What you are trying to do is called hairpin NAT. It is better if you create a hostname for the server and bind it to the internal server IP. Otherwise the router will be a proxy for all the traffic going from lan hosts to the dmz server and might become a bottleneck.
@lleachii : yes, I'm trying to forward port 80 to another server and no, I'm not trying to expose luci
@trendy : my servers already have dedicated hostname/domain names and I'm accessing through these. However the domains point toward my public IP. Your solution would require to setup a dedicated DNS server on my LAN that would resolve these domains with their local IP. Am I right? Did I understand correctly your intention?
If I understood correctly, I'd rather not have a dedicated DNS or dedicated hosts for my server other than the one I usually use.
And I guess my main question is, why did it work before I setup any VLAN?
config rule
option target 'ACCEPT'
option proto 'tcp'
option name 'HTTP'
option family 'ipv4'
option dest_port '80'
option src 'wan'
option dest 'lan'
list dest_ip 'xxx.xxx.xxx.xxx'
![]() Be sure to test from WAN (i.e. the Zone for which you created the rule).
Be sure to test from WAN (i.e. the Zone for which you created the rule).
As I accessed my website through my WAN public address, I guessed it would apply the WAN rules althrough I come from LAN
Nope, that isn’t the case.
Not sure if your response meant you did or didn't.
You'll need to try from the WAN zone to test such a rule.
let's see the complete firewall configuration in text form (and the network file, too, just to make sure we can see the whole story).
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/firewall
My network and firewall file were provided as link in my first post, but here it is:
network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fd0d:56a4:b54e::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-lan.99'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option vendorid 'neufbox_NB6V-XXXXXXXXXX'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config interface 'wwan'
option proto 'dhcp'
config interface 'dmz'
option proto 'static'
option ipaddr '172.16.0.1'
option netmask '255.255.0.0'
option device 'br-lan.1'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1:t'
config bridge-vlan
option device 'br-lan'
option vlan '99'
list ports 'lan1:t'
list ports 'lan2:u*'
list ports 'lan3:u*'
list ports 'lan4:u*'
firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
list network 'dmz'
option name 'dmz'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option src 'lan'
list src_ip '192.168.1.23'
option dest 'wan'
option target 'DROP'
option name 'Block Fan2'
config rule
option name 'Block Vacuum2'
option src 'lan'
list src_ip '192.168.1.22'
option dest 'wan'
option target 'DROP'
config rule
option name 'Block cam2'
option src 'lan'
list src_ip '192.168.1.87'
option dest 'wan'
option target 'DROP'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
list proto 'tcp'
option src 'wan'
option src_dport '80'
option name 'http'
option dest_ip '172.16.0.101'
option dest 'lan'
config redirect
option target 'DNAT'
list proto 'tcp'
option src 'wan'
option src_dport '443'
option name 'https'
option dest_ip '172.16.0.101'
option dest 'lan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'ssh-git'
list proto 'tcp'
option src 'wan'
option src_dport '22'
option dest_ip '172.16.0.104'
config forwarding
option dest 'wan'
config forwarding
option src 'wan'
config forwarding
option src 'dmz'
option dest 'wan'
config rule
option name 'Allow-IPSec-ESP-DMZ'
list proto 'esp'
option src 'wan'
option dest 'dmz'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP-DMZ'
list proto 'udp'
option src 'wan'
option dest 'dmz'
option dest_port '500'
option target 'ACCEPT'
config rule
option name 'external-samba-445'
list proto 'tcp'
option src 'dmz'
list src_ip '172.16.0.101'
option dest 'lan'
list dest_ip '192.168.1.101'
option dest_port '445'
option target 'ACCEPT'
config rule
option name 'external-samba-139'
list proto 'tcp'
option src 'dmz'
list src_ip '172.16.0.101'
option dest 'lan'
list dest_ip '192.168.1.101'
option dest_port '139'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'dmz'
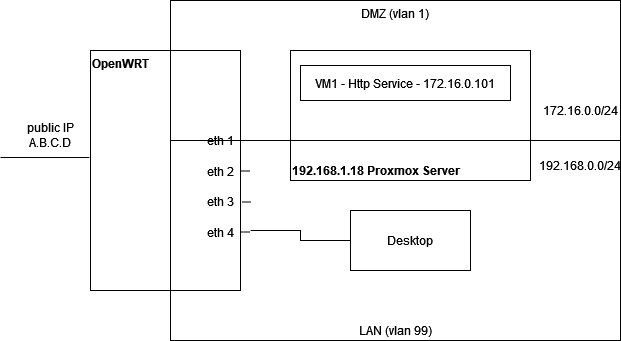
And just to remind what I currently have:
- port forwarding from WAN to LAN on port 80/443 to IP 172.16.0.101 (even though ip is not in LAN)
And my issue was with :
- port forwarding from WAN to DMZ on port 80/443 to IP 172.16.0.101
=> because then, when accessing public IP A.B.C.D from my desktop, it did not forward traffic to 172.16.0.101 but to luci instead. Even though nat loopback was enabled.
