Would appreciate help with setting up VLAN's & Firewall, been at this for over a month now and the way things are done confuse me greatly. I have read the docs over and over, and searched videos and asked people for help. I can't get things setup how I want. Granted I am slightly new to dealing with all this. I am not on my network at this moment, so I can't grab the exact files from the router, however I can attempt to give a rundown of my setup and my issues. If you want to see a certain file, ask and I can grab it when I get on my network.
I am not entirely sure what I have setup right, and what I don't. I'd like to avoid starting fresh, and just try to fix what I already have because I think it's just a few firewall settings that need to be changed around. I just don't know if my current setup, matches my goals, and also the few issues I am having.
Thanks.
Hardware Setup
I have OpenWRT router and a laptop running Pihole for DNS, and NGINX for my media server (Ports 80 and 443 are open for this).
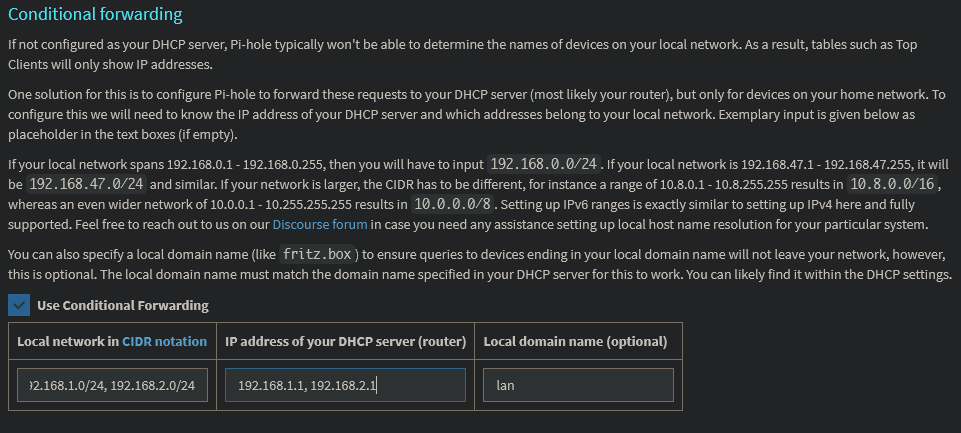
Router at 192.168.5.4, and Pihole at 192.168.5.5.
I have two unmanaged switches going into the house. One is only family stuff and the other is mine. Both go directly into the router.
I have a printer (192.168.40.10) on IOT, other devices may be added to it in the future.
OpenWRT Interfaces
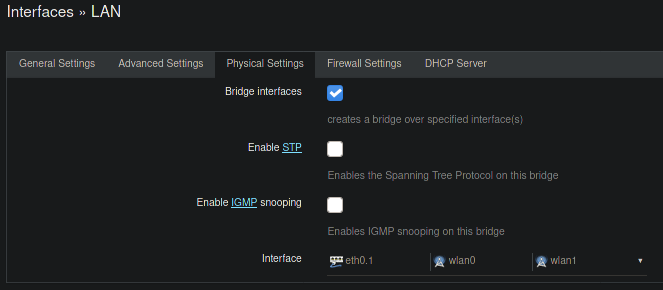
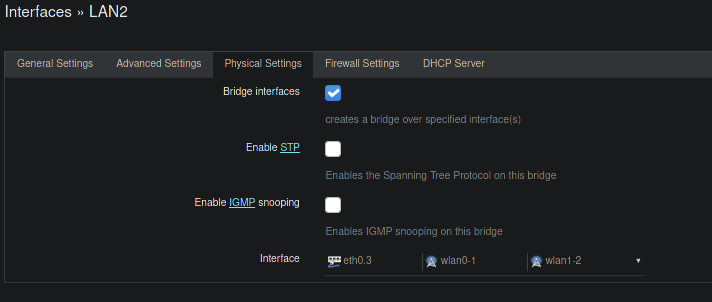
I have 4 interfaces made on Openwrt-LAN, GUEST, LAN2, and IOT.
Interfaces
LAN, Static Address 192.168.5.4/24
LAN2, Static Address 192.168.10.1/24
Guest, Static Address 192.168.30.1/24
IOT 192.168.40.1/24
(ignoring wan and wan6 interfaces)
These are all set to use 192.168.5.5 (pihole) as the DNS, except guest which uses two custom external DNS servers.
Traffic Rules
Allow-DHCP-Renew
Incoming ipv4 UDP,
from wan
to this device port 68
Guest DNS
Incoming ipv4 and ipv6
from guest
to this device port 53
(To allow DNS access for guest vlan)
Guest DHCP
incoming ipv4 and ipv6 prot UDP
from guest
to this device port 67-68
(To allow DHCP access for guest vlan)
LAN2 DNS
incoming ipv4 and ipv6
from lan2
to this device, IP 192.168.5.5
(To allow access to Pihole for DNS access on LAN2)
LAN2 DHCP
incoming ipv4 and ipv6, prot UDP
from lan2
to this device, port 67-68
(To allow DHCP access on LAN2)
LAN2 to LAN
Forwarded ipv4 and ipv6
from lan2
To lan, IP 192.168.5.5, 192.168.5.4, 192.168.5.17, 192.168.5.67
(My attempt to access my media server from LAN2, however this seems to not be working entirely as I expect? Not sure.)
IOT DHCP
incoming IPv4 and ipv6
from iot
to this device, port 67-68
(To allow DHCP access on IOT)
Printer to LAN
Forwarded IPv4 and IPv6
From IOT, 192.168.40.10
to LAN
Accept forward
(An attempt to access the printer on IOT, on LAN. I just added the printer today, however this does not seem to be working at this current moment.)
