Hi everyone,
I'm using a Fritzbox 7490 with FritzOS.
But I want to use a used Fritz 7520 as a DSL modem with openwrt for Wireguard VPN.
I'm not really an IT expert, but thanks to the great instructions here, I successfully flashed openwrt-24.10.1 on the Fritz 7520.
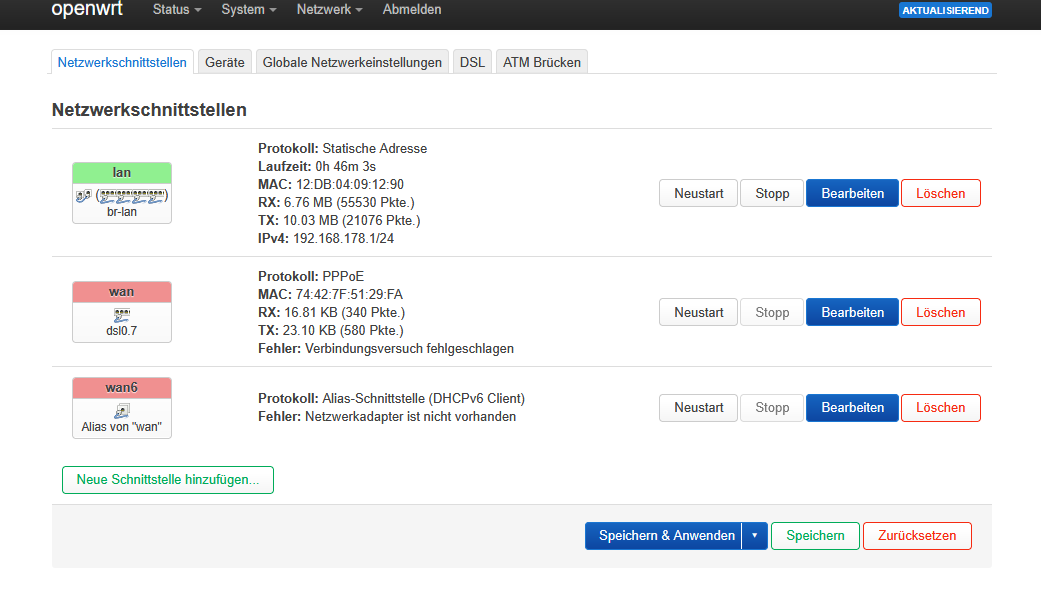
However, when I try to connect the Fritz 7520 to DSL, I get an error message stating that the connection attempt failed.
The port status is displayed as connected, but the bar below is red.
A few KB are displayed as upload and download, and I also get the data rate: 49.991 Mbps / 15.999 Mbps, but I can't get an internet connection.
Display in line mode: G.993.2 (VDSL2, Profile 17a, with downstream and upstream vectoring)
What could be the problem?
I'm sure I entered the correct access data for my 1&1 connection.
I noticed that when connecting the 7490 to FritzOS, the mode is displayed as ITU G.993.5 and G.Vector. Does this mean anything?
I think the Fritz!7520 should support G.Vector.
Can anyone help?
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
The outputs are below.
To ask questions here in the forum, I disconnected the Fritz 7520 from the DSL connection and switched the LAN to DHCP client. The following outputs also occurred without a DSL connection.
I hope this still helps.
root@OpenWrt:~# ubus call system board
{
"kernel": "6.6.86",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 5 (v7l)",
"model": "AVM FRITZ!Box 7530",
"board_name": "avm,fritzbox-7530",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "24.10.1",
"revision": "r28597-0425664679",
"target": "ipq40xx/generic",
"description": "OpenWrt 24.10.1 r28597-0425664679",
"builddate": "1744562312"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fe77:ed51f:be89::/48'
option packet_steering '1'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'j'
option tone 'b'
option ds_snr_offset '0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'dhcp'
config device
option name 'dsl0'
option macaddr '74:92:7B:51:39:FA'
config interface 'wan'
option device 'dsl0'
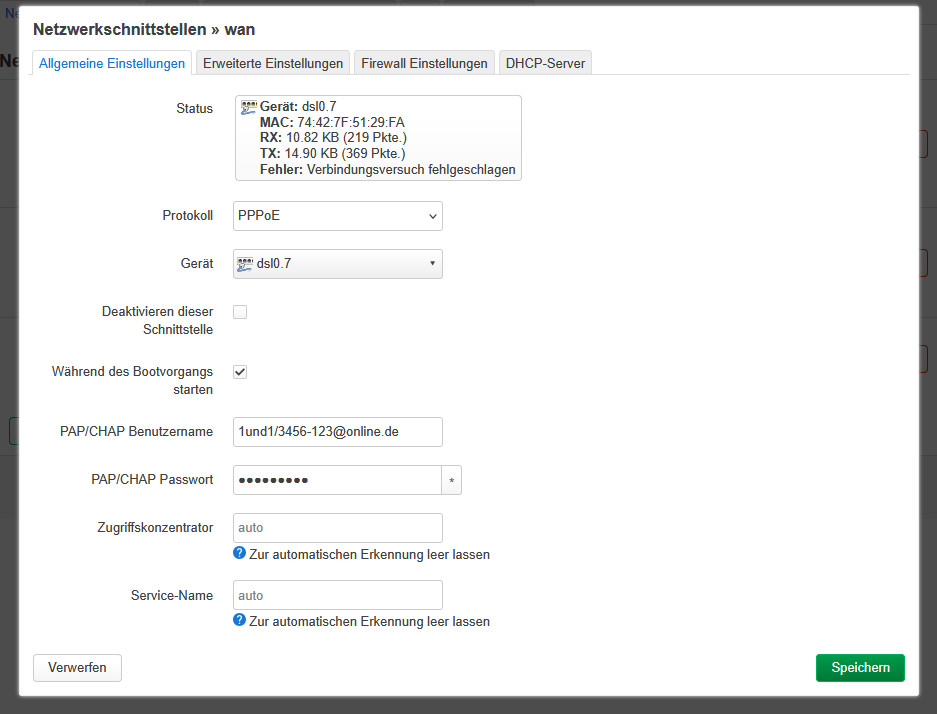
option proto 'pppoe'
option username '1und1/1234-567@online.de'
option password 'abcdefg'
option ipv6 '1'
config interface 'wan6'
option device '@wan'
option proto 'dhcpv6'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood 1
option input REJECT
option output ACCEPT
option forward REJECT
Uncomment this line to disable ipv6 rules
option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
We need to accept udp packets on port 68,
see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
Allow DHCPv6 replies
see https://github.com/openwrt/openwrt/issues/5066
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
config rule
option name Allow-IPSec-ESP
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option name Allow-ISAKMP
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
EXAMPLE CONFIG SECTIONS
do not allow a specific ip to access wan
#config rule
option src lan
option src_ip 192.168.45.2
option dest wan
option proto tcp
option target REJECT
block a specific mac on wan
#config rule
option dest wan
option src_mac 00:11:22:33:44:66
option target REJECT
block incoming ICMP traffic on a zone
#config rule
option src lan
option proto ICMP
option target DROP
port redirect port coming in on wan to lan
#config redirect
option src wan
option src_dport 80
option dest lan
option dest_ip 192.168.16.235
option dest_port 80
option proto tcp
port redirect of remapped ssh port (22001) on wan
#config redirect
option src wan
option src_dport 22001
option dest lan
option dest_port 22
option proto tcp
FULL CONFIG SECTIONS
#config rule
option src lan
option src_ip 192.168.45.2
option src_mac 00:11:22:33:44:55
option src_port 80
option dest wan
option dest_ip 194.25.2.129
option dest_port 120
option proto tcp
option target REJECT
#config redirect
option src lan
option src_ip 192.168.45.2
option src_mac 00:11:22:33:44:55
option src_port 1024
option src_dport 80
