READ ENTIRE GUIDE BEFORE YOU BEGIN
This Tutorial / Guide Was Updated on Jan 19 2020
in order to keep you in step with changes needed for OpenWrt 19.07.0
For those who want to obtain full new updated upstream DOT Server List and Keys August 21 2020
see here below :
https://forums.torguard.net/index.php?/topic/1861-openwrt-new-and-improved-getdns-stubby-and-unbound-aka-dns-privacy/
NOW ! is the time for all of US ( A ) to GET UP & GET INVLOVED and act with SOUL POWER ! - lyrics : https://genius.com/James-brown-get-up-get-into-it-get-involved-lyrics plus https://genius.com/James-brown-soul-power-lyrics and video : https://www.youtube.com/watch?v=1pvIarW3xHg Bonus JB : https://www.youtube.com/watch?v=v8TvBPshngE
"I recommend Unbound to utilize the caching. Sometimes the connections from stubby to the resolver can have a little but of lag, so caching + prefetch helps minimize the effects."
A small number have questioned DNS OVER TLS and the supposed complexity of this setup vis a’ vis DNSCrypt. DNSCrypt has always been suggested to best deployed when forwarded to Unbound as a Caching Server. In effect, this methodology simply drops Stubby and GetDns in place instead of DNSCrypt. The use of DNSMasq for DHCP is particular to OpenWRT / LEDE. However, it is a fairly simple and straightforward task to setup DNSMasq for purposes of DHCP and well described and referenced in this tutorial. Lastly, GetDns and Stubby do allow for TLS OVER Port 443 ; I have amended this guide for those who may worry about being blocked behind a firewall while using TLS OVER Port 853.**
https://www.nlnetlabs.nl/projects/unbound/about/
Why DNS OVER TLS is all the rage - read this:
https://tenta.com/blog/post/2017/12/dns-over-tls-vs-dnscrypt So here we go.
GETDNS and STUBBY - this method is the one recommended by DNSPRIVACY - see here :
https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Clients#DNSPrivacyClients-Unbound - please read this carefully - you will note that it indicates :
Unbound As A DNS TLS Client Features:
Unbound can be run as a local caching forwarder, configured to use SSL upstream, however it cannot yet authenticate upstreams, re-use TCP/TLS connections, be configured for Opportunistic mode or send several of the privacy related options (padding, ECS privacy) etc. Some users combine Unbound (as a caching proxy with other features such as DNS Blacklisting) and Stubby (as a fully featured TLS forwarder).
I was asked by a still skeptical devotee of DOH
" What makes this way better than just running the DNS-over-https-proxy ?
My answer was : Read this and make your
decisions and conclusions concerning DOH vs DOT .
Here is the article below :
Bottom Line Conclusion From Jan Schaumann - The Author of This Blog Entry :
For that, my current preference is quite clearly DNS-over-TLS:
I fear a bifurcation of DNS resolution by apps combined with the
push for using public resolvers with DoH will lead to a more complex
environment and threat model for many users.
Short Synopsis of DOH:
In other words , ( with DOH ) we gain the same
protections as with DoT for our web applications,
but leaves all other DNS traffic vulnerable.
Subsequently, as a matter of fact and in practice
with DNS OVER TLS ALL DNS traffic is invulnerable
and protected.This is why I run DOT and
eschew DOH on my OPNsense Router.
Further, Personally, I run GETDNS STUBBY and UNBOUND as
described here along with ( wait for it )
FireFox DOH along with Encrypted SNI - plus TLS v 1.3 in Stubby
and naturally a properly configured and encrypted VPN -
Basic guide as to how to do it -
https://blog.grobox.de/2018/what-is-dns-privacy-and-how-to-set-it-up-for-openwrt/
Modifications are necessary in order to to have GetDns and Stubby up and running and successfully integrated with Unbound DNS and Dnsmasq for DHCP.
As always - opkg update
first and foremost
Prerequisite
You have a ca cert bundle installed on your router.
