless.radio0.htmode='VHT80'
wireless.radio0.distance='50'
wireless.radio0.country='DE'
wireless.radio0.disabled='1'
wireless.radio1=wifi-device
wireless.radio1.type='mac80211'
wireless.radio1.channel='36'
wireless.radio1.hwmode='11a'
wireless.radio1.path='pci0000:00/0000:00:1f.0/0000:02:0d.0'
wireless.radio1.htmode='VHT80'
wireless.radio1.distance='50'
wireless.radio1.country='DE'
wireless.wifinet0=wifi-iface
wireless.wifinet0.network='GUEST'
wireless.wifinet0.wpa_disable_eapol_key_retries='1'
wireless.wifinet0.ssid='Guest'
wireless.wifinet0.device='radio1'
wireless.wifinet0.mode='ap'
wireless.wifinet0.ieee80211w='1'
wireless.wifinet0.key='***'
wireless.wifinet0.encryption='psk2'
wireless.wifinet1=wifi-iface
wireless.wifinet1.ssid='Secure'
wireless.wifinet1.encryption='psk2'
wireless.wifinet1.device='radio0'
wireless.wifinet1.mode='ap'
wireless.wifinet1.wpa_disable_eapol_key_retries='1'
wireless.wifinet1.key='***'
wireless.wifinet1.network='LAN'
wireless.wifinet1.disabled='1'
uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.lan=zone
firewall.lan.name='lan'
firewall.lan.input='ACCEPT'
firewall.lan.output='ACCEPT'
firewall.lan.forward='ACCEPT'
firewall.lan.network='LAN'
firewall.guest=zone
firewall.guest.name='guest'
firewall.guest.network='GUEST'
firewall.guest.input='ACCEPT'
firewall.guest.output='ACCEPT'
firewall.guest.forward='ACCEPT'
firewall.wan=zone
firewall.wan.name='wan'
firewall.wan.input='REJECT'
firewall.wan.output='ACCEPT'
firewall.wan.forward='REJECT'
firewall.wan.network='wan wan6 WAN'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[3]=zone
firewall.@zone[3].network='MULLVAD'
firewall.@zone[3].name='WG_FW'
firewall.@zone[3].mtu_fix='1'
firewall.@zone[3].input='REJECT'
firewall.@zone[3].forward='REJECT'
firewall.@zone[3].masq='1'
firewall.@zone[3].output='ACCEPT'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='WG_FW'
firewall.@forwarding[0].src='lan'
firewall.guest_wan=forwarding
firewall.guest_wan.src='guest'
firewall.guest_wan.dest='wan'
firewall.guest_dns=rule
firewall.guest_dns.name='Allow-DNS-Guest'
firewall.guest_dns.src='guest'
firewall.guest_dns.dest_port='53'
firewall.guest_dns.proto='tcp udp'
firewall.guest_dns.target='ACCEPT'
uci show dhcp
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].logqueries='1'
dhcp.@dnsmasq[0].server='10.19.89.2'
dhcp.@dnsmasq[0].interface='br-LAN' 'br-guest'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_management='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
dhcp.LAN=dhcp
dhcp.LAN.start='100'
dhcp.LAN.leasetime='12h'
dhcp.LAN.interface='LAN'
dhcp.LAN.limit='150'
dhcp.LAN.dhcp_option='6,10.19.89.2'
dhcp.@host[0]=host
dhcp.@host[0].mac='EA:25:6F:59:08:0F'
dhcp.@host[0].name='pihole'
dhcp.@host[0].dns='1'
dhcp.@host[0].ip='10.19.89.2'
dhcp.@host[1]=host
dhcp.@host[1].name='apu2'
dhcp.@host[1].dns='1'
dhcp.@host[1].ip='10.19.89.3'
dhcp.@host[1].mac='92:B9:59:7E:F3:97'
dhcp.LAN_PUBLIC=dhcp
dhcp.LAN_PUBLIC.start='100'
dhcp.LAN_PUBLIC.leasetime='12h'
dhcp.LAN_PUBLIC.limit='150'
dhcp.LAN_PUBLIC.interface='LAN_PUBLIC'
dhcp.LAN_PUBLIC.dhcp_option='6,10.19.90.3'
dhcp.guest=dhcp
dhcp.guest.interface='guest'
dhcp.guest.start='100'
dhcp.guest.limit='150'
dhcp.guest.leasetime='1h'
dhcp.guest.dhcp_option='6,1.1.1.1'
grep -v -e ^# -e ^$ /etc/firewall.user;
empty
head -v -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface WAN
nameserver 10.19.90.3
search fritz.box
head: /tmp/resolv.*/*: No such file or directory
ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-LAN state UP group default qlen 1000
link/ether 3a:32:67:2c:4f:28 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:0d:b9:4c:a3:44 brd ff:ff:ff:ff:ff:ff
inet 10.19.90.21/24 brd 10.19.90.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::20d:b9ff:fe4c:a344/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-LAN state UP group default qlen 1000
link/ether 00:0d:b9:4c:a3:45 brd ff:ff:ff:ff:ff:ff
5: eth3: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq master br-GUEST state DOWN group default qlen 1000
link/ether 00:0d:b9:4c:a3:46 brd ff:ff:ff:ff:ff:ff
6: wlan0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 04:f0:21:85:42:3a brd ff:ff:ff:ff:ff:ff
8: br-GUEST: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 00:0d:b9:4c:a3:46 brd ff:ff:ff:ff:ff:ff
inet 10.19.88.1/24 brd 10.19.88.255 scope global br-GUEST
valid_lft forever preferred_lft forever