option dest_ip 194.25.2.129
option dest_port 120
option proto tcp
i've read around a bit but have no idea if it will work
it seems like people are saying 1&1 germany works over vlan id 7
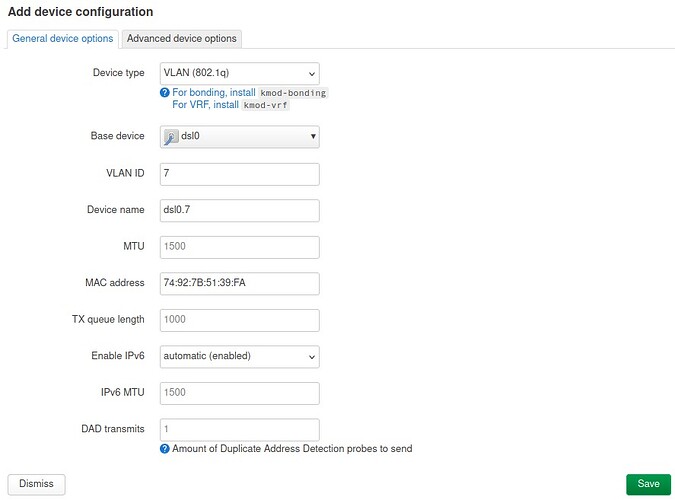
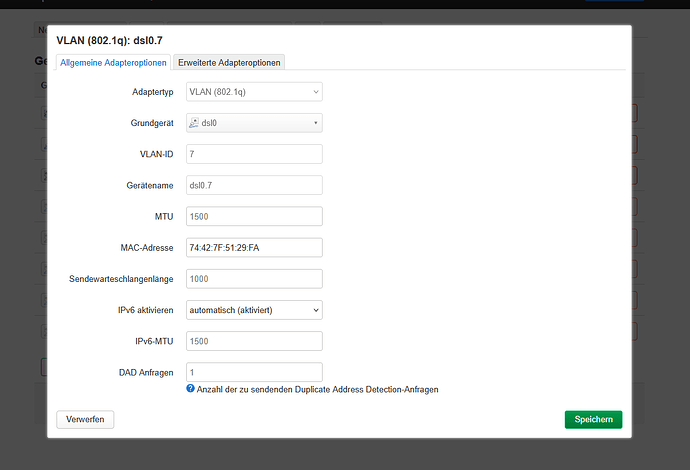
so for your "wan" interface, you would put 'dsl0.7' as your device
if the mac address is important though you might need to create the vlan device yourself and make sure you set the mac address to what you have there for dsl0.7 instead of dsl0 maaaybe
eg
config device
option type '8021q'
option ifname 'dsl0'
option vid '7'
option name 'dsl0.7'
option macaddr '74:92:7B:51:39:FA'
Yes, I had read that too:
But after that, this should be when migrating from Annex B to Annex J.
According to my information about the functioning 7490, Annex B should definitely be running here?
Connection type: VDSL2 17a G.Vector (ITU G.993.5)
Line ID: 1UND1.DEU.DTAG.J03X8
arrow_downReceive: 49.99 Mbps
arrow_upSend: 16.00 Mbps
But I could give it a try, thanks.
Unfortunately, I can't select DSL0.
Please excuse me, but as I already mentioned, I'm not exactly an IT expert.
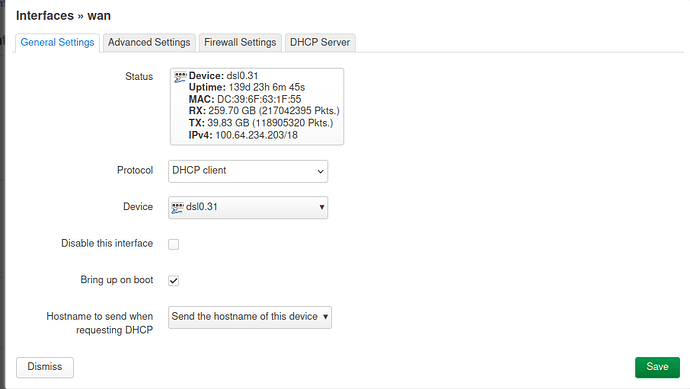
It's not necessary to create a VLAN device manually. Just put "dsl0.7" as device in the WAN interface (you will need to type this as it won't be listed). This is my wan interface with VLAN 31:
In your screenshot, dsl0 is probably not listed because it's not synchronized (you mentioned you were connected via LAN). You can still input the device manually.
OK, I'll test again this weekend. Thanks for the tips. But I'm generally interested in whether the Fritz 7520 (black 1&1 with Q4019) will even work productively as a DSL modem with OpenWrt, or whether it's not particularly reliable. Has anyone used this box in this way?
I use mine fine on the NBN in Australia. Fritz 7530 + Openwrt is the best there is, sure it could have better wireless but works and is reliable.
Also just one thing, don't be discouraged if it immediately doesn't work or you appear to login but can't browse. Some ISPs have a time out feature when the client mac address changes, so sometimes it can take a while to be able to actually log in or it lets you log in and you get an address but you can't browse for a while, but eventually the lock they have at their end gets forgotten, but you may need to refresh or 'restart' the wan connection every 15 mins or so to see.
Yes, the thing about the lock on the new MAC is plausible. I waited over 30 minutes and didn't get a valid login. Maybe that was too short, and maybe I should call my provider's support while I waited to get it activated. As soon as I have the chance, I'll try that and report the results here. ![]()
Unfortunately, I can't often crash the internet here for that long. ![]()
I use a 7520 as bridged modem on a 100/40 VDSL" link in Germany (O2, on basis of a telekom vdsl2 access line), works without any noticeable issues (but note I am on a short TAL and get full sync with line capacity to spare).
Note for 1&1 you need to use the correct username, which differs for ADSL, VDSL2, and apparently nowadays ds-lite over VDSL, here are examples:
ADSL: option username '1und1/(***)1234-567@t-online.de' # note no H prefix and no ui
VDSL: option username 'H1und1/1234-567@t-online.de' # note the H prefix!
ds-lite: option username '1und1/ui1234-567@t-online.de' # note the ui in there
I never used 1&1, but I remember this being an issue in the past, so maybe that helps...
The connection here is VDLS2. But in the original FritzOS, there's no need to prefix it with an H, which is strange that it should be with openwrt. Still, it can't hurt to try. Thanks.
Ah, since you use PPPoE, edit /etc/ppp/options and change #debug to debug, then run logread | grep ppp after giving it a bit to connect, check the output for sensitive information, potentially redact that and post the rest here, that might tell us what goes wrong...
Hi everyone,
Today I finally had the chance to test the project a bit.