You can do this by running the following
opkg install ca-certificates
Now Let’s Move On
1 - opkg update ; opkg install unbound-daemon-heavy unbound-control unbound-control-setup luci-app-unbound unbound-anchor unbound-host unbound-checkconf odhcpd
2 - opkg update ; opkg install stubby getdns
3- My WORKING CONFIGS /etc/unbound/unbound_srv.conf
( Adjust For Your Router )
** "Optimize Unbound " - increase size of cache among other things see guide here and adjust for your router's memory , number of cores and so on-**
see here: https://nlnetlabs.nl/documentation/unbound/howto-optimise/
cat >> /etc/unbound/unbound_srv.conf <<UNBOUND_SERVER_CONF
server:
# use all CPUs
num-threads: 2
# power of 2 close to num-threads
msg-cache-slabs: 4
rrset-cache-slabs: 4
infra-cache-slabs: 4
key-cache-slabs: 4
# more cache memory, rrset=msg*2
rrset-cache-size: 256m
msg-cache-size: 128m
# more outgoing connections
# depends on number of cores: 1024/cores - 50
outgoing-range: 8192
# Larger socket buffer. OS may need config.
so-rcvbuf: 4m
so-sndbuf: 4m
cache-min-ttl: 3600
cache-max-ttl: 86400
hide-identity: yes
hide-version: yes
hide-trustanchor: yes
harden-glue: yes
harden-dnssec-stripped: yes
infra-cache-numhosts: 100000
num-queries-per-thread: 4096
max-udp-size: 3072
minimal-responses: yes
rrset-roundrobin: yes
use-caps-for-id: no
do-ip6: no
do-ip4: yes
do-tcp: yes
do-udp: yes
prefetch: yes
prefetch-key: yes
qname-minimisation: yes
qname-minimisation-strict: yes
harden-below-nxdomain: yes
aggressive-nsec: yes
so-reuseport: yes
unwanted-reply-threshold: 10000000
interface-automatic: yes
verbosity: 1
private-domain: "your.domain" ## put your domain here
do-not-query-localhost: no
harden-referral-path: yes
target-fetch-policy: "0 0 0 0 0"
val-clean-additional: yes
ip-ratelimit: 300
ip-ratelimit-factor: 10
incoming-num-tcp: 100
edns-buffer-size: 1472
UNBOUND_SERVER_CONF
As per guide :# Don’t let each server know the next recursion
Enter via SSH command line:
uci set ‘unbound.@unbound[0].query_minimize=1’
To keep this simple - go into default UCI STUBBY file which is /etc/config/stubby by entering nano /etc/config/stubby and then set option manual '1' - if you leave it at default setting of option manual 'o' you will not be able to use the /etc/stubby/stubby.yml file in order to configure STUBBY as before. So, after changing option manual '1' in the /etc/config/stubby file - configure /etc/stubby/stubby.yml as follows :
4 - My WORKING CONFIG /etc/stubby/stubby.yml --
nano /etc/stubby/stubby.yml - replace contents of file with configuration below:
Proper Configuration Examples For Non- Readable Options:
VERY IMPORTANT UPDATE:
I strongly suggest you only choose to deploy servers which support the TLSv1.3 protocol . See here for information and importance of TLSv1.3 : https://kinsta.com/blog/tls-1-3/ 1
I will save you some considerable leg work and post below the best configuration for your stubby.yml file. Here it is:
# All DNS Privacy Servers Below Tested and Updated On June 30 2020 With A+ Rating -
# 100% Perfecto Configuration on website: https://www.immuniweb.com/ssl/?id=Su8SeUQ4n
# These servers support the most recent and secure TLS protocol version of TLS 1.3 **
# see country code lists here :
# https://www.nationsonline.org/oneworld/country_code_list.htm and / or
# https://www.iban.com/country-codes
# Use as many or as few depending on your specific needs
resolution_type: GETDNS_RESOLUTION_STUB
