Ahoy friends.
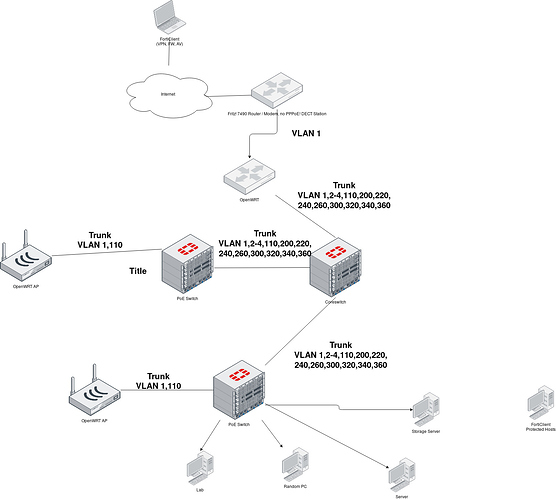
I got the following setup
I got a Fritz! 7490 Router, acting as modem and router for dialing in.
The OpenWRT Router is connected to a trunk port.
Vlan 1 is the VLAN of the 7490 router.
To the OpenWRT device (Raspberry Pi 4) there is a trunk port connected to the router deploying all vlans
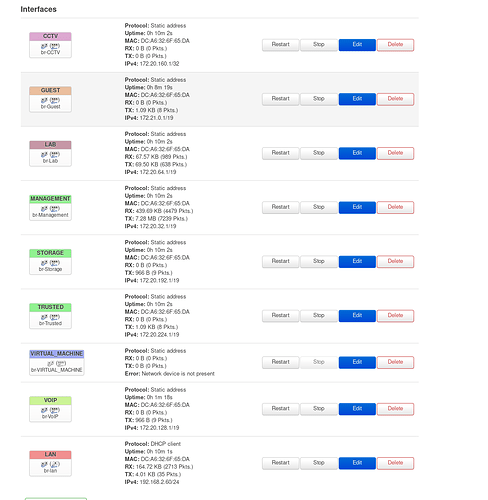
VLAN 1 Untrusted OK
VLAN 2 Lab
VLAN 3 Trusted Devices
VLAN 110 Management, Zabbix
VLAN 300 VoIP
VLAN 200 Virtual Machines, Server
VLAN 220 Storage Server
VLAN 320 Guest
VLAN 340 CCTV
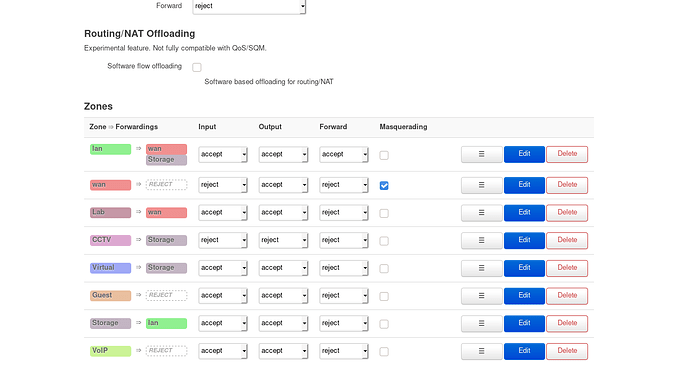
And at the bottom there are my Firewall rules.
I want the network acting like this:
VLAN 1: It's the native VLAN on all switchports, random pc's should be connected to it, and they should use the 7490 Router, not the OpenWRT one.
The OpenWRT Router is also connected to it as an exposed host, in order to manage the rest.
VLAN 2 (Lab):
It's my LAB setup, it should only have access to the internet, but not to the other VLANs at all.
Clients in this VLAN should be able to contact each other.
VLAN 3 (Trusted):
Trusted devices should be access to the internet, but should also be able to access the Storage Server in VLAN 220. Clients should see each other
VLAN 110 (Management):
No access to the internet, or other VLANs. Only way to access should be a VPN connection to the router, or using an access port VLAN 110 on the switch. Clients don't need to see each other, but that's not necessary. It should be isolated.
VLAN 300 (VoIP):
VoIP devices should only route traffic to the Fritz! 7490 Router. (Network 192.168.2.0), in order to let the Fritz! 7490 do the work with the SIP stuff.
No access by other VLANs or to other VLANs
VLAN 200 (Virtual Machines):
Should have access to the internet, and to the Storage Server in VLAN 220.
Will be used to be accessed through the internet using port forwarding.
VLAN 220 (Storage Server)
VLAN for only one device. It should have internet access only, and it can be accessed through the Internet using port forwarding, and VLAN 200 (Virtual Machines), VLAN 3 (Trusted).
VLAN 320 (Guest)
Should only have access to the internet, and nothing else.
VLAN 340 (CCTV)
Should only have access to the Storage Server VLAN (VLAN 220), nothing else.
I'm quite struggeling in order to get it working, i hope someone could help a bit 
I'd also like to limit the access to the web gui and ssh of the OpenWRT device to VLAN 110.
How do i have to mess with the firewall rules in order to get it working?
I'd like to let the Fritz! 7490 deal with the VLAN 1 and their unimportant untrusted devices only.
Is there also a way to assign a hostname to servers, and virtual machines, in order to be accessed by the allowed zones/vlans?
Do i have to create static routes, or how can i get this work?
Some more question:
Let's think, i'd like to add some more VLAN to my OpenWRT APs, can i "copy" these firewall rules, and use exact the same rules, when messing with the same VLAN on the AP?
Thanks in advance!