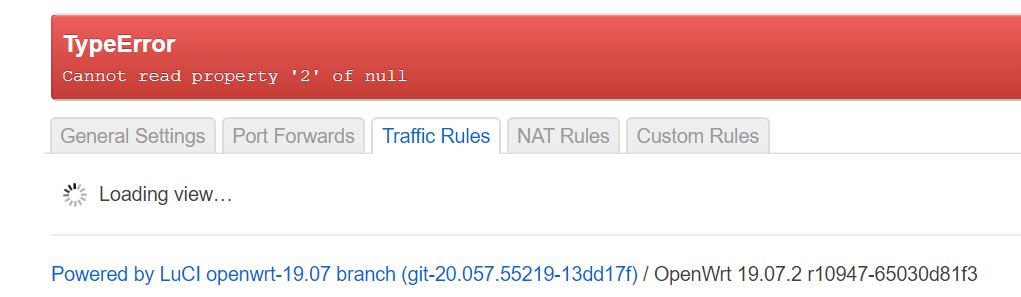
Anyone can help a newbie with the following. I was adding a Guest wifi using VLAN in luci and when it came to open the firewall to traffic I can't even get to the Traffic Rules.
https://openwrt.org/docs/guide-user/network/wifi/guestwifi/guest-wlan-webinterface
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
root@OpenWrt:~# uci export network; uci export wireless; \
> uci export dhcp; uci export firewall; \
> head -n -0 /etc/firewall.user; \
> ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
>
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd34:9dfb:1b8c::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
option type 'bridge'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr '[REDACTED]'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 2 3 4 5'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
config interface 'Guest'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:00.0'
option htmode 'VHT80'
option channel 'auto'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option key '[REDACTED]'
option encryption 'psk'
option disabled '1'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'platform/ahb/18100000.wmac'
option htmode 'HT20'
option channel 'auto'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option key '[REDACTED]'
option encryption 'psk-mixed'
option ssid '2'
config wifi-iface 'wifinet2'
option encryption 'psk-mixed'
option device 'radio0'
option mode 'ap'
option key '[REDACTED]'
option network 'lan'
option hidden '1'
option ssid '[REDACTED]'
config wifi-iface 'wifinet3'
option encryption 'psk-mixed'
option device 'radio1'
option mode 'ap'
option key '[REDACTED]'
option network 'lan'
option ssid '[REDACTED]'
config wifi-iface 'wifinet4'
option isolate '1'
option ssid 'OpenWrt-TEST'
option device 'radio1'
option mode 'ap'
option macfilter 'deny'
option hidden '1'
option key '[REDACTED]'
option encryption 'psk-mixed'
option network 'Guest'
option disabled '1'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
list server '8.8.8.8'
list server '8.8.4.4'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option mac '[REDACTED]'
option dns '1'
option ip '[REDACTED]'
option leasetime 'infinite'
option name 'Asus-GuestAP'
config host
option mac '[REDACTED]'
option name 'WDMyCloud'
option dns '1'
option ip '[REDACTED]'
option leasetime 'infinite'
config host
option mac '[REDACTED]'
option leasetime 'infinite'
option dns '1'
option name 'Alexa'
option ip '[REDACTED]'
config host
option mac '[REDACTED]'
option leasetime 'infinite'
option dns '1'
option ip '[REDACTED]'
config host
option mac '[REDACTED]'
option leasetime 'infinite'
option dns '1'
option ip '[REDACTED]'
option name 'MiLight-Living'
config host
option mac '[REDACTED]'
option leasetime 'infinite'
option dns '1'
option name 'MiBox-S'
option ip '[REDACTED]'
config host
option mac '[REDACTED]'
option name 'pi4-lan'
option dns '1'
option ip '[REDACTED]'
option leasetime 'infinite'
config dhcp 'Guest'
option start '100'
option limit '150'
option interface 'Guest'
option leasetime '1h'
package firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option ac_enabled '1'
option src '*'
option dest 'wan'
option extra '--kerneltz'
option proto '0'
option target 'REJECT'
option weekdays ' mon tue wed thu sat sun'
option enabled '1'
option src_mac '[REDACTED]'
option start_time '00:00'
option stop_time '05:00'
option name 'Eve'
config rule
option ac_enabled '1'
option src '*'
option dest 'wan'
option extra '--kerneltz'
option proto '0'
option target 'REJECT'
option weekdays ' fri'
option enabled '1'
option name 'Fri'
option src_mac '[REDACTED]'
option start_time '23:00'
option stop_time '24:00'
config rule
option ac_enabled '1'
option src '*'
option dest 'wan'
option extra '--kerneltz'
option proto '0'
option target 'REJECT'
option enabled '1'
option name 'AM'
option src_mac '[REDACTED]'
option start_time '06:00'
option stop_time '13:00'
config rule
option ac_enabled '1'
option src '*'
option dest 'wan'
option extra '--kerneltz'
option proto '0'
option target 'REJECT'
option enabled '1'
option name 'PM'
option src_mac '[REDACTED]0'
option start_time '14:00'
option stop_time '18:00'
config zone
option network 'Guest'
option forward 'REJECT'
option name 'Guest'
option output 'ACCEPT'
option input 'REJECT'
config forwarding
option dest 'wan'
option src 'Guest'
config rule
option name 'Allow DNS Queries'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule
option name 'Allow DHCP request'
option src 'guest'
option src_port '67-68'
option dest_port '67-68'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6-guest'
option src 'guest'
option proto 'udp'
option dest_port '547'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow guest ICMP input'
option src 'guest'
option proto 'icmp'
option target 'ACCEPT'
option family 'ipv6'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
8: br-wan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 1[REDACTED]/24 brd 1[REDACTED] scope global br-wan
valid_lft forever preferred_lft forever
default via [REDACTED] dev br-wan src 1[REDACTED]
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
[REDACTED]/24 dev br-wan scope link src [REDACTED]
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local scope link src 192.168.1.1
broadcast 192.168.70.0 dev br-wan table local scope link src [REDACTED]
local [REDACTED] dev br-wan table local scope host src [REDACTED]
broadcast [REDACTED] dev br-wan table local scope link src [REDACTED]
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
I cannot see where is that in the configs.
Other than that did you create these time based rules in Luci, Uci, or direct edit of the firewall file?
1 Like
Also, explain why you added the option extra '--kerneltz' line to the firewall rules; but then use OpenWrt syntax to define times.
All of this I configured in Luci software. So I am not sure why these rogue items are in here. UCI is new to me.
I wound it back and can see the page I wanted. Will live without the scheduling until I learn some schedule rules myself. Was hoping the luci software would have saved me a learning curve. Thanks for the advice.
So you did want to create scheduled firewall rules...OK...now I'm lost.
Yes, I hope you figure out what you desire. Maybe this will help:
(Also, you can use the web GUI...your comments imply that you're having some difficulty and didn't wish to ask how to make a rule. Feel free to search or make another thread about how to make scheduled firewall rules.)
Yes the guest wifi with MAC scheduling was intended. We have a young child and a nanny who easily get distracted by her phone and hogging bandwidth. Plan is 1) WLan [isolate], 2) automate the on/off wifi access [scheduled breaks] and 3) BW limiting. Thanks again, will take a look and starting with the guest WLan...step-by-step.
1 Like
system
May 17, 2020, 4:15pm
11
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.