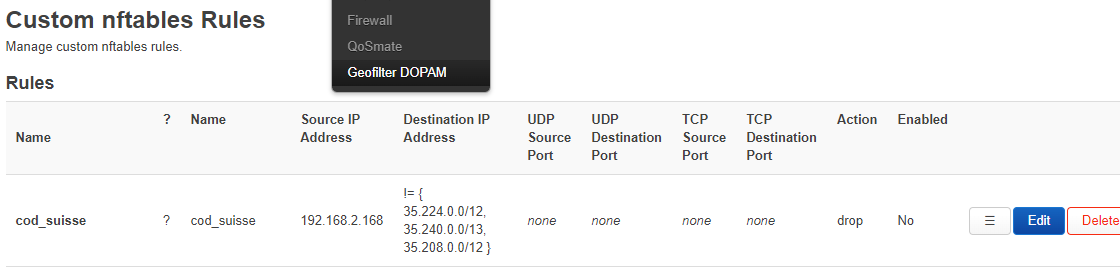
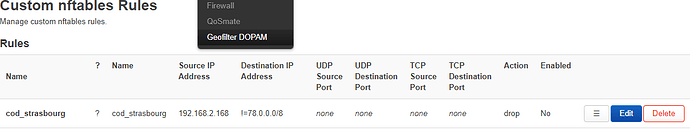
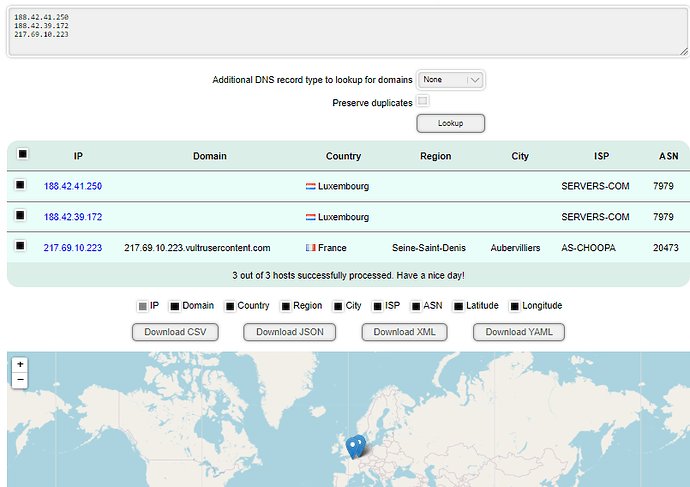
Hello everyone, I recently recreated a geofilter, but I lost the data from my router file. I've recovered some basics, but they are incomplete. I'm sharing them with you as best as I can...
Thank you
1er files place in hotplug.d/iface name : 13-nftables_custom
#!/bin/sh
# Vérifiez si la variable $DEVICE est définie (non vide)
[ -n "$DEVICE" ] || exit 0
# Si l'action est 'ifup', exécuter les commandes suivantes
[ "$ACTION" = ifup ] && {
# Vérifiez si nftables_custom est activé dans la configuration UCI
enabled=$(uci get nftables_custom.global.enabled 2>/dev/null)
if [ "$enabled" = "1" ]; then
# Activez le service nftables_custom au démarrage et redémarrez-le
/etc/init.d/nftables_custom enable
/etc/init.d/nftables_custom restart
# Journaliser l'action effectuée
logger -t nftables_custom "Reloading nftables_custom.sh due to $ACTION of $INTERFACE ($DEVICE)"
else
# Journaliser que nftables_custom est désactivé et aucune action n'a été prise
logger -t nftables_custom "nftables_custom is disabled in the configuration. Not executing the script."
