grosjo
December 14, 2024, 8:57am
1
Hi
I made so to be able to place some limitations on the traffic between the lans
However, before putting limitation, I would like those 2 to, for now, at least ping each other
The firewall is et as follows
but no commuinciations between the lan
What I am missing ?
grosjo
December 14, 2024, 8:58am
2
One more thing
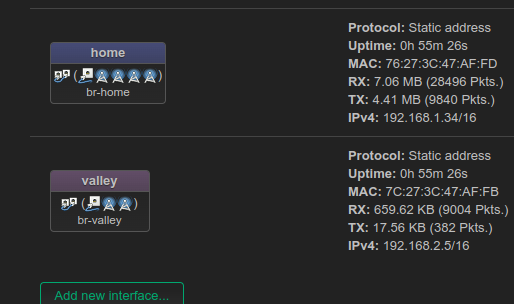
"home" is 192.168.1.0/24 (netmask is 255.255.0.0)
from any device on home LAN, the ping to any device on valley times out and vice versa
brada4
December 14, 2024, 9:02am
3
Networks overlap. You need /23 or more to route between them
1 Like
grosjo
December 14, 2024, 9:06am
4
@brada4 Can you explain a bit more ?
brada4
December 14, 2024, 9:12am
5
It is same subnet in both networks 192.168/16
1 Like
boxman
December 14, 2024, 9:14am
6
do you have 255.255.255.0 or 255.255.0.0 ?
2 Likes
This is 192.168.0.0 /16 - or 192.168.0.0 -192.168.255.255 (mask 255.255.0.0)
That means you told your router that 192.168.1.0 /24 and 192.168.2.0 /24 could be [reached] in the same [physical] network Yet you assigned them to different physical interfaces
This is incorrect 255.255.0.0 is not the OpenWrt default
Multiple users have suggested you fix this
See: https://en.wikipedia.org/wiki/Classless_Inter-Domain_Routing#IPv4_CIDR_blocks
1 Like
lleachii:
This is 192.168.0.0 /16 - or 192.168.0.0 -192.168.255.255 (mask 255.255.0.0)
That means you told your router that 192.168.1.0 /24 and 192.168.2.0 /24 could be [reached] in the same [physical] network Yet you assigned them to different physical interfaces
This is incorrect
255.255.0.0 is not the OpenWrt default
brada4:
Picture has /16
grosjo:
And that part - you configured /16, not /24.
1 Like
boxman
December 14, 2024, 2:06pm
10
o wow, so many wrongs on the first pics
if you still have prb come back after that
grosjo
December 14, 2024, 3:37pm
11
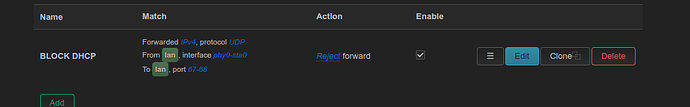
So I put them all in one zone
and put the following rule
However, DHCP request coming from phy0-sta0 are not blocked
# nc -vz -u 192.168.2.1 67
Connection to 192.168.2.1 67 port [udp/bootps] succeeded!
Why ?
grosjo
December 14, 2024, 3:53pm
12
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config rule
option name 'DHCP'
option direction 'in'
option device 'phy0-sta0'
option family 'ipv4'
option src 'lan'
option target 'REJECT'
option dest 'lan'
list proto 'udp'
option dest_port '67-68'
grosjo
December 14, 2024, 4:00pm
13
The same test with TCP 80 gives the same result (packets not dropped/rejected)
brada4
December 14, 2024, 4:03pm
14
grosjo:
device 'phy0-sta0'
You can not filter bridge members with inet table. Thanks. You fixed your subnets so question is over.
grosjo
December 14, 2024, 4:20pm
15
Why are you so impolite and unfriendly?
brada4
December 14, 2024, 4:22pm
16
What? You think you can stare at your misconfigurations until they go away?
grosjo:
Why ?
Simple.
DHCP requests aren't forwarded anyway
So a rule specifying from LAN to LAN (or home/valley) won't work
Now you only have one interface and firewall zone, there's nowhere to forward
Perhaps you should explain the goal of your firewall rule so we can better assist you.
From what SRC - to what DST?
Where's this firewall rule?
Let's take a slightly different approach:
What are the specific goals you have in terms of how you want to allow/limit traffic between the two networks?
let's take a look at the configuration as it stands now to figure out if there are any current misconfigurations and/or recommended changes to make this easier.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
1 Like
slh
December 14, 2024, 6:55pm
19
Just in general, anything but /24 subnets is almost always a mistake and a kludge to paper over a real bug, at least as long as you are in a 'home' environment.
Yes, there are reasons for a different subnetting (particularly in the business sector with many (>>256) clients) and there are valid configurations using those, but only if you really know what you're doing and why.
1 Like
grosjo
December 14, 2024, 11:55pm
20
While I appreciate the effort, all these response have little to do with the question
To rephrase:
The openwrt box has several interfaces (ethx, and phy0-ap0/1/2 and phy-sta0/1)
One of those interfaces is phy0-sta0, reaching the other lan (another openwrt box across the forest)
->I want to block (drop/reject) some packet going through this interface
What is the best configuration on OpenWrt ?
Thank you