(but yes, it worked when I accessed it from the internet)
What I want (and that works with my current weird config with LAN instead of DMZ) :
- access 172.16.0.101 when browsing http://A.B.C.D (public address) from the internet, from my LAN vlan or from my DMZ vlan
- access luci when browsing http://192.168.1.1 from my LAN
Where is this IP???
(That's the zone you'd set.)
This IP is part of the DMZ vlan (172.16.0.0/24) not part of the LAN vlan (192.168.0.0/24)
Then:
option dest 'dmz'
I'm sorry to have to say this, but could you please read my post more carefully? From the beginning you're asking question or giving solution about things that were already addressed.
As I said, when setting the rule destination to DMZ, I then can no longer access to my server via my public IP while inside my LAN vlan
This requires a different rule:
config redirect
option target 'DNAT'
option src 'wan'
option proto 'tcp'
option src_dport '80'
option dest_port '80'
option src_ip '192.168.1.0/24'
option name 'REDIRECT_HTTP_LAN'
option dest_ip '172.16.0.101'
option dest 'lan' #<---yes, this is correct, it will route to DMZ and be allowed
Then again, if I create a new rule "from lan to dmz, port 80/443", then I can no longer access luci interface by browsing 192.168.1.1
See rule:
(Notice rule uses LAN as DST and WAN as SRC.)
It works with this rule, but at the end of the day, this rule is kind of the same I have currently. So why bother having 2 distinct rules indead of the one I currently have? Is it really correct / the intended way to have the destination to LAN when the IP is 172.16.0.0/24? I can't wrap my head around this rule
- Rule one: allow WAN traffic to server
- Rule two: allow LAN traffic to server
Rationale for rule 2:
Instead of a firewall rule - the other option is to create an internal DNS hostname for the server instead:
# in /etc/config/dhcp
config domain
option ip '172.16.0.101'
option name 'foo.example.com' #<---this would be the Global FQDN of the server
You don't need to set up any DNS server, the built-in dnsmasq works fine.
If you don't want to do that, you'll have to make a DNAT rule matching from lan to wan IP http(s) to send it to the server in dmz. Which is making the OpenWrt a proxy and is a waste of resource.
Ok, thanks to you both.
I ended up using a lan to dmz rule instead of the wan to lan rule as it made more sense to me. And I fixed the fact of having no longer access to luci by specifying the src_dip to "wan".
So in the end I have:
config redirect
option target 'DNAT'
list proto 'tcp'
option src 'wan'
option src_dport '80'
option name 'http'
option dest_ip '172.16.0.101'
option dest 'dmz'
config redirect
option target 'DNAT'
list proto 'tcp'
option src 'wan'
option src_dport '443'
option name 'https'
option dest_ip '172.16.0.101'
option dest 'dmz'
config redirect
option name 'http-lan'
option dest 'dmz'
option target 'DNAT'
list proto 'tcp'
option src 'lan'
option src_dport '80'
option dest_ip '172.16.0.101'
option src_dip 'wan'
option reflection_src 'external'
config redirect
option name 'https-lan'
option dest 'dmz'
option target 'DNAT'
list proto 'tcp'
option src 'lan'
option src_dport '443'
option dest_ip '172.16.0.101'
option src_dip 'wan'
option reflection_src 'external'
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.