round_robin_upstreams: 1
appdata_dir: "/var/lib/stubby"
tls_authentication: GETDNS_AUTHENTICATION_REQUIRED
tls_query_padding_blocksize: 128
edns_client_subnet_private: 1
idle_timeout: 9000
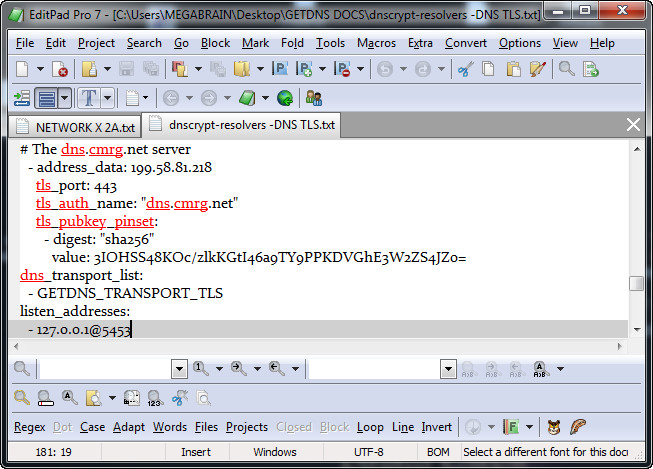
listen_addresses:
- 127.0.0.1@5453
dns_transport_list:
- GETDNS_TRANSPORT_TLS
tls_connection_retries: 5
tls_backoff_time: 900
timeout: 2000
tls_ca_path: "/etc/ssl/certs/"
upstream_recursive_servers:
### IPV4 Servers ###
### DNS Privacy DOT Test Servers ###
## 1 - The getdnsapi.net DNS TLS Server A+ ( NLD )
- address_data: 185.49.141.37
tls_auth_name: "getdnsapi.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: foxZRnIh9gZpWnl+zEiKa0EJ2rdCGroMWm02gaxSc9Q=
## 2 - The Surfnet/Sinodun DNS TLS Server #3 A+ ( NLD )
- address_data: 145.100.185.18
tls_port: 853
tls_auth_name: "dnsovertls3.sinodun.com"
tls_pubkey_pinset:
- digest: "sha256"
value: 5SpFz7JEPzF71hditH1v2dBhSErPUMcLPJx1uk2svT8=
## 3 - The dns.cmrg.net DNS TLS Server A+ ( CAN )
- address_data: 199.58.81.218
tls_auth_name: "dns.cmrg.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 3IOHSS48KOc/zlkKGtI46a9TY9PPKDVGhE3W2ZS4JZo=
## 4 - The BlahDNS Japan DNS TLS Server A+ ( JPN )
- address_data: 45.32.55.94
tls_auth_name: "dot-jp.blahdns.com"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: gIoiNFxX1Nw+7/pVsmUKBU941bMBYjEYuB2T9drULOM=
## 5 - The BlahDNS German DNS TLS Server A+ ( USA Hosted In DEU )
- address_data: 159.69.198.101
tls_auth_name: "dot-de.blahdns.com"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: YZeyeJf/suAR2fMHLc9RDPkcQi/e8EEnzk5Y1N90QQE=
## 6 - The BlahDNS Finland DNS TLS Server A+ ( FIN )
- address_data: 95.216.212.177
tls_auth_name: "dot-fi.blahdns.com"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: PID8ufrN/lfloA6y/C+mpR8MT53GG6GkAd8k+RmgTwc=
## 7 - The dns.neutopia.org DNS TLS Server A+ ( FRA )
- address_data: 89.234.186.112
tls_auth_name: "dns.neutopia.org"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: wTeXHM8aczvhRSi0cv2qOXkXInoDU+2C+M8MpRyT3OI=
## 8 - The Foundation for Applied Privacy DNS TLS Server #1 A+ ( AUT )
- address_data: 94.130.106.88
tls_auth_name: "dot1.applied-privacy.net"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: 78kfbZFJaxGrAl+0hkiyWER0ajTgFL/KxMAZQHSNhWU=
## 9 - The Foundation for Applied Privacy DNS TLS Server #2 A+ ( AUT )
- address_data: 93.177.65.183
tls_auth_name: "dot1.applied-privacy.net"
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: 78kfbZFJaxGrAl+0hkiyWER0ajTgFL/KxMAZQHSNhWU=
## 10 - The Secure DNS Project by PumpleX DNS TLS Server #1 A+ ( GBR )
- address_data: 51.38.83.141
tls_auth_name: "dns.oszx.co"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: Bd5frvFVxtk4ru8L7JozLol7dn80YDTaP8b3yU06JB8=
## 11 - The Rubyfish Internet Tech DNS TLS Server A+ ( CHN )
- address_data: 115.159.131.230
tls_auth_name: "dns.rubyfish.cn"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: DBDigty3zDS7TN/zbQOmnjZ0qW+qbRVzlsDKSsTwSxo=
## 12 - The Lorraine Data Network DNS TLS Server A+ ( FRA )
- address_data: 80.67.188.188
tls_port: 443
tls_pubkey_pinset:
- digest: "sha256"
value: WaG0kHUS5N/ny0labz85HZg+v+f0b/UQ73IZjFep0nM=
## This certificate is currently expired which
## does not pose any concerns in SPKI mode
## (in practice with Stubby)
## Source : https://ldn-fai.net/serveur-dns-recursif-ouvert/
## 13 - The DNSPRIVACY.at TLS Server #1 A+ ( DEU )
- address_data: 94.130.110.185