inet6 fe80::20d:b9ff:fe4c:a346/64 scope link
valid_lft forever preferred_lft forever
9: br-LAN: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 3a:32:67:2c:4f:28 brd ff:ff:ff:ff:ff:ff
inet 10.19.89.1/24 brd 10.19.89.255 scope global br-LAN
valid_lft forever preferred_lft forever
inet6 fe80::3832:67ff:fe2c:4f28/64 scope link
valid_lft forever preferred_lft forever
10: MULLVAD: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
link/none
inet X.X.X.X/32 brd 255.255.255.255 scope global MULLVAD
valid_lft forever preferred_lft forever
11: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-GUEST state UP group default qlen 1000
link/ether 04:f0:21:88:40:33 brd ff:ff:ff:ff:ff:ff
inet6 fe80::6f0:21ff:fe88:4033/64 scope link
valid_lft forever preferred_lft forever
ip route show table all
default dev MULLVAD proto static scope link
10.19.88.0/24 dev br-GUEST proto kernel scope link src 10.19.88.1
10.19.89.0/24 dev br-LAN proto kernel scope link src 10.19.89.1
10.19.90.0/24 dev eth1 proto kernel scope link src 10.19.90.21
193.32.249.69 via 10.19.90.1 dev eth1 proto static
broadcast 10.19.88.0 dev br-GUEST table local proto kernel scope link src 10.19.88.1
local 10.19.88.1 dev br-GUEST table local proto kernel scope host src 10.19.88.1
broadcast 10.19.88.255 dev br-GUEST table local proto kernel scope link src 10.19.88.1
broadcast 10.19.89.0 dev br-LAN table local proto kernel scope link src 10.19.89.1
local 10.19.89.1 dev br-LAN table local proto kernel scope host src 10.19.89.1
broadcast 10.19.89.255 dev br-LAN table local proto kernel scope link src 10.19.89.1
broadcast 10.19.90.0 dev eth1 table local proto kernel scope link src 10.19.90.21
local 10.19.90.21 dev eth1 table local proto kernel scope host src 10.19.90.21
broadcast 10.19.90.255 dev eth1 table local proto kernel scope link src 10.19.90.21
local X.X.X.X dev MULLVAD table local proto kernel scope host src X.X.X.X
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
unreachable fda8:2149:e3a8::/48 dev lo proto static metric 2147483647 error 4294967183 pref medium
fe80::/64 dev br-LAN proto kernel metric 256 pref medium
fe80::/64 dev eth1 proto kernel metric 256 pref medium
fe80::/64 dev wlan1 proto kernel metric 256 pref medium
fe80::/64 dev br-GUEST proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fe80:: dev br-LAN table local proto kernel metric 0 pref medium
anycast fe80:: dev eth1 table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan1 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-GUEST table local proto kernel metric 0 pref medium
local fe80::20d:b9ff:fe4c:a344 dev eth1 table local proto kernel metric 0 pref medium
local fe80::20d:b9ff:fe4c:a346 dev br-GUEST table local proto kernel metric 0 pref medium
local fe80::6f0:21ff:fe88:4033 dev wlan1 table local proto kernel metric 0 pref medium
local fe80::3832:67ff:fe2c:4f28 dev br-LAN table local proto kernel metric 0 pref medium
ff00::/8 dev br-LAN table local metric 256 pref medium
ff00::/8 dev eth1 table local metric 256 pref medium
ff00::/8 dev wlan1 table local metric 256 pref medium
ff00::/8 dev br-GUEST table local metric 256 pref medium
ff00::/8 dev MULLVAD table local metric 256 pref medium
ip rule show
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
iptables-save
# Generated by iptables-save v1.8.3 on Tue Jan 5 14:00:17 2021
*nat
:PREROUTING ACCEPT [72:6901]
:INPUT ACCEPT [8:562]
:OUTPUT ACCEPT [4:292]
:POSTROUTING ACCEPT [4:256]
:postrouting_WG_FW_rule - [0:0]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_WG_FW_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_WG_FW_postrouting - [0:0]
:zone_WG_FW_prerouting - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-LAN -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i br-GUEST -m comment --comment "!fw3" -j zone_guest_prerouting
-A PREROUTING -i eth1 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i MULLVAD -m comment --comment "!fw3" -j zone_WG_FW_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-LAN -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o br-GUEST -m comment --comment "!fw3" -j zone_guest_postrouting
-A POSTROUTING -o eth1 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o MULLVAD -m comment --comment "!fw3" -j zone_WG_FW_postrouting
-A zone_WG_FW_postrouting -m comment --comment "!fw3: Custom WG_FW postrouting rule chain" -j postrouting_WG_FW_rule
