Hello,
I'm using OpenWRT for a few weeks and I'm impressed. I'm using Archer C6 right now, I ordered AX3200 to flash it with OpenWRT.
I was playing with my simple home-network segmentation. I just want to have physical lan port 1 in "guest" VLAN, because I have some service running on PC that I don't trust. I struggled to manage it because I'm a beginner in Networking and the web is full of different explanations and more complicated than I need. Now I somehow made it. After watching a lot of videos and tutorials I did it in that way:
I added "guest" VLAN with ID 20 and assigned "untagged" port 1 to it. VLANs "lan" and "wan" stayed as they were by default.
I created Device "guest" with IP range 192.168.20.1 /24 and assign "eth0.20" to it
I created Interface "guest" and assigned Device "guest" to it.
I didn't use any Bridge VLAN Filtering, because I don't know yet how to use it. It works now as I wanted it. The IP on my "guest" PC now has an IP in the range 192.168.20.xxx, it can connect to the Internet, it cannot access the router on 192.168.1.1. I am almost satisfied with it, I just need to add access from PC in "lan", because I'm connecting to it via RDP.
So my question is, how to add rule (or maybe I can do some other thing), that I could access from "lan" to "guest", but not vice versa?
Thank you for your help. If you need more information I can give it to you.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.134",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C6 v2 (EU/RU/JP)",
"board_name": "tplink,archer-c6-v2",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "ath79/generic",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 3 4 5'
option vid '1'
option description 'LAN'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
option description 'WAN'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t 2'
option vid '20'
option description 'GUEST'
config interface 'guest'
option proto 'static'
option device 'guest'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config device
option type 'bridge'
option name 'guest'
list ports 'eth0.20'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
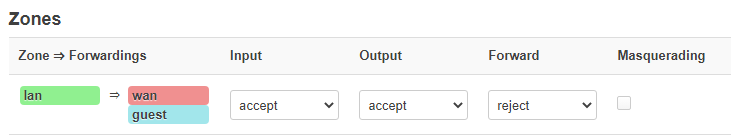
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding
option src 'guest'
option dest 'wan'
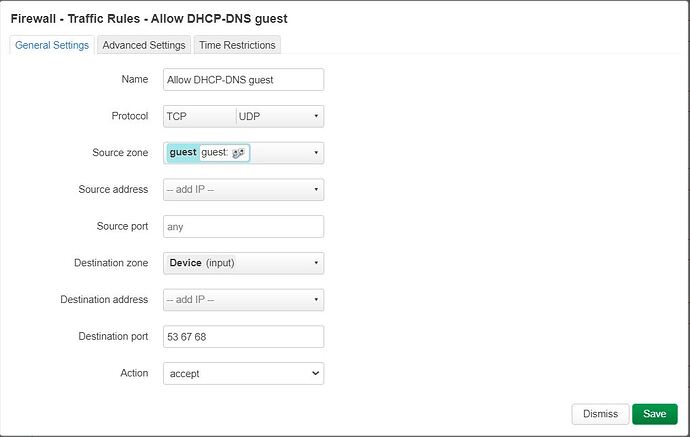
config rule
option name 'Allow DHCP-DNS guest'
option src 'guest'
option dest_port '53 67 68'
option target 'ACCEPT'
Your device is not using DSA, so bridge vlan filtering is not relevant here. Everything in the configuration looks correct.
Tesla87:
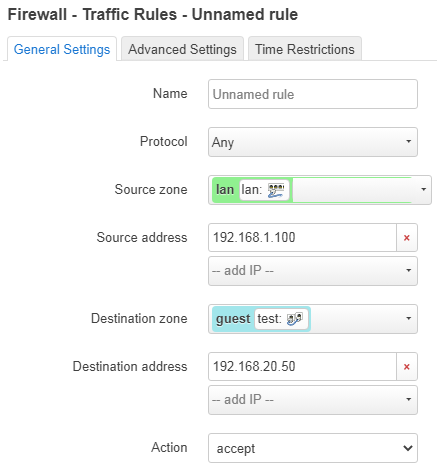
So my question is, how to add rule (or maybe I can do some other thing), that I could access from "lan" to "guest", but not vice versa?
The fastest way is to allow forwarding lan=>guest.
If you want to be more restrictive, create a traffic rule.
This is incredible, it works, I tried both of your suggestions. From small example I'm now getting better understanding of what is going on.
If I try to ping from "lan" to "guest" it fails. Probably this is normal, because Firewall now refusing answers sent from guest?
Thank you for your help.
Best regards