Hey All,
Hoping someone can assist me with a weird issue, I'm having with the MT6000.
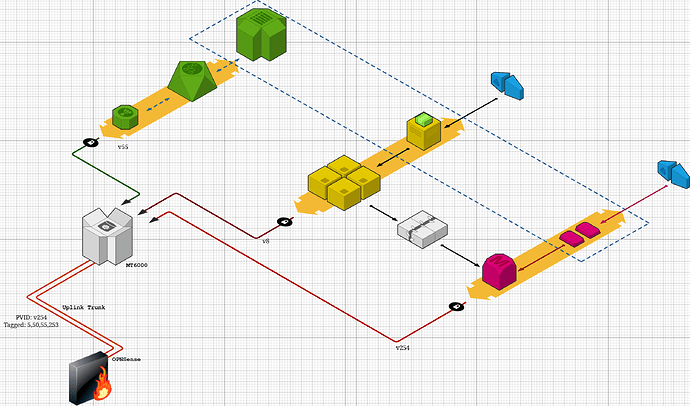
The config I'm going for is:
- Device used in 'Dumb-AP' mode.
- Uplink(trunked) via the WAN port
- Use of LAN1-5 as regular ports that can be trunked or access ports.
- Information on how to (if NEEDED/ Required) disable the firewall, as it's not needed with this config - I've seen some posts suggesting that leaving the fwall enable will not post an issue.
Current Config:
Layout
- VLAN 254: MGMT (privileged VLAN for adminstration)
- VLAN 253: (swMGMT; uplink, PVID; for switches).
- VLAN 5,50,55: VLANs used for assorted purposes.
- DHCP is upstream (via relay), via OPNSense, works as expected.
The WAN port is uplink to a Layer 3 switch, this L3 Switch in turn connects to a core switch, and then uplinked to an OPNSense Firewall.
Note: The other portions of the network work as expected and have been configured as such, for years.
Note++: Additionally, the MT6000, is replacing an MR16 (also running OpenWRT)... replacing as in: the MT6000 is now connected to the same uplink (with the identical PVID, tagging, etc)
Works:
- Dumb AP mode (appears to be configured correctly)
- Uplink config works as expected.
- dhcp relay, vlan tagging (at least for WiFi vlan)
- WiFi works as expected.
- DHCP Relay works as expected.
Issues:
- local DNS(via forwarding) not working as expected.
- unable to ping or resolve local hostnames that are known by upstream dns server
# ping hostname.mt6k ping: bad address 'hostname.mt6k'
- Routing issue...? with respect to opkg updates, install, etc
- opkg update will fail, even though I'm able to ping
downloads.openwrt.orgsuccessfully.
# opkg update Failed to send request: Operation not permitted *** Failed to download the package list from https://downloads.openwrt.org ....
I've tried a couple of configs., all to no avail.
- I've also looked around the forums, but haven't seen anyone with a similar issue.
The current config (see below) is what is intended, but I'd also previously whittled it down to the basics to see if the more complicated config. could be what was causing the issue, but still no go.