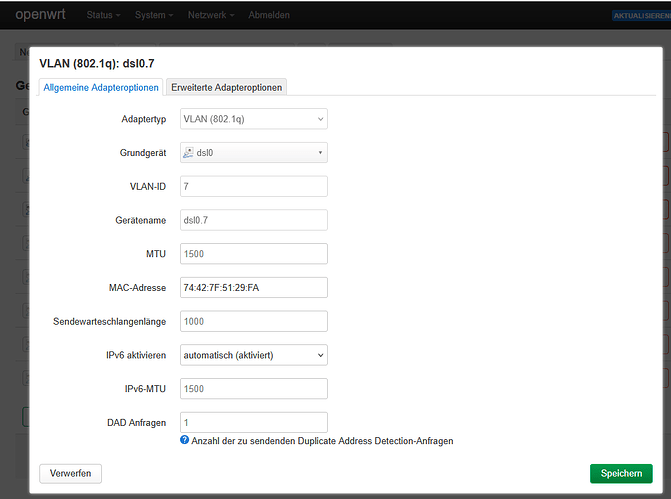
The H prefix didn't help. I created dsl0.7 and waited for an hour, to no avail. Here are a few screenshots of the settings, and then I'll upload the PPP debug output. I hope there's no sensitive information there; I've changed the username. Hopefully, someone can spot the mistake I'm making here.
root@openwrt:~# logread | grep ppp
Sun Jul 13 15:43:18 2025 kern.warn kernel: [ 30.865349] Modules linked in: pppoe ppp_async nft_fib_inet nf_flow_table_inet ath10k_pci(O) ath10k_core(O) ath(O) pppox ppp_generic nft_reject_ipv6 nft_reject_ipv4 nft_reject_inet nft_reject nft_redir nft_quota nft_numgen nft_nat nft_masq nft_log nft_limit nft_hash nft_flow_offload nft_fib_ipv6 nft_fib_ipv4 nft_fib nft_ct nft_chain_nat nf_tables nf_nat nf_flow_table nf_conntrack mac80211(O) cfg80211(O) slhc nfnetlink nf_reject_ipv6 nf_reject_ipv4 nf_log_syslog nf_defrag_ipv6 nf_defrag_ipv4 libcrc32c hwmon crc_ccitt compat(O) clip drv_dsl_cpe_api(O) drv_mei_cpe(O) br2684 vrx518_tc(O) atm vrx518(O) drv_ifxos(O) sha512_arm md5 ghash_arm_ce cmac leds_gpio xhci_plat_hcd xhci_pci xhci_hcd dwc3 dwc3_qcom gpio_button_hotplug(O) crc32c_generic
Sun Jul 13 15:44:48 2025 daemon.info pppd[2735]: Plugin pppoe.so loaded.
Sun Jul 13 15:44:48 2025 daemon.info pppd[2735]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:44:48 2025 daemon.notice pppd[2735]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:44:48 2025 daemon.debug pppd[2735]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:44:48 2025 daemon.debug pppd[2735]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:44:48 2025 daemon.debug pppd[2735]: [service-name] [host-uniq af 0a 00 00]
Sun Jul 13 15:44:53 2025 daemon.debug pppd[2735]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:44:53 2025 daemon.debug pppd[2735]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:44:53 2025 daemon.debug pppd[2735]: [service-name] [host-uniq af 0a 00 00]
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: [AC-name WAGJ00] [host-uniq af 0a 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: [service-name] [host-uniq af 0a 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: [service-name] [host-uniq af 0a 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:44:54 2025 daemon.info pppd[2735]: PPP session is 67
Sun Jul 13 15:44:54 2025 daemon.warn pppd[2735]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: using channel 1
Sun Jul 13 15:44:54 2025 daemon.info pppd[2735]: Using interface pppoe-wan
Sun Jul 13 15:44:54 2025 daemon.notice pppd[2735]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x56dd49c8>]
Sun Jul 13 15:44:54 2025 daemon.debug pppd[2735]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x56dd49c8>]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: rcvd [LCP ConfReq id=0xd9 <mru 1492> <auth pap> <magic 0x25e9709f>]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: sent [LCP ConfAck id=0xd9 <mru 1492> <auth pap> <magic 0x25e9709f>]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: sent [LCP EchoReq id=0x0 magic=0x56dd49c8]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: rcvd [LCP EchoRep id=0x0 magic=0x25e9709f]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122213887 profile not sufficient"]
Sun Jul 13 15:44:57 2025 daemon.info pppd[2735]: Remote message: 0034 PXYMUN13 0122213887 profile not sufficient
Sun Jul 13 15:44:57 2025 daemon.err pppd[2735]: PAP authentication failed
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: rcvd [LCP TermReq id=0xda]
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: sent [LCP TermAck id=0xda]
Sun Jul 13 15:44:57 2025 daemon.notice pppd[2735]: Modem hangup
Sun Jul 13 15:44:57 2025 daemon.notice pppd[2735]: Connection terminated.
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2735]: [host-uniq af 0a 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:44:57 2025 daemon.info pppd[2735]: Sent PADT
Sun Jul 13 15:44:57 2025 daemon.info pppd[2735]: Exit.
Sun Jul 13 15:44:57 2025 daemon.info pppd[2809]: Plugin pppoe.so loaded.
Sun Jul 13 15:44:57 2025 daemon.info pppd[2809]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:44:57 2025 daemon.notice pppd[2809]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2809]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2809]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:44:57 2025 daemon.debug pppd[2809]: [service-name] [host-uniq f9 0a 00 00]
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: [service-name] [host-uniq f9 0a 00 00]
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: [AC-name WAGJ00] [host-uniq f9 0a 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: [service-name] [host-uniq f9 0a 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: [service-name] [host-uniq f9 0a 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:02 2025 daemon.info pppd[2809]: PPP session is 67
Sun Jul 13 15:45:02 2025 daemon.warn pppd[2809]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: using channel 2
Sun Jul 13 15:45:02 2025 daemon.info pppd[2809]: Using interface pppoe-wan
Sun Jul 13 15:45:02 2025 daemon.notice pppd[2809]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x65ce3abd>]
Sun Jul 13 15:45:02 2025 daemon.debug pppd[2809]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x65ce3abd>]
Sun Jul 13 15:45:05 2025 daemon.debug pppd[2809]: rcvd [LCP ConfReq id=0x3c <mru 1492> <auth pap> <magic 0x3646015b>]
Sun Jul 13 15:45:05 2025 daemon.debug pppd[2809]: sent [LCP ConfAck id=0x3c <mru 1492> <auth pap> <magic 0x3646015b>]
Sun Jul 13 15:45:05 2025 daemon.debug pppd[2809]: sent [LCP EchoReq id=0x0 magic=0x65ce3abd]
Sun Jul 13 15:45:05 2025 daemon.debug pppd[2809]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:45:05 2025 daemon.debug pppd[2809]: rcvd [LCP EchoRep id=0x0 magic=0x3646015b]
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122214019 profile not sufficient"]
Sun Jul 13 15:45:06 2025 daemon.info pppd[2809]: Remote message: 0034 PXYMUN13 0122214019 profile not sufficient
Sun Jul 13 15:45:06 2025 daemon.err pppd[2809]: PAP authentication failed
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: rcvd [LCP TermReq id=0x3d]
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: sent [LCP TermAck id=0x3d]
Sun Jul 13 15:45:06 2025 daemon.notice pppd[2809]: Modem hangup
Sun Jul 13 15:45:06 2025 daemon.notice pppd[2809]: Connection terminated.
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:45:06 2025 daemon.debug pppd[2809]: [host-uniq f9 0a 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:06 2025 daemon.info pppd[2809]: Sent PADT
Sun Jul 13 15:45:06 2025 daemon.info pppd[2809]: Exit.