tls_auth_name: "ns1.dnsprivacy.at"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: MjA0IXWNt3+LCmuKT9ewjX3PwJxNqs2RoTa/NmzPHwI=
## 14 - The DNSPRIVACY.at TLS Server #2 A+ ( DEU ) - expired 2020-04-01
- address_data: 94.130.110.178
tls_auth_name: "ns2.dnsprivacy.at"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 68MH4G5hipbK1xYATBFgA+/DNLDd333oXr22QyB/RRo=
# 15 - The ibksturm.synology.me DNS TLS Server A+ ( CHE )
- address_data: 85.5.93.230
tls_auth_name: "ibksturm.synology.me"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: npNOnBcLbvZWZgdmcuFaEqYJbaGjBlHMf9DknDoIkgg=
## 16 - The dns.flatuslifir.is DNS TLS Server A+ ( ISL )
- address_data: 46.239.223.80
tls_auth_name: "dns.flatuslifir.is"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 3QPTZIcJdZFCx5t3tZiqdCBYpigUX+1Gwz+iQfLXrJE=
### Publicly Available DOT Test Servers ###
## 17 - The ContainerPI.com - CPI DNS TLS Server A+ ( JPN )
- address_data: 45.77.180.10
tls_auth_name: "dns.containerpi.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: xz8kGlumwEGkPwJ3QV/XlHRKCVNo2Fae8bM5YqlyvFs=
## 18 - The FEROZ SALAM DNS TLS Server A+ ( GBR )
- address_data: 46.101.66.244
tls_auth_name: "doh.li"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: VEjC/umyfulb4CbLZ6mIyEqHPbwv0D6osfrUbi8Dm28=
## 19 - The Andrews & Arnold DNS TLS Server #1 A+ ( GBR )
- address_data: 217.169.20.23
tls_auth_name: "dns.aa.net.uk"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 41OknyzhvFDNZqlvTs4mFTWSkAXSPXWQ4wRgky5Qyzc=
## 20 - The Andrews & Arnold DNS TLS Server #2 A+ ( GBR )
- address_data: 217.169.20.22
tls_auth_name: "dns.aa.net.uk"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: I88W3UOUiCa+1KMukcoys2FtyL93GAKalO1EW7iOZJk=
## 21 - The dns.seby.io - Vultr DNS TLS Server A+ ( AUS )
- address_data: 45.76.113.31
tls_auth_name: "dot.seby.io"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: H13Su1659zEn0ZIblEShwjZO+M5gxKK2wXpVKQHgibM=
## 22 - The dns.seby.io - OVH DNS TLS Server A+ ( AUS )
- address_data: 139.99.222.72
tls_auth_name: "dot.seby.io"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 8A/1KQQiN+aFWenQon076nAINhlZjGkB15C4E/qogGw=
## 23 - The Digitale Gesellschaft DNS TLS Server #1 A+ ( CHE )
- address_data: 185.95.218.43
tls_auth_name: "dns.digitale-gesellschaft.ch"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: S+DuqASQtCTm8qr4G9z53uLEy230lIDgbHl9AtId0Yw=
## 24 - The Digitale Gesellschaft DNS TLS Server #2 A+ ( CHE )
- address_data: 185.95.218.42
tls_auth_name: "dns.digitale-gesellschaft.ch"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: bthpji8smy3f2lSvweu5hXpb/6hLrk3Txh6euWztF5Q=
## 25 - The Antoine Aflalo DNS TLS Server #1 A+ ( USA )
- address_data: 168.235.81.167
tls_auth_name: "dns-nyc.aaflalo.me"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: kjMUEH0kNEaZ4cDn3SQV/vANgycPm0qRPMU2yd4OlT0=
## 26 - The Privacy-First DNS TLS Server #1 A+ ( JPN )
- address_data: 172.104.93.80
tls_auth_name: "jp.tiar.app"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 6PiLZvmKVJKLekrweBWO1tjRmratPGWkadjsicFXAlU=
## 27 - The Privacy-First DNS TLS Server #2 A+ ( SGP Hosted In USA )
- address_data: 174.138.29.175
tls_auth_name: "dot.tiar.app"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 5hG9dlXtWeLWdCfE4QdNWlalxlFITtt8c2YgZVaCNWQ=