Printer to LAN2
Forwarded IPv4 and IPv6
From IOT, 192.168.40.10
to LAN2
Accept forward
(An attempt to access the printer on IOT, on LAN2. I just added the printer today, however this does not seem to be working at this current moment.)
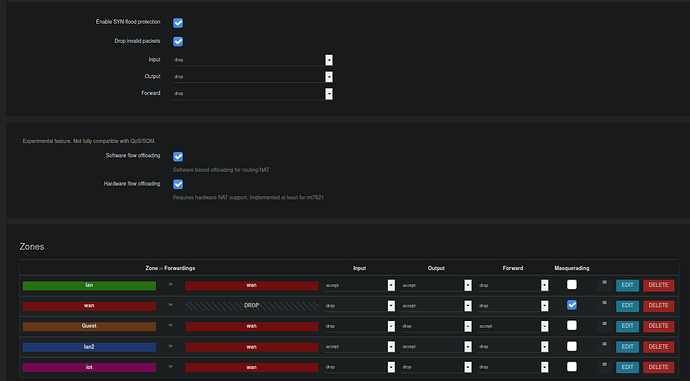
Firewall
Basic Rules
Enable SYN-flood protection on
Drop invalid packets on
Default Rules,
Input: Drop
Output: Drop
Forward: Drop
Software and Hardware flow offloading enabled.
Firewall Zones
lan >> wan
input accept
output accept
forward reject
wan >> drop
input drop
output accept
forward drop
guest >> wan
input drop
output accept
forward drop
lan2 >> wan
input accept
output accept
forward reject
iot >> wan
input drop
output drop
forward drop
Custom Rules
iptables -t nat -A PREROUTING -i br-lan ! -s 192.168.5.5 -p udp --dport 53 -j REDIRECT
iptables -t nat -A PREROUTING -i br-lan ! -s 192.168.5.5 -p tcp --dport 53 -j REDIRECT
iptables -t nat -A PREROUTING -i eth0.2 -p udp --dport 53 -j REDIRECT
iptables -t nat -A PREROUTING -i eth0.2 -p tcp --dport 53 -j REDIRECT
meant to force lan to use the pihole, will probably also have to duplicate this in for lan2, guest, and IOT after it's all setup and the switching I guess.
Wireless Access Points
5ghz
ssid: primary internet
network lan
5ghz
ssid: my internet
network lan2
2.4ghz
ssid: family internet
network: lan
2.4ghz
ssid: my internet
network: lan2
guest 2.4
ssid: guest network
network: guest
iot 2.4
ssid: iot network
network: IOT
How I Want My Setup and Issues
So my goals are as follows,
-
Both LAN and LAN2 should be able to access the router configuration page, however Guest, IOT should not.
-
I want my family LAN to not be able to interact with my LAN2 in any way except specified.
The specifications are, that I can access the Pi-Hole on LAN for my DNS at LAN2. -
Guest should be completely isolated, not even have access to the Pi-Hole for DNS.
I setup custom DNS servers for the guest interface.
It seems like I may have gotten the guest and LAN and LAN2 setup properly for wireless, however I'd appreciate if it could be checked over. I can access websites, and I have my DNS for LAN and LAN2 interfaces set to use 192.168.5.5 (pihole), and I can connect to websites. However I am having issues with my media server when crossing over (the media server is still on LAN, I talk about this below)
I set this up using the traffic rules, however I am not entirely sure if it is setup as I expect it to be?
-
I have the two unmanaged switches, one for family and one for my stuff, I was hoping to separate these so say SWITCH1 is for LAN, and SWITCH2 is for LAN2 and they can't interact with each other (again except for what is specified, so like the Pi-Hole being able to cross the network for DNS).
This I have not messed with yet, as I am not familiar with tagging and stuff, and was getting confused. I figured it'd be best to wait and setup everything else and ensure it works 100% then mess with this. -
I do have a media server (jellyfin/airsonic) (which is also used as a computer), which I'd like to be on LAN2, but it also needs access to LAN for NGINX on the Pihole.
However, I also don't want LAN to lose access to a direct connection to the media server, and be required to travel through the public internet (which the media server can do, however the local link would be nice to keep), but I also don't want to expose that computer to LAN besides for the media server.
With my current setup, if I cross over to my LAN2 network, I get a "Forbidden Rejected request from RFC1918 IP to public server address" error when going to the jellyfin domain, however I have no issues pinging that device local IP across vlan. I can reach it no issues if I hop onto LAN vlan.
I'm unsure exactly how I would properly set this media server up for firewall? It's still on LAN though because LAN users need to access it, and if I move it over, they will not (for the same reason I can't access it on LAN2 while it's on LAN.) Also I haven't figured out switching, and this device is wired.
- I have the printer on the IOT network, I do not want anything on this network to have access to public internet, I've not dealt with a printer before, however I assume this is possible as it receives the data from the computers on the lan, so I see no reason why it needs to connect to the public internet. So I would like it to be completely isolated to LAN and LAN2 for usage, and have ZERO internet connectivity. Of course anything else that goes on this interface will not have internet too I am aware.
Would greatly appreciate help again, I have read through the docs, however I am still slightly new to all of this and it has been giving me massive headaches, I've been at this one and off for months trying to get everything setup properly. Some things are working, some are kind of working, and some just don't seem to be working. Would appreciate help.