Sun Jul 13 15:45:06 2025 daemon.info pppd[3099]: Plugin pppoe.so loaded.
Sun Jul 13 15:45:06 2025 daemon.info pppd[3099]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:45:06 2025 daemon.notice pppd[3099]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:45:06 2025 daemon.debug pppd[3099]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:06 2025 daemon.debug pppd[3099]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:06 2025 daemon.debug pppd[3099]: [service-name] [host-uniq 1b 0c 00 00]
Sun Jul 13 15:45:11 2025 daemon.debug pppd[3099]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:11 2025 daemon.debug pppd[3099]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:11 2025 daemon.debug pppd[3099]: [service-name] [host-uniq 1b 0c 00 00]
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: [service-name] [host-uniq 1b 0c 00 00]
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: [AC-name WAGJ00] [host-uniq 1b 0c 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: [service-name] [host-uniq 1b 0c 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: [service-name] [host-uniq 1b 0c 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:21 2025 daemon.info pppd[3099]: PPP session is 67
Sun Jul 13 15:45:21 2025 daemon.warn pppd[3099]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: using channel 3
Sun Jul 13 15:45:21 2025 daemon.info pppd[3099]: Using interface pppoe-wan
Sun Jul 13 15:45:21 2025 daemon.notice pppd[3099]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0xeba2efef>]
Sun Jul 13 15:45:21 2025 daemon.debug pppd[3099]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0xeba2efef>]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: rcvd [LCP ConfReq id=0xae <mru 1492> <auth pap> <magic 0x2c8b45e4>]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: sent [LCP ConfAck id=0xae <mru 1492> <auth pap> <magic 0x2c8b45e4>]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: sent [LCP EchoReq id=0x0 magic=0xeba2efef]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: rcvd [LCP EchoRep id=0x0 magic=0x2c8b45e4]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122214264 profile not sufficient"]
Sun Jul 13 15:45:24 2025 daemon.info pppd[3099]: Remote message: 0034 PXYMUN13 0122214264 profile not sufficient
Sun Jul 13 15:45:24 2025 daemon.err pppd[3099]: PAP authentication failed
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: rcvd [LCP TermReq id=0xaf]
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: sent [LCP TermAck id=0xaf]
Sun Jul 13 15:45:24 2025 daemon.notice pppd[3099]: Modem hangup
Sun Jul 13 15:45:24 2025 daemon.notice pppd[3099]: Connection terminated.
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:45:24 2025 daemon.debug pppd[3099]: [host-uniq 1b 0c 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:45:24 2025 daemon.info pppd[3099]: Sent PADT
Sun Jul 13 15:45:24 2025 daemon.info pppd[3099]: Exit.
Sun Jul 13 15:45:25 2025 daemon.info pppd[3390]: Plugin pppoe.so loaded.
Sun Jul 13 15:45:25 2025 daemon.info pppd[3390]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:45:25 2025 daemon.notice pppd[3390]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:45:25 2025 daemon.debug pppd[3390]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:25 2025 daemon.debug pppd[3390]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:25 2025 daemon.debug pppd[3390]: [service-name] [host-uniq 3e 0d 00 00]
Sun Jul 13 15:45:30 2025 daemon.debug pppd[3390]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:30 2025 daemon.debug pppd[3390]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:30 2025 daemon.debug pppd[3390]: [service-name] [host-uniq 3e 0d 00 00]
Sun Jul 13 15:45:40 2025 daemon.debug pppd[3390]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:45:40 2025 daemon.debug pppd[3390]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:45:40 2025 daemon.debug pppd[3390]: [service-name] [host-uniq 3e 0d 00 00]
Sun Jul 13 15:46:00 2025 daemon.warn pppd[3390]: Timeout waiting for PADO packets
Sun Jul 13 15:46:00 2025 daemon.err pppd[3390]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:46:00 2025 daemon.info pppd[3390]: Exit.
Sun Jul 13 15:46:00 2025 daemon.info pppd[3675]: Plugin pppoe.so loaded.
Sun Jul 13 15:46:00 2025 daemon.info pppd[3675]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:46:00 2025 daemon.notice pppd[3675]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: [service-name] [host-uniq 5b 0e 00 00]
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: [AC-name WAGJ00] [host-uniq 5b 0e 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: [service-name] [host-uniq 5b 0e 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:46:00 2025 daemon.debug pppd[3675]: [service-name] [host-uniq 5b 0e 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:00 2025 daemon.info pppd[3675]: PPP session is 67
Sun Jul 13 15:46:01 2025 daemon.warn pppd[3675]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:46:01 2025 daemon.debug pppd[3675]: using channel 4
Sun Jul 13 15:46:01 2025 daemon.info pppd[3675]: Using interface pppoe-wan
Sun Jul 13 15:46:01 2025 daemon.notice pppd[3675]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:46:01 2025 daemon.debug pppd[3675]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0xa2837d03>]
Sun Jul 13 15:46:01 2025 daemon.debug pppd[3675]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0xa2837d03>]
Sun Jul 13 15:46:03 2025 daemon.debug pppd[3675]: rcvd [LCP ConfReq id=0x8a <mru 1492> <auth pap> <magic 0x2f4a01df>]
Sun Jul 13 15:46:03 2025 daemon.debug pppd[3675]: sent [LCP ConfAck id=0x8a <mru 1492> <auth pap> <magic 0x2f4a01df>]
Sun Jul 13 15:46:03 2025 daemon.debug pppd[3675]: sent [LCP EchoReq id=0x0 magic=0xa2837d03]
Sun Jul 13 15:46:03 2025 daemon.debug pppd[3675]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:46:03 2025 daemon.debug pppd[3675]: rcvd [LCP EchoRep id=0x0 magic=0x2f4a01df]
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122214753 profile not sufficient"]
Sun Jul 13 15:46:04 2025 daemon.info pppd[3675]: Remote message: 0034 PXYMUN13 0122214753 profile not sufficient
Sun Jul 13 15:46:04 2025 daemon.err pppd[3675]: PAP authentication failed
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: rcvd [LCP TermReq id=0x8b]
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: sent [LCP TermAck id=0x8b]
Sun Jul 13 15:46:04 2025 daemon.notice pppd[3675]: Modem hangup
Sun Jul 13 15:46:04 2025 daemon.notice pppd[3675]: Connection terminated.
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3675]: [host-uniq 5b 0e 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:04 2025 daemon.info pppd[3675]: Sent PADT
Sun Jul 13 15:46:04 2025 daemon.info pppd[3675]: Exit.
Sun Jul 13 15:46:04 2025 daemon.info pppd[3966]: Plugin pppoe.so loaded.
Sun Jul 13 15:46:04 2025 daemon.info pppd[3966]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:46:04 2025 daemon.notice pppd[3966]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3966]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3966]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:04 2025 daemon.debug pppd[3966]: [service-name] [host-uniq 7e 0f 00 00]
Sun Jul 13 15:46:09 2025 daemon.debug pppd[3966]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:09 2025 daemon.debug pppd[3966]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:09 2025 daemon.debug pppd[3966]: [service-name] [host-uniq 7e 0f 00 00]
Sun Jul 13 15:46:19 2025 daemon.debug pppd[3966]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:19 2025 daemon.debug pppd[3966]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:19 2025 daemon.debug pppd[3966]: [service-name] [host-uniq 7e 0f 00 00]
Sun Jul 13 15:46:39 2025 daemon.warn pppd[3966]: Timeout waiting for PADO packets
Sun Jul 13 15:46:39 2025 daemon.err pppd[3966]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:46:39 2025 daemon.info pppd[3966]: Exit.