## 28 - The ibuki.cgnat.net DNS TLS Server A+ ( USA )
- address_data: 35.198.2.76
tls_auth_name: "ibuki.cgnat.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: C+ximOx14NAMAWq9TvgT1irRs2R37MnECtGBTO1OOYU=
## 29 - The PI-DNS.COM West USA DNS TLS Server A+ ( USA )
- address_data: 45.67.219.208
tls_auth_name: "dot.westus.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: tfdCeUhPuPGyufMk1O1m8wMirCGpuS/chiAUyRCkBmY=
## 30 - The PI-DNS.COM DNS TLS East USA Server A+ ( USA )
- address_data: 185.213.26.187
tls_auth_name: "dot.eastus.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: PDuAjVfbR5apthM4n0c1LzcmJH/aBd4SAqpnnt4Bmy4=
## 31 - The PI-DNS.COM Central Europe DNS TLS Server A+ ( DEU )
- address_data: 88.198.91.187
tls_auth_name: "dot.centraleu.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 9rEHDwaRyQf/NFX6OH2gyJOrPg6ZABeEQ2PIXgrgyyE=
## 32 - The PI-DNS.COM North Europe DNS TLS Server A+ ( FIN )
- address_data: 95.216.181.228
tls_auth_name: "dot.northeu.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: gouwOSAsY4GvTHhm1aai15Xt8+L84199aAVN3CrWsiI=
## 33 - The PI-DNS.COM East Australia DNS TLS Server A+ ( AUS )
- address_data: 45.63.30.163
tls_auth_name: "dot.eastau.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: TFNiPxVz7a1gxDV5x8i6zY3gvEFL/o99zgmwc79KrTs=
## 34 - The PI-DNS.COM East Asia DNS TLS Server A+ ( USA )
- address_data: 66.42.33.135
tls_auth_name: "dot.eastas.pi-dns.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: XDrRwtqxJgnvmBoWZrD9QE1QAjF74qPWnBv2UJ4Wkgg=
## 35 - The Snopyta DNS TLS Server A+ ( FIN )
- address_data: 95.216.24.230
tls_auth_name: "fi.dot.dns.snopyta.org"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: cYf+8BXhzbBmQe6qP+BHzLb2UZ/rgOspuyCmk2aVhlE=
## 36 - The NixNet Uncensored Las Vegas DNS TLS Server A+ ( USA )
## - or use ( tls_auth_name: "adblock.lv1.dns.nixnet.xyz" )
- address_data: 209.141.34.95
tls_auth_name: "uncensored.lv1.dns.nixnet.xyz"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: flpUestk4tYCQ1wB3WP5sIztvRIOiAPLKCtVqbM/SJ8=
## 37 - The NixNet Uncensored New York DNS TLS Server A+ ( USA )
## - or use ( tls_auth_name: "adblock.ny1.dns.nixnet.xyz" )
- address_data: 199.195.251.84
tls_auth_name: "uncensored.ny1.dns.nixnet.xyz"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: cXriM10X2+lW6V8NOrMZd2nssgC1TeW2DutGlmMn5fc=
## 38 - The NixNet Uncensored Luxembourg DNS TLS Server A+ ( LUX )
## - or use ( tls_auth_name: "adblock.lux1.dns.nixnet.xyz" )
- address_data: 104.244.78.231
tls_auth_name: "uncensored.lux1.dns.nixnet.xyz"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 7cOZUgpjYw3Qy5K97ww3APnMau8zHrIEbC0znGgEGyw=
## 39 - The Lelux.fi DNS TLS Server A+ ( FRA Hosted In GBR )
- address_data: 51.158.147.50
tls_auth_name: "resolver-eu.lelux.fi"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 77zOtPEiiEnIEliuHySTchfWbyfCV+nfHeejrN0gzpM=
## 40 - The Lightning Wire Labs DNS TLS Server A+ ( DEU )
- address_data: 81.3.27.54
tls_auth_name: "recursor01.dns.lightningwirelabs.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: jVdEaKPP27O6wPq6wbvXrTtDsDEiOoVdyTY9uUHXDJ0=
## 41 - The Hostux DNS TLS Server A+ ( LUX )
- address_data: 185.26.126.37
tls_auth_name: "dns.hostux.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: P0gaP31TQQzAIN3DomM5vXS3+8oCgYcTA/ZJ09Jw4QE=