Reference Info +Files
# ubus call system board
{
"kernel": "6.6.73",
"hostname": "MT6000",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT6000",
"board_name": "glinet,gl-mt6000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "24.10.0",
"revision": "r28427-6df0e3d02a",
"target": "mediatek/filogic",
"description": "OpenWrt 24.10.0 r28427-6df0e3d02a",
"builddate": "1738624177"
}
}
- file:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd19:e4f2:60c9::/48'
option packet_steering '2'
option steering_flows '128'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
option bridge_empty '1'
option ipv6 '0'
config interface 'swMGMT'
option device 'br-lan.253'
option proto 'static'
option ipaddr 'X.X.253.246'
option netmask '255.255.255.240'
option delegate '0'
option gateway 'X.X.253.254'
list dns_search 'v253.mt6k'
list dns_search 'v253'
list dns_search 'mt6k'
list dns 'X.X.253.254'
list dns 'X.X.254.254'
config bridge-vlan
option device 'br-lan'
option vlan '253'
list ports 'eth1:u*'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4:t'
list ports 'lan5:u*'
config bridge-vlan
option device 'br-lan'
option vlan '254'
list ports 'eth1:t'
list ports 'lan4:u*'
list ports 'lan5:t'
config bridge-vlan
option device 'br-lan'
option vlan '5'
list ports 'eth1:t'
list ports 'lan4:t'
list ports 'lan5:t'
config bridge-vlan
option device 'br-lan'
option vlan '8'
list ports 'eth1:t'
list ports 'lan4:t'
list ports 'lan5:t'
config bridge-vlan
option device 'br-lan'
option vlan '50'
list ports 'eth1:t'
list ports 'lan4:t'
list ports 'lan5:t'
config bridge-vlan
option device 'br-lan'
option vlan '55'
list ports 'eth1:t'
list ports 'lan4:t'
list ports 'lan5:t'
config interface 'I0T'
option proto 'static'
option device 'br-lan.5'
option ipaddr 'X.X.5.246'
option netmask '255.255.255.0'
option gateway 'X.X.5.254'
option delegate '0'
list dns 'X.X.5.254'
list dns 'X.X.254.254'
list dns_search 'v5.mt6k'
list dns_search 'mt6k'
config interface 'WLAN'
option proto 'static'
option device 'br-lan.8'
option ipaddr 'X.X.8.246'
option netmask '255.255.255.0'
option gateway 'X.X.8.254'
option delegate '0'
list dns_search 'v8.mt6k'
list dns_search 'v8'
list dns_search 'mt6k'
list dns 'X.X.4.240'
list dns 'X.X.8.254'
config interface 'Guest'
option proto 'none'
option device 'br-lan.50'
option delegate '0'
option force_link '1'
list dns '1.1.1.2'
list dns '1.0.0.2'
config interface 'i5mart'
option proto 'static'
option device 'br-lan.55'
option ipaddr 'X.X.55.246'
option netmask '255.255.255.0'
option gateway 'X.X.55.254'
list dns_search 'v55.mt6k'
option delegate '0'
list dns 'X.X.55.254'
list dns 'X.X.254.254'
config interface 'MGMT'
option proto 'none'
option device 'br-lan.254'
option force_link '1'
option delegate '0'
list dns 'X.X.254.250'
list dns 'X.X.254.254'
config device
option name 'br-lan.253'
option type '8021q'
option ifname 'br-lan'
option vid '253'
option ipv6 '0'
config device
option name 'br-lan.254'
option type '8021q'
option ifname 'br-lan'
option vid '254'
option ipv6 '0'
config device
option name 'br-lan.55'
option type '8021q'
option ifname 'br-lan'
option vid '55'
option ipv6 '0'
config device
option name 'br-lan.50'
option type '8021q'
option ifname 'br-lan'
option vid '50'
option ipv6 '0'
config device
option name 'br-lan.5'
option type '8021q'
option ifname 'br-lan'
option vid '5'
option ipv6 '0'
config device
option name 'br-lan.8'
option type '8021q'
option ifname 'br-lan'
option vid '8'
option ipv6 '0'
- file:
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/mt6k/'
option domain 'mt6k'
option expandhosts '1'
option cachesize '1000'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '1'
option logqueries '1'
option quietdhcp '1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option dynamicdhcp '0'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config relay
option local_addr 'X.X.8.246'
option server_addr 'X.X.8.254'
config relay
option local_addr 'X.X.55.246'
option server_addr 'X.X.55.254'
config relay
option local_addr 'X.X.253.246'
option server_addr 'X.X.253.254'
config relay
option local_addr 'X.X.254.246'
option server_addr 'X.X.254.254'
config relay
option local_addr 'X.X.5.246'
option server_addr 'X.X.5.254'
- file:
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
- Basic Network Diagram