Sun Jul 13 15:46:40 2025 daemon.info pppd[4252]: Plugin pppoe.so loaded.
Sun Jul 13 15:46:40 2025 daemon.info pppd[4252]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:46:40 2025 daemon.notice pppd[4252]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:46:40 2025 daemon.debug pppd[4252]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:40 2025 daemon.debug pppd[4252]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:40 2025 daemon.debug pppd[4252]: [service-name] [host-uniq 9c 10 00 00]
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: [service-name] [host-uniq 9c 10 00 00]
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: [AC-name WAGJ00] [host-uniq 9c 10 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: [service-name] [host-uniq 9c 10 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: [service-name] [host-uniq 9c 10 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:45 2025 daemon.info pppd[4252]: PPP session is 67
Sun Jul 13 15:46:45 2025 daemon.warn pppd[4252]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: using channel 5
Sun Jul 13 15:46:45 2025 daemon.info pppd[4252]: Using interface pppoe-wan
Sun Jul 13 15:46:45 2025 daemon.notice pppd[4252]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x76a504e3>]
Sun Jul 13 15:46:45 2025 daemon.debug pppd[4252]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x76a504e3>]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: rcvd [LCP ConfReq id=0x92 <mru 1492> <auth pap> <magic 0x273a1c64>]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: sent [LCP ConfAck id=0x92 <mru 1492> <auth pap> <magic 0x273a1c64>]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: sent [LCP EchoReq id=0x0 magic=0x76a504e3]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: rcvd [LCP EchoRep id=0x0 magic=0x273a1c64]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122215247 profile not sufficient"]
Sun Jul 13 15:46:48 2025 daemon.info pppd[4252]: Remote message: 0034 PXYMUN13 0122215247 profile not sufficient
Sun Jul 13 15:46:48 2025 daemon.err pppd[4252]: PAP authentication failed
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: rcvd [LCP TermReq id=0x93]
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: sent [LCP TermAck id=0x93]
Sun Jul 13 15:46:48 2025 daemon.notice pppd[4252]: Modem hangup
Sun Jul 13 15:46:48 2025 daemon.notice pppd[4252]: Connection terminated.
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:46:48 2025 daemon.debug pppd[4252]: [host-uniq 9c 10 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:46:48 2025 daemon.info pppd[4252]: Sent PADT
Sun Jul 13 15:46:48 2025 daemon.info pppd[4252]: Exit.
Sun Jul 13 15:46:48 2025 daemon.info pppd[4542]: Plugin pppoe.so loaded.
Sun Jul 13 15:46:48 2025 daemon.info pppd[4542]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:46:48 2025 daemon.notice pppd[4542]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:46:49 2025 daemon.debug pppd[4542]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:49 2025 daemon.debug pppd[4542]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:49 2025 daemon.debug pppd[4542]: [service-name] [host-uniq be 11 00 00]
Sun Jul 13 15:46:54 2025 daemon.debug pppd[4542]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:46:54 2025 daemon.debug pppd[4542]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:46:54 2025 daemon.debug pppd[4542]: [service-name] [host-uniq be 11 00 00]
Sun Jul 13 15:47:04 2025 daemon.debug pppd[4542]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:47:04 2025 daemon.debug pppd[4542]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:47:04 2025 daemon.debug pppd[4542]: [service-name] [host-uniq be 11 00 00]
Sun Jul 13 15:47:24 2025 daemon.warn pppd[4542]: Timeout waiting for PADO packets
Sun Jul 13 15:47:24 2025 daemon.err pppd[4542]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:47:24 2025 daemon.info pppd[4542]: Exit.
Sun Jul 13 15:47:24 2025 daemon.info pppd[4828]: Plugin pppoe.so loaded.
Sun Jul 13 15:47:24 2025 daemon.info pppd[4828]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:47:24 2025 daemon.notice pppd[4828]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:47:24 2025 daemon.debug pppd[4828]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:47:24 2025 daemon.debug pppd[4828]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:47:24 2025 daemon.debug pppd[4828]: [service-name] [host-uniq dc 12 00 00]
Sun Jul 13 15:47:29 2025 daemon.debug pppd[4828]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:47:29 2025 daemon.debug pppd[4828]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:47:29 2025 daemon.debug pppd[4828]: [service-name] [host-uniq dc 12 00 00]
Sun Jul 13 15:47:39 2025 daemon.debug pppd[4828]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:47:39 2025 daemon.debug pppd[4828]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:47:39 2025 daemon.debug pppd[4828]: [service-name] [host-uniq dc 12 00 00]
Sun Jul 13 15:47:59 2025 daemon.warn pppd[4828]: Timeout waiting for PADO packets
Sun Jul 13 15:47:59 2025 daemon.err pppd[4828]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:47:59 2025 daemon.info pppd[4828]: Exit.
Sun Jul 13 15:47:59 2025 daemon.info pppd[5115]: Plugin pppoe.so loaded.
Sun Jul 13 15:47:59 2025 daemon.info pppd[5115]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:47:59 2025 daemon.notice pppd[5115]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: [service-name] [host-uniq fb 13 00 00]
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: [AC-name WAGJ00] [host-uniq fb 13 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: [service-name] [host-uniq fb 13 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: [service-name] [host-uniq fb 13 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:48:00 2025 daemon.info pppd[5115]: PPP session is 67
Sun Jul 13 15:48:00 2025 daemon.warn pppd[5115]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: using channel 6
Sun Jul 13 15:48:00 2025 daemon.info pppd[5115]: Using interface pppoe-wan
Sun Jul 13 15:48:00 2025 daemon.notice pppd[5115]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x59c14596>]
Sun Jul 13 15:48:00 2025 daemon.debug pppd[5115]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x59c14596>]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: rcvd [LCP ConfReq id=0x4e <mru 1492> <auth pap> <magic 0x70ccb536>]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: sent [LCP ConfAck id=0x4e <mru 1492> <auth pap> <magic 0x70ccb536>]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: sent [LCP EchoReq id=0x0 magic=0x59c14596]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: rcvd [LCP EchoRep id=0x0 magic=0x70ccb536]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122216127 profile not sufficient"]
Sun Jul 13 15:48:03 2025 daemon.info pppd[5115]: Remote message: 0034 PXYMUN13 0122216127 profile not sufficient
Sun Jul 13 15:48:03 2025 daemon.err pppd[5115]: PAP authentication failed
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: rcvd [LCP TermReq id=0x4f]
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: sent [LCP TermAck id=0x4f]
Sun Jul 13 15:48:03 2025 daemon.notice pppd[5115]: Modem hangup
Sun Jul 13 15:48:03 2025 daemon.notice pppd[5115]: Connection terminated.
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5115]: [host-uniq fb 13 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:48:03 2025 daemon.info pppd[5115]: Sent PADT
Sun Jul 13 15:48:03 2025 daemon.info pppd[5115]: Exit.
Sun Jul 13 15:48:03 2025 daemon.info pppd[5406]: Plugin pppoe.so loaded.