fi
}
2nd files init.d name : nftables_custom
#!/bin/sh /etc/rc.common
START=99
STOP=15
start() {
config_load nftables_custom
# Appliquer les règles dans l'ordre
config_foreach apply_rule rule
}
apply_rule() {
local name ip_saddr ip_daddr udp_dport tcp_dport action enabled
config_get name "$1" name
config_get ip_saddr "$1" ip_saddr
config_get ip_daddr "$1" ip_daddr
config_get udp_dport "$1" udp_dport
config_get tcp_dport "$1" tcp_dport
config_get action "$1" action
config_get enabled "$1" enabled
[ "$enabled" = "1" ] || return
# Construction de la règle
local rule="ip saddr $ip_saddr"
[ -n "$ip_daddr" ] && rule="$rule ip daddr $ip_daddr"
[ -n "$udp_dport" ] && rule="$rule udp dport { $udp_dport }"
[ -n "$tcp_dport" ] && rule="$rule tcp dport { $tcp_dport }"
rule="$rule counter $action"
# Insertion de la règle dans fw4
nft insert rule inet fw4 forward_lan $rule
logger -t nftables_custom "Added rule: $rule"
}
stop() {
# Supprimer toutes les règles ajoutées dans la chaîne forward_lan
nft flush chain inet fw4 forward_lan
# Ajoutez les règles que vous souhaitez conserver dans la chaîne forward_lan
nft insert rule inet fw4 forward_lan jump accept_to_lan
nft insert rule inet fw4 forward_lan jump accept_to_wireguard
nft insert rule inet fw4 forward_lan jump accept_to_vpn
nft insert rule inet fw4 forward_lan jump accept_to_wan
}
### is important to place in orderthe rule lan because lost internet after my memories
3rd files usr/share/luci/menu.d/luci-app-nftables_custom
{
"admin/network/nftables_custom": {
"title": "Geofilter DOPAM",
"order": 80,
"action": {
"type": "firstchild"
},
"depends": {
"acl": [ "luci-app-nftables_custom" ],
"uci": { "nftables_custom": true }
}
},
"admin/network/nftables_custom/rules": {
"title": "Rules",
"order": 10,
"action": {
"type": "view",
"path": "nftables_custom/rules"
}
}
}
4eme files usr/share/rpcd/acl.d/luci-app-nftables_custom
{
"luci-app-nftables_custom": {
"description": "Grant access to nftables custom configuration",
"read": {
"ubus": {
"luci.nftables_custom": [ "getNftablesStats", "listRules" ],
"luci": [ "getInitList", "setInitAction", "getInitActionStatus", "exec" ]
},
"uci": [ "nftables_custom" ],
"file": {
"/etc/config/nftables_custom": [ "read" ],
"/etc/init.d/nftables_custom": [ "read", "exec" ],
"/etc/nftables_custom.sh": [ "read" ],
"/etc/hotplug.d/iface/13-nftables_custom": [ "read" ],
"/tmp/nftables_custom_output.txt": [ "read" ]
}
},
"write": {
"ubus": {
"luci": [ "setInitAction", "exec" ]
},
"uci": [ "nftables_custom" ],
"file": {
"/etc/config/nftables_custom": [ "write" ],
"/etc/init.d/nftables_custom": [ "write", "exec" ],
"/etc/nftables_custom.sh": [ "write" ],
"/etc/hotplug.d/iface/13-nftables_custom": [ "write" ]
}
}
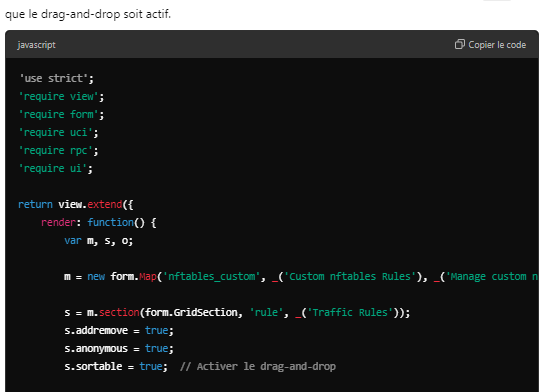
5eme files www/luci-static/resources/view/nftables_custom/rules.js
'use strict';
'require view';
'require form';
'require uci';
'require rpc';
'require ui';
return view.extend({
render: function() {
var m, s, o;
m = new form.Map('nftables_custom', _('Custom nftables Rules'), _('Manage custom nftables rules. Drag and drop to reorder.'));
s = m.section(form.GridSection, 'rule', _('Traffic Rules'));
s.addremove = true;
s.anonymous = true;
s.sortable = true; // Activer le drag-and-drop
// Ajouter la colonne avec les trois traits pour le drag-and-drop
o = s.option(form.DummyValue, '_move', _('☰')); // Symbole unicode représentant les trois traits
o.rawhtml = true;
o.cfgvalue = function() {
return '☰'; // Affiche le symbole de trois traits pour drag-and-drop
};
// Nom de la règle
o = s.option(form.Value, 'name', _('Name'));
o.rmempty = false; // Le champ ne doit pas être vide
o.datatype = 'string'; // Assurez-vous que c'est du texte
// Adresse IP source
o = s.option(form.Value, 'ip_saddr', _('Source IP Address'));
o.placeholder = '0.0.0.0/0';
// Adresse IP destination
o = s.option(form.Value, 'ip_daddr', _('Destination IP Address'));
o.placeholder = '0.0.0.0/0';
// Ports UDP
o = s.option(form.Value, 'udp_dport', _('UDP Destination Port'));
o.placeholder = '53, 80, 443, etc.';
// Ports TCP
o = s.option(form.Value, 'tcp_dport', _('TCP Destination Port'));
o.placeholder = '53, 80, 443, etc.';
// Action sur les règles
o = s.option(form.ListValue, 'action', _('Action'));
o.value('accept', _('Accept'));
o.value('drop', _('Drop'));
o.value('reject', _('Reject'));
// Activer ou désactiver la règle
o = s.option(form.Flag, 'enabled', _('Enabled'));
o.default = '1';
o.rmempty = false;
return m.render();
}
});