## 42 - The dnsforge.de DNS TLS Server #1 A+ ( DEU )
- address_data: 176.9.1.117
tls_auth_name: "dnsforge.de"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: m51QwAhzNDSa3G7c1Y6eOEsskzp6ySzeOqy0LKcptDw=
## 43 - The dnsforge.de DNS TLS Server #2 A+ ( DEU )
- address_data: 176.9.93.198
tls_auth_name: "dnsforge.de"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: m51QwAhzNDSa3G7c1Y6eOEsskzp6ySzeOqy0LKcptDw=
# 44 - The Freifunk München DNS TLS Server A+ ( DEU )
- address_data: 195.30.94.28
tls_auth_name: "doh.ffmuc.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: 1swf1Y7mDE9KBYARlBG00o5sQ7zZjOGSb0ahWpaKV5M=
# 45 - The doh.defaultroutes.de DNS TLS Server A+ ( DEU )
- address_data: 5.45.107.88
tls_auth_name: "doh.defaultroutes.de"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: p7t6DDebAlM1rwkrJgZJ6CDkuJG0Ff5PKYZ8bUPQCM0=
## 46 - The CIRA Canadian Shield DNS TLS Servers A+ ( CAN )
- address_data: 149.112.121.10
tls_auth_name: "private.canadianshield.cira.ca"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: sXmZXPsnkbQMw68THpV0Tgh9zCe12TtXIinSTf7lkkw=
- address_data: 149.112.122.10
tls_auth_name: "private.canadianshield.cira.ca"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: sXmZXPsnkbQMw68THpV0Tgh9zCe12TtXIinSTf7lkkw=
# 47 - The dns.dnshome.de DNS TLS Server #1 A+ ( DEU )
- address_data: 185.233.106.232
tls_auth_name: "dns.dnshome.de"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: q5AkxgnWVCVjCUNUKl3aIBpGTfXF5GahE0RcncwbZoc=
- address_data: 185.233.107.4
tls_auth_name: "dns.dnshome.de"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: q5AkxgnWVCVjCUNUKl3aIBpGTfXF5GahE0RcncwbZoc=
## 48 - The Usable Privacy DNS TLS Server A+ ( DEU / AUT )
- address_data: 149.154.153.153
tls_auth_name: "adfree.usableprivacy.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: VEmtR6+zgZ2mcyEI0NvpDCFhijAoawwKbStKYTj+774=
## 49 - The DeCloudUs DNS TLS Server A+ ( DEU )
- address_data: 176.9.199.152
tls_auth_name: "dot.decloudus.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: L/QUBSkq/goTWjGgW7DjC29IoSdaqrVYGG5ME7lJYMo=
## 50 - The Hurricane Electric DNS TLS Server A+ ( USA )
- address_data: 74.82.42.42
tls_auth_name: "ordns.he.net"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: G9pQNrYB98Wll0AmBF/GsMMn6gaDbXDnInV1je1MaPo=
### Anycast Publicly Available DOT Test Servers ###
## 51 - The NixNet Uncensored Anycast DNS TLS Servers ( Anycast )
- address_data: 198.251.90.114
tls_auth_name: "uncensored.any.dns.nixnet.xyz"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: Ryhjf7K6V9/Fw/7XU7fqzrVJVEOyPtlHR/rFetOXrug=
- address_data: 198.251.90.89
tls_auth_name: "adblock.any.dns.nixnet.xyz"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: Ryhjf7K6V9/Fw/7XU7fqzrVJVEOyPtlHR/rFetOXrug=
## 52 - The DNSlify DNS TLS Servers A+ ( Anycast )
- address_data: 185.235.81.1
tls_auth_name: "doh.dnslify.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: w5AEEaNvoBOl4+QeDIuRaaL6ku+nZfrhZdB2f0lSITM=
- address_data: 185.235.81.2
tls_auth_name: "doh.dnslify.com"
tls_port: 853
tls_pubkey_pinset:
- digest: "sha256"
value: w5AEEaNvoBOl4+QeDIuRaaL6ku+nZfrhZdB2f0lSITM=
# Set the acceptable cipher for DNS over TLS1.3. OpenSSL >= 1.1.1 is required
# for this option. This option can also be given per upstream.
tls_ciphersuites: "TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256"