Sun Jul 13 15:48:03 2025 daemon.info pppd[5406]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:48:03 2025 daemon.notice pppd[5406]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5406]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5406]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:03 2025 daemon.debug pppd[5406]: [service-name] [host-uniq 1e 15 00 00]
Sun Jul 13 15:48:09 2025 daemon.debug pppd[5406]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:09 2025 daemon.debug pppd[5406]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:09 2025 daemon.debug pppd[5406]: [service-name] [host-uniq 1e 15 00 00]
Sun Jul 13 15:48:19 2025 daemon.debug pppd[5406]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:19 2025 daemon.debug pppd[5406]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:19 2025 daemon.debug pppd[5406]: [service-name] [host-uniq 1e 15 00 00]
Sun Jul 13 15:48:39 2025 daemon.warn pppd[5406]: Timeout waiting for PADO packets
Sun Jul 13 15:48:39 2025 daemon.err pppd[5406]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:48:39 2025 daemon.info pppd[5406]: Exit.
Sun Jul 13 15:48:39 2025 daemon.info pppd[5692]: Plugin pppoe.so loaded.
Sun Jul 13 15:48:39 2025 daemon.info pppd[5692]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:48:39 2025 daemon.notice pppd[5692]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:48:39 2025 daemon.debug pppd[5692]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:39 2025 daemon.debug pppd[5692]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:39 2025 daemon.debug pppd[5692]: [service-name] [host-uniq 3c 16 00 00]
Sun Jul 13 15:48:44 2025 daemon.debug pppd[5692]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:44 2025 daemon.debug pppd[5692]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:44 2025 daemon.debug pppd[5692]: [service-name] [host-uniq 3c 16 00 00]
Sun Jul 13 15:48:54 2025 daemon.debug pppd[5692]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:48:54 2025 daemon.debug pppd[5692]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:48:54 2025 daemon.debug pppd[5692]: [service-name] [host-uniq 3c 16 00 00]
Sun Jul 13 15:49:14 2025 daemon.warn pppd[5692]: Timeout waiting for PADO packets
Sun Jul 13 15:49:14 2025 daemon.err pppd[5692]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:49:14 2025 daemon.info pppd[5692]: Exit.
Sun Jul 13 15:49:14 2025 daemon.info pppd[5967]: Plugin pppoe.so loaded.
Sun Jul 13 15:49:14 2025 daemon.info pppd[5967]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:49:14 2025 daemon.notice pppd[5967]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:49:14 2025 daemon.debug pppd[5967]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:14 2025 daemon.debug pppd[5967]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:14 2025 daemon.debug pppd[5967]: [service-name] [host-uniq 4f 17 00 00]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: [AC-name WAGJ00] [host-uniq 4f 17 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: [service-name] [host-uniq 4f 17 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: [service-name] [host-uniq 4f 17 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:49:15 2025 daemon.info pppd[5967]: PPP session is 67
Sun Jul 13 15:49:15 2025 daemon.warn pppd[5967]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: using channel 7
Sun Jul 13 15:49:15 2025 daemon.info pppd[5967]: Using interface pppoe-wan
Sun Jul 13 15:49:15 2025 daemon.notice pppd[5967]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0xc8089509>]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: rcvd [LCP ConfReq id=0x5d <mru 1492> <auth pap> <magic 0x312c8a6e>]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [LCP ConfAck id=0x5d <mru 1492> <auth pap> <magic 0x312c8a6e>]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0xc8089509>]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [LCP EchoReq id=0x0 magic=0xc8089509]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: rcvd [LCP EchoRep id=0x0 magic=0x312c8a6e]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122217101 profile not sufficient"]
Sun Jul 13 15:49:15 2025 daemon.info pppd[5967]: Remote message: 0034 PXYMUN13 0122217101 profile not sufficient
Sun Jul 13 15:49:15 2025 daemon.err pppd[5967]: PAP authentication failed
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: rcvd [LCP TermReq id=0x5e]
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: sent [LCP TermAck id=0x5e]
Sun Jul 13 15:49:15 2025 daemon.notice pppd[5967]: Modem hangup
Sun Jul 13 15:49:15 2025 daemon.notice pppd[5967]: Connection terminated.
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:49:15 2025 daemon.debug pppd[5967]: [host-uniq 4f 17 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:49:15 2025 daemon.info pppd[5967]: Sent PADT
Sun Jul 13 15:49:15 2025 daemon.info pppd[5967]: Exit.
Sun Jul 13 15:49:15 2025 daemon.info pppd[6002]: Plugin pppoe.so loaded.
Sun Jul 13 15:49:15 2025 daemon.info pppd[6002]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:49:15 2025 daemon.notice pppd[6002]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:49:15 2025 daemon.debug pppd[6002]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:15 2025 daemon.debug pppd[6002]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:15 2025 daemon.debug pppd[6002]: [service-name] [host-uniq 72 17 00 00]
Sun Jul 13 15:49:20 2025 daemon.debug pppd[6002]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:20 2025 daemon.debug pppd[6002]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:20 2025 daemon.debug pppd[6002]: [service-name] [host-uniq 72 17 00 00]
Sun Jul 13 15:49:30 2025 daemon.debug pppd[6002]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:30 2025 daemon.debug pppd[6002]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:30 2025 daemon.debug pppd[6002]: [service-name] [host-uniq 72 17 00 00]
Sun Jul 13 15:49:50 2025 daemon.warn pppd[6002]: Timeout waiting for PADO packets
Sun Jul 13 15:49:50 2025 daemon.err pppd[6002]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:49:50 2025 daemon.info pppd[6002]: Exit.
Sun Jul 13 15:49:51 2025 daemon.info pppd[6317]: Plugin pppoe.so loaded.
Sun Jul 13 15:49:51 2025 daemon.info pppd[6317]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:49:51 2025 daemon.notice pppd[6317]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:49:51 2025 daemon.debug pppd[6317]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:51 2025 daemon.debug pppd[6317]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:51 2025 daemon.debug pppd[6317]: [service-name] [host-uniq ad 18 00 00]
Sun Jul 13 15:49:56 2025 daemon.debug pppd[6317]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:49:56 2025 daemon.debug pppd[6317]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:49:56 2025 daemon.debug pppd[6317]: [service-name] [host-uniq ad 18 00 00]
Sun Jul 13 15:50:06 2025 daemon.debug pppd[6317]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:50:06 2025 daemon.debug pppd[6317]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:50:06 2025 daemon.debug pppd[6317]: [service-name] [host-uniq ad 18 00 00]
Sun Jul 13 15:50:26 2025 daemon.warn pppd[6317]: Timeout waiting for PADO packets
Sun Jul 13 15:50:26 2025 daemon.err pppd[6317]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:50:26 2025 daemon.info pppd[6317]: Exit.
Sun Jul 13 15:50:26 2025 daemon.info pppd[6633]: Plugin pppoe.so loaded.