-A zone_WG_FW_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_WG_FW_prerouting -m comment --comment "!fw3: Custom WG_FW prerouting rule chain" -j prerouting_WG_FW_rule
-A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
-A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Jan 5 14:00:17 2021
# Generated by iptables-save v1.8.3 on Tue Jan 5 14:00:17 2021
*mangle
:PREROUTING ACCEPT [1548:364171]
:INPUT ACCEPT [939:172762]
:FORWARD ACCEPT [597:189081]
:OUTPUT ACCEPT [973:228001]
:POSTROUTING ACCEPT [1570:417082]
-A FORWARD -o MULLVAD -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone WG_FW MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i MULLVAD -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone WG_FW MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Jan 5 14:00:17 2021
# Generated by iptables-save v1.8.3 on Tue Jan 5 14:00:17 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_WG_FW_rule - [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_WG_FW_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_WG_FW_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_WG_FW_dest_ACCEPT - [0:0]
:zone_WG_FW_dest_REJECT - [0:0]
:zone_WG_FW_forward - [0:0]
:zone_WG_FW_input - [0:0]
:zone_WG_FW_output - [0:0]
:zone_WG_FW_src_REJECT - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_ACCEPT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-LAN -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i br-GUEST -m comment --comment "!fw3" -j zone_guest_input
-A INPUT -i eth1 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i MULLVAD -m comment --comment "!fw3" -j zone_WG_FW_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-LAN -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i br-GUEST -m comment --comment "!fw3" -j zone_guest_forward
-A FORWARD -i eth1 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i MULLVAD -m comment --comment "!fw3" -j zone_WG_FW_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-LAN -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o br-GUEST -m comment --comment "!fw3" -j zone_guest_output
-A OUTPUT -o eth1 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o MULLVAD -m comment --comment "!fw3" -j zone_WG_FW_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_WG_FW_dest_ACCEPT -o MULLVAD -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_WG_FW_dest_ACCEPT -o MULLVAD -m comment --comment "!fw3" -j ACCEPT
-A zone_WG_FW_dest_REJECT -o MULLVAD -m comment --comment "!fw3" -j reject
-A zone_WG_FW_forward -m comment --comment "!fw3: Custom WG_FW forwarding rule chain" -j forwarding_WG_FW_rule
-A zone_WG_FW_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_WG_FW_forward -m comment --comment "!fw3" -j zone_WG_FW_dest_REJECT
-A zone_WG_FW_input -m comment --comment "!fw3: Custom WG_FW input rule chain" -j input_WG_FW_rule
-A zone_WG_FW_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_WG_FW_input -m comment --comment "!fw3" -j zone_WG_FW_src_REJECT
-A zone_WG_FW_output -m comment --comment "!fw3: Custom WG_FW output rule chain" -j output_WG_FW_rule
-A zone_WG_FW_output -m comment --comment "!fw3" -j zone_WG_FW_dest_ACCEPT
-A zone_WG_FW_src_REJECT -i MULLVAD -m comment --comment "!fw3" -j reject
-A zone_guest_dest_ACCEPT -o br-GUEST -m comment --comment "!fw3" -j ACCEPT
-A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
-A zone_guest_forward -m comment --comment "!fw3: Zone guest to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
-A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
-A zone_guest_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -p udp -m udp --dport 53 -m comment --comment "!fw3: Allow-DNS-Guest" -j ACCEPT
-A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_ACCEPT
-A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
-A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
-A zone_guest_src_ACCEPT -i br-GUEST -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_ACCEPT -o br-LAN -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to WG_FW forwarding policy" -j zone_WG_FW_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-LAN -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o eth1 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth1 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i eth1 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Tue Jan 5 14:00:17 2021