# Set the minimum acceptable TLS version. Works with OpenSSL >= 1.1.1 only.
# This option can also be given per upstream.
tls_min_version: GETDNS_TLS1_3
In order for TLSv1.3 protocol to work properly ( read at all ) in your Stubby
instance, OpenWrt must have OpenSSL 1.1.1 active and configured in the kernel.
The operative lines necessary are these two specifically found at the bottom
of the stubby.yml file above:
tls_ciphersuites: "TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256"
tls_min_version: GETDNS_TLS1_3
See below for TLS1.3 Support Check SSH Commands -
openssl s_client 168.235.81.167:853
OR :
openssl s_client 159.69.198.101:443
Read Out Will Be Verified By These Lines Below:
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_CHACHA20_POLY1305_SHA256
OR :
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Depending on Configuration on Tested DOT Server
PS - Lastly, this new DNS OVER TLS provider.
You need to sign up and use configured settings.
NextDNS is a free service - ANYCAST and pretty much cutting edge.
ANYCAST speeds up your DNS - Here it is:
NextDNS https://my.nextdns.io/signup
or feel free to use and test
NextDNS " Try it now for free " Feature
go to : https://nextdns.io/
I also strongly encourage you to subscribe to blockerDNS found here : https://blockerdns.com/
This new DOH / DNS OVER TLS provider is the fastest I have run across. blockerDNS is run by
Tambe Barsbay a seasoned, thorough and extremely proficient tech practitioner.
blockerDNS is based in the U.S. and its infrastructure is hosted on Google Cloud Platform
and DigitalOcean. You can view blockerDNS subscription options here : https://blockerdns.com/tryit -
Most significantly, Tambe stands by his claim that he offers " Instant support by phone or email ".
Overall blockerDNS is a great DNSPRIVACY DNS Service. Tip : The Mobile $0.99 per month option should suffice for most home users. Links : https://tambeb.com/ https://blockerdns.com/blog
https://blockerdns.com/support https://blockerdns.com/overview
DNS query name minimisation to improve privacy, along with DNS resolution speed and accuracy -
Run Test After Completing Full Setup
A - You need to opkg install drill and - then run command : drill txt qnamemintest.internet.nl
and / or
B - opkg install bind-dig or opkg install bind-tools with command: dig txt qnamemintest.internet.nl +short and / or dig -t txt qnamemintest.internet.nl
The results in any of these scenarios will show either:
"HOORAY - QNAME minimisation is enabled on your resolver :)!”
or “NO - QNAME minimisation is NOT enabled on your resolver :(.”
Reference https://discourse.pi-hole.net/t/unbound-and-qname-minimisation/10038/4
You will and should get HOORAY ! - if you used the name servers listed in this guide.
5 - MY WORKING CONFIG /etc/unbound/unbound_ext.conf
( Simply Copy and Paste Into Your SSH Session and Hit Enter )
cat >> /etc/unbound/unbound_ext.conf <<UNBOUND_FORWARD_CONF
forward-zone:
name: "." # Allow all DNS queries
forward-addr: 127.0.0.1@5453 # Forward Unbound To Stubby Address/Port
UNBOUND_FORWARD_CONF
6 - From The Guide referred to in the link above - self explanatory: # Move dnsmasq to port 53535 where it will still serve local DNS from DHCP# Network -> DHCP & DNS -> Advanced Settings -> DNS server port to 53535
Enter via SSH command line:
uci set ‘dhcp.@dnsmasq[0].port=53535’
uci add_list “dhcp.lan.dhcp_option=option:dns-server,$(uci get network.lan.ipaddr)”
uci set ‘unbound.@unbound[0].dhcp_link=dnsmasq’
uci commit
/etc/init.d/unbound restart
7 - From https://github.com/openwrt/packages/tree/master/net/unbound/files HOW TO Integrate with DHCP
Parallel DNSMASQ
I referred to this guide:
Go to this section near bottom of page.