Sun Jul 13 15:50:26 2025 daemon.info pppd[6633]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:50:26 2025 daemon.notice pppd[6633]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: [service-name] [host-uniq e9 19 00 00]
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: [AC-name WAGJ00] [host-uniq e9 19 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: [service-name] [host-uniq e9 19 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: [service-name] [host-uniq e9 19 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:50:26 2025 daemon.info pppd[6633]: PPP session is 67
Sun Jul 13 15:50:26 2025 daemon.warn pppd[6633]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: using channel 8
Sun Jul 13 15:50:26 2025 daemon.info pppd[6633]: Using interface pppoe-wan
Sun Jul 13 15:50:26 2025 daemon.notice pppd[6633]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 15:50:26 2025 daemon.debug pppd[6633]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x699a43ba>]
Sun Jul 13 15:50:27 2025 daemon.debug pppd[6633]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x699a43ba>]
Sun Jul 13 15:50:29 2025 daemon.debug pppd[6633]: rcvd [LCP ConfReq id=0xfc <mru 1492> <auth pap> <magic 0x2c98ae6e>]
Sun Jul 13 15:50:29 2025 daemon.debug pppd[6633]: sent [LCP ConfAck id=0xfc <mru 1492> <auth pap> <magic 0x2c98ae6e>]
Sun Jul 13 15:50:29 2025 daemon.debug pppd[6633]: sent [LCP EchoReq id=0x0 magic=0x699a43ba]
Sun Jul 13 15:50:29 2025 daemon.debug pppd[6633]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 15:50:29 2025 daemon.debug pppd[6633]: rcvd [LCP EchoRep id=0x0 magic=0x2c98ae6e]
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122218095 profile not sufficient"]
Sun Jul 13 15:50:30 2025 daemon.info pppd[6633]: Remote message: 0034 PXYMUN13 0122218095 profile not sufficient
Sun Jul 13 15:50:30 2025 daemon.err pppd[6633]: PAP authentication failed
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: rcvd [LCP TermReq id=0xfd]
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: sent [LCP TermAck id=0xfd]
Sun Jul 13 15:50:30 2025 daemon.notice pppd[6633]: Modem hangup
Sun Jul 13 15:50:30 2025 daemon.notice pppd[6633]: Connection terminated.
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6633]: [host-uniq e9 19 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 15:50:30 2025 daemon.info pppd[6633]: Sent PADT
Sun Jul 13 15:50:30 2025 daemon.info pppd[6633]: Exit.
Sun Jul 13 15:50:30 2025 daemon.info pppd[6923]: Plugin pppoe.so loaded.
Sun Jul 13 15:50:30 2025 daemon.info pppd[6923]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:50:30 2025 daemon.notice pppd[6923]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6923]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6923]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:50:30 2025 daemon.debug pppd[6923]: [service-name] [host-uniq 0b 1b 00 00]
Sun Jul 13 15:50:35 2025 daemon.debug pppd[6923]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:50:35 2025 daemon.debug pppd[6923]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:50:35 2025 daemon.debug pppd[6923]: [service-name] [host-uniq 0b 1b 00 00]
Sun Jul 13 15:50:45 2025 daemon.debug pppd[6923]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:50:45 2025 daemon.debug pppd[6923]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:50:45 2025 daemon.debug pppd[6923]: [service-name] [host-uniq 0b 1b 00 00]
Sun Jul 13 15:51:05 2025 daemon.warn pppd[6923]: Timeout waiting for PADO packets
Sun Jul 13 15:51:05 2025 daemon.err pppd[6923]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 15:51:05 2025 daemon.info pppd[6923]: Exit.
Sun Jul 13 15:51:06 2025 daemon.info pppd[7218]: Plugin pppoe.so loaded.
Sun Jul 13 15:51:06 2025 daemon.info pppd[7218]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 15:51:06 2025 daemon.notice pppd[7218]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 15:51:06 2025 daemon.debug pppd[7218]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:51:06 2025 daemon.debug pppd[7218]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:51:06 2025 daemon.debug pppd[7218]: [service-name] [host-uniq 32 1c 00 00]
Sun Jul 13 15:51:11 2025 daemon.debug pppd[7218]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:51:11 2025 daemon.debug pppd[7218]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:51:11 2025 daemon.debug pppd[7218]: [service-name] [host-uniq 32 1c 00 00]
Sun Jul 13 15:51:21 2025 daemon.debug pppd[7218]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 15:51:21 2025 daemon.debug pppd[7218]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 15:51:21 2025 daemon.debug pppd[7218]: [service-name] [host-uniq 32 1c 00 00]
Sun Jul 13 18:57:51 2025 daemon.warn pppd[7218]: Timeout waiting for PADO packets
Sun Jul 13 18:57:51 2025 daemon.err pppd[7218]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 18:57:51 2025 daemon.info pppd[7218]: Exit.
Sun Jul 13 18:57:52 2025 daemon.info pppd[7597]: Plugin pppoe.so loaded.
Sun Jul 13 18:57:52 2025 daemon.info pppd[7597]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 18:57:52 2025 daemon.notice pppd[7597]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: [service-name] [host-uniq ad 1d 00 00]
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: [AC-name WAGJ00] [host-uniq ad 1d 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: [service-name] [host-uniq ad 1d 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: [service-name] [host-uniq ad 1d 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:57:52 2025 daemon.info pppd[7597]: PPP session is 67
Sun Jul 13 18:57:52 2025 daemon.warn pppd[7597]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: using channel 9
Sun Jul 13 18:57:52 2025 daemon.info pppd[7597]: Using interface pppoe-wan
Sun Jul 13 18:57:52 2025 daemon.notice pppd[7597]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x9fcf91d2>]
Sun Jul 13 18:57:52 2025 daemon.debug pppd[7597]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x9fcf91d2>]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: rcvd [LCP ConfReq id=0x60 <mru 1492> <auth pap> <magic 0x4c2032e2>]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: sent [LCP ConfAck id=0x60 <mru 1492> <auth pap> <magic 0x4c2032e2>]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: sent [LCP EchoReq id=0x0 magic=0x9fcf91d2]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: rcvd [LCP EchoRep id=0x0 magic=0x4c2032e2]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122218904 profile not sufficient"]
Sun Jul 13 18:57:55 2025 daemon.info pppd[7597]: Remote message: 0034 PXYMUN13 0122218904 profile not sufficient
Sun Jul 13 18:57:55 2025 daemon.err pppd[7597]: PAP authentication failed
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: rcvd [LCP TermReq id=0x61]
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: sent [LCP TermAck id=0x61]
Sun Jul 13 18:57:55 2025 daemon.notice pppd[7597]: Modem hangup
Sun Jul 13 18:57:55 2025 daemon.notice pppd[7597]: Connection terminated.
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 18:57:55 2025 daemon.debug pppd[7597]: [host-uniq ad 1d 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:57:55 2025 daemon.info pppd[7597]: Sent PADT
Sun Jul 13 18:57:55 2025 daemon.info pppd[7597]: Exit.
Sun Jul 13 18:57:55 2025 daemon.info pppd[7887]: Plugin pppoe.so loaded.
Sun Jul 13 18:57:55 2025 daemon.info pppd[7887]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 18:57:56 2025 daemon.notice pppd[7887]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 18:57:56 2025 daemon.debug pppd[7887]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:57:56 2025 daemon.debug pppd[7887]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:57:56 2025 daemon.debug pppd[7887]: [service-name] [host-uniq cf 1e 00 00]
Sun Jul 13 18:58:01 2025 daemon.debug pppd[7887]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:58:01 2025 daemon.debug pppd[7887]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:58:01 2025 daemon.debug pppd[7887]: [service-name] [host-uniq cf 1e 00 00]
Sun Jul 13 18:58:11 2025 daemon.debug pppd[7887]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:58:11 2025 daemon.debug pppd[7887]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:58:11 2025 daemon.debug pppd[7887]: [service-name] [host-uniq cf 1e 00 00]
Sun Jul 13 18:58:30 2025 daemon.warn pppd[7887]: Timeout waiting for PADO packets
Sun Jul 13 18:58:30 2025 daemon.err pppd[7887]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 18:58:30 2025 daemon.info pppd[7887]: Exit.
