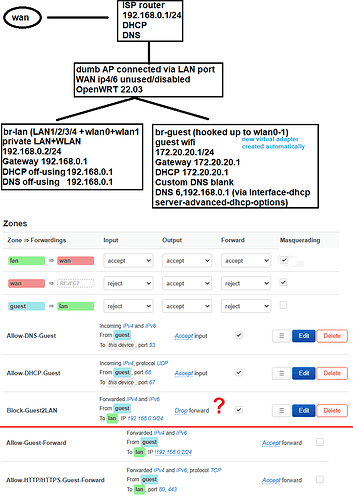
I just set up guest wifi following below tutorials and making proper adjustments along the way to accommodate for different subnets, bridge on lan/wlan and lack of WAN connection (ports not used).
First was struggling a bit with DNS traffic as none of the tutorials said settings presented were only good if you use external DNS. Since I tried to use internal DNS I had to set up "dhcp-option" to force different subnet dns (from main LAN), otherwise guest-wifi would get DNS same as gateway - 172.20.20.1 and no internet. I think that should be included in "guestwifi_dumbap" wiki. (OpenWRT wiki admin anyone?)
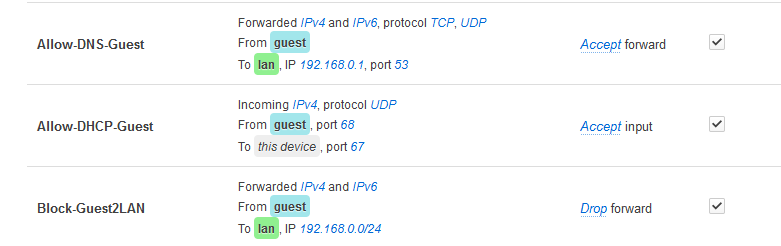
Anyways with that out of the picture I finally got internet in guest. Problem now is guest clients can browse local resources, they can get to admin portal of ISP router 192.168.0.1, which ofc holds dhcp and dns for entire network. With only two rules created for dhcp and dns all works as described (first two on the screenshot). When I turn on 3rd rule "Block-Guest2LAN" to drop forward traffic from guest to lan (rule being lower than dhcp and dns accept rules) all traffic dies. Turns out it won't work if you're trying to use internal DNS or a pihole on main lan. Seems rule priority is not working here.
Using different rules from "guestwifi/extras" doesn't seem to do what I want either. "Allow-Guest-Forward" has both internet and main router admin page working "Allow-HTTP/HTTPS-Guest-Forward" same as above.
The only thing that's consistent no matter the rules is no OpenWRT admin webpage for dumbAP 192.168.0.2.
With some additional devices and services in mind I'd like to stop traffic from guest to private lan altogether and leave only internet.
No to the point. How to configure the firewall to use internal DNS servers? I mean it works with external, sure, but that means if I had a pihole locally I wouldn't be able to use it or had to make a separate subnet just for it so it doesn't fall under "block" rule.
Can anyone help me, please? Thanks.