Use specific DNS server to lookup one or more host names
https://www.leowkahman.com/2016/05/23/openwrt-encrypted-dns-lookup-using-multiple-dnscrypt-servers/
option noresolv ‘1’ is to prevent using any upstream DNS server other than those specified in this file # this file being: /etc/config/dhcp
Solution is as follows add these two lines to /etc/config/dhcp:
nano /etc/config/dhcp - enter these lines before / option domain ‘yourdomain’
list server '127.0.0.1#5453' # Stubby/Unbound Default Address/Port
option noresolv ‘1’ # Make sure to change this as indicated
or Via Uci
uci add_list dhcp.@dnsmasq[-1].server='127.0.0.1#5453'
uci set dhcp.@dnsmasq[-1].noresolv=1
uci commit && reload_config
7A - Disable Sending DNS Requests to ISP Provided DNS Servers
uci set network.wan.peerdns='0'
uci set network.wan.dns='127.0.0.1'
uci commit && reload_config
After you complete all the steps in this tutorial and restart your Router Check Status > System Log - You will find an entry like the one below:
daemon.info dnsmasq[8532]: using nameserver 127.0.0.1#5453 - which indicates that your OpenWrt Router is using Unbound and Stubby for Encrypted DNS Resolution
8 - Working /etc/config/unbound file
nano /etc/config/unbound
config unbound
option add_extra_dns '0'
option add_local_fqdn '1'
option add_wan_fqdn '0'
option dhcp4_slaac6 '0'
option dns64 '0'
option dns64_prefix '64:ff9b::/96'
option domain "your.domain" ## put your domain here
option domain_type 'static'
option edns_size '1280'
option extended_stats '1'
option hide_binddata '1'
option extended_luci '1'
option luci_expanded '1'
option listen_port '53'
option localservice '1'
option manual_conf '0'
option protocol 'ip4_only'
option query_min_strict '1'
option rebind_localhost '0'
option rebind_protection '1'
option recursion 'default'
option resource 'medium'
option root_age '28'
option ttl_min '120'
option unbound_control '2'
option validator '1'
option validator_ntp '1'
option verbosity '2'
list trigger_interface 'lan'
list trigger_interface 'wan'
option query_minimize '1'
option dhcp_link 'dnsmasq'
VERY IMPORTANT STEP:
Now run /etc/init.d/unbound restart one more time. When you do this you will see that your unbound root.key will be installed to /var/lib/unbound/root.key and also it will install root.key to /etc/unbound/root.key. This will automatically configure DNSSEC on your router. The function also lists your auto-trust anchor in your /var/lib/unbound/unbound.conf file.
You will now be running DNS OVER TLS with GETDNS and Stubby on LEDE / OpenWrt
Make sure to follow this guide precisely and it works GREAT!!!
Peace and God Bless - My Pleasure For You and The Entire Community -
You can install - opkg install bind-dig or opkg install bind-tools order to be able to issue dig commands in order to check DNS resolution if you opt to - as you test you will see that your cache is working also.
VERY IMPORTANT TIP:
Please note that right at the top of the main DNS Privacy Test Servers Homepage ( https://dnsprivacy.org/wiki/display/DP/DNS+Privacy+Test+Servers ) It Ominously Declares:
DoT servers
The following servers are experimental DNS-over-TLS servers.
Also note that the single SPKI pins published here for many of these servers are subject to change (e.g on Certificate renewal) and should be used with care!!
For these reasons it is most important to check and verify your SPKI pin(s) for TLS authentication manually yourself from time to time.
Most Simple and Direct Method:
gnutls-cli --print-cert -p 853 159.69.198.101 | grep "pin-sha256" | head -1
And / Or With Adjustment For SSL Port and Address Being Tested
gnutls-cli --print-cert -p 443 159.69.198.101 | grep "pin-sha256" | head -1 - where you must opkg install gnutls
OR
echo | openssl s_client -connect '185.49.141.37:853' 2>/dev/null | openssl x509 -pubkey -noout | openssl pkey -pubin -outform der | openssl dgst -sha256 -binary | openssl enc -base64
https://www.dnsleaktest.com/ https://www.perfect-privacy.com/dns-leaktest
https://www.grc.com/dns/dns.htm http://www.vpninsights.com/dns-leak-test and last but not least
https://cmdns.dev.dns-oarc.net/ for a thorough in depth DNS Test https://bash.ws/dnsleak/test/