Sun Jul 13 18:58:30 2025 daemon.info pppd[8891]: Plugin pppoe.so loaded.
Sun Jul 13 18:58:30 2025 daemon.info pppd[8891]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 18:58:30 2025 daemon.notice pppd[8891]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 18:58:30 2025 daemon.debug pppd[8891]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:58:30 2025 daemon.debug pppd[8891]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:58:30 2025 daemon.debug pppd[8891]: [service-name] [host-uniq bb 22 00 00]
Sun Jul 13 18:58:35 2025 daemon.debug pppd[8891]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:58:35 2025 daemon.debug pppd[8891]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:58:35 2025 daemon.debug pppd[8891]: [service-name] [host-uniq bb 22 00 00]
Sun Jul 13 18:58:45 2025 daemon.debug pppd[8891]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:58:45 2025 daemon.debug pppd[8891]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:58:45 2025 daemon.debug pppd[8891]: [service-name] [host-uniq bb 22 00 00]
Sun Jul 13 18:59:06 2025 daemon.warn pppd[8891]: Timeout waiting for PADO packets
Sun Jul 13 18:59:06 2025 daemon.err pppd[8891]: Unable to complete PPPoE Discovery phase 1
Sun Jul 13 18:59:06 2025 daemon.info pppd[8891]: Exit.
Sun Jul 13 18:59:06 2025 daemon.info pppd[9167]: Plugin pppoe.so loaded.
Sun Jul 13 18:59:06 2025 daemon.info pppd[9167]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 18:59:06 2025 daemon.notice pppd[9167]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: [service-name] [host-uniq cf 23 00 00]
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: Recv PPPOE Discovery V1T1 PADO session 0x0 length 42
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: [AC-name WAGJ00] [host-uniq cf 23 00 00] [service-name] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: Send PPPOE Discovery V1T1 PADR session 0x0 length 32
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: [service-name] [host-uniq cf 23 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: Recv PPPOE Discovery V1T1 PADS session 0x43 length 42
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: dst 74:42:7f:51:29:fa src 40:a6:77:38:12:ea
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: [service-name] [host-uniq cf 23 00 00] [AC-name WAGJ00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:59:06 2025 daemon.info pppd[9167]: PPP session is 67
Sun Jul 13 18:59:06 2025 daemon.warn pppd[9167]: Connected to 40:A6:77:38:12:EA via interface dsl0.7
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: using channel 10
Sun Jul 13 18:59:06 2025 daemon.info pppd[9167]: Using interface pppoe-wan
Sun Jul 13 18:59:06 2025 daemon.notice pppd[9167]: Connect: pppoe-wan <--> dsl0.7
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: sent [LCP ConfReq id=0x1 <mru 1492> <magic 0x338454c3>]
Sun Jul 13 18:59:06 2025 daemon.debug pppd[9167]: rcvd [LCP ConfAck id=0x1 <mru 1492> <magic 0x338454c3>]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: rcvd [LCP ConfReq id=0xc9 <mru 1492> <auth pap> <magic 0x5b8a585d>]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: sent [LCP ConfAck id=0xc9 <mru 1492> <auth pap> <magic 0x5b8a585d>]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: sent [LCP EchoReq id=0x0 magic=0x338454c3]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: sent [PAP AuthReq id=0x1 user="1und1/1234-567@online.de" password=<hidden>]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: rcvd [LCP EchoRep id=0x0 magic=0x5b8a585d]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: rcvd [PAP AuthNak id=0x1 "0034 PXYMUN13 0122219836 profile not sufficient"]
Sun Jul 13 18:59:09 2025 daemon.info pppd[9167]: Remote message: 0034 PXYMUN13 0122219836 profile not sufficient
Sun Jul 13 18:59:09 2025 daemon.err pppd[9167]: PAP authentication failed
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: sent [LCP TermReq id=0x2 "Failed to authenticate ourselves to peer"]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: rcvd [LCP TermReq id=0xca]
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: sent [LCP TermAck id=0xca]
Sun Jul 13 18:59:09 2025 daemon.notice pppd[9167]: Modem hangup
Sun Jul 13 18:59:09 2025 daemon.notice pppd[9167]: Connection terminated.
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: Send PPPOE Discovery V1T1 PADT session 0x43 length 28
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: dst 40:a6:77:38:12:ea src 74:42:7f:51:29:fa
Sun Jul 13 18:59:09 2025 daemon.debug pppd[9167]: [host-uniq cf 23 00 00] [AC-cookie e0 ad fb ad c3 a5 86 5b 36 1b cd 00 38 cf 7c 30]
Sun Jul 13 18:59:09 2025 daemon.info pppd[9167]: Sent PADT
Sun Jul 13 18:59:10 2025 daemon.info pppd[9167]: Exit.
Sun Jul 13 18:59:10 2025 daemon.info pppd[9465]: Plugin pppoe.so loaded.
Sun Jul 13 18:59:10 2025 daemon.info pppd[9465]: PPPoE plugin from pppd 2.5.1
Sun Jul 13 18:59:10 2025 daemon.notice pppd[9465]: pppd 2.5.1 started by root, uid 0
Sun Jul 13 18:59:10 2025 daemon.debug pppd[9465]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:59:10 2025 daemon.debug pppd[9465]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:59:10 2025 daemon.debug pppd[9465]: [service-name] [host-uniq f9 24 00 00]
Sun Jul 13 18:59:15 2025 daemon.debug pppd[9465]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:59:15 2025 daemon.debug pppd[9465]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:59:15 2025 daemon.debug pppd[9465]: [service-name] [host-uniq f9 24 00 00]
Sun Jul 13 18:59:25 2025 daemon.debug pppd[9465]: Send PPPOE Discovery V1T1 PADI session 0x0 length 12
Sun Jul 13 18:59:25 2025 daemon.debug pppd[9465]: dst ff:ff:ff:ff:ff:ff src 74:42:7f:51:29:fa
Sun Jul 13 18:59:25 2025 daemon.debug pppd[9465]: [service-name] [host-uniq f9 24 00 00]
Looks like the other side of the PPPoE link is not a happy camper... I would talk to the ISP.
The good news is it looks like everything is working ![]()
The bad news is except the login and password ![]()
Seems like there's some talk about it here: https://www.ip-phone-forum.de/threads/7390-fritz-box-als-dsl-modem-nutzen-pppoe-profile-not-sufficient.207436/ I assume you can translate that with google if you need to like I did. Or perhaps even post there if it's a place that is still active.
Hello @wilsonyan. In that link, prefix H was the solution. I tried that yesterday without success. The thread there is over 15 years old, so a post won't be successful. However, I haven't tried adjusting the MAC yet. It's worth a try.
@moeller0 I think I'll have to do that. Unfortunately, it was a bit difficult to find a competent contact person yesterday, Sunday.
Could you try this again and post the PPPoE log, please?
Telekom does not care about the MAC, so this should not matter... but they di care about the PPPoE realm as they seem to use that information to "route" packets to their resellers...
Also, could you post the output of:
curl -s "https://www.easybell.de/api/provider-availabilities/TAL?exact_address=false&zip_code=PLZ&city=STADT&street=STRASSE&house_number=HAUSNUMMER"
replace PLZ, STADT, STRASSE, HAUSNUMMER with your true values look at the values for carrier in the DSL sections the question is dies it say 1U1 or DTAG?