Hi There,
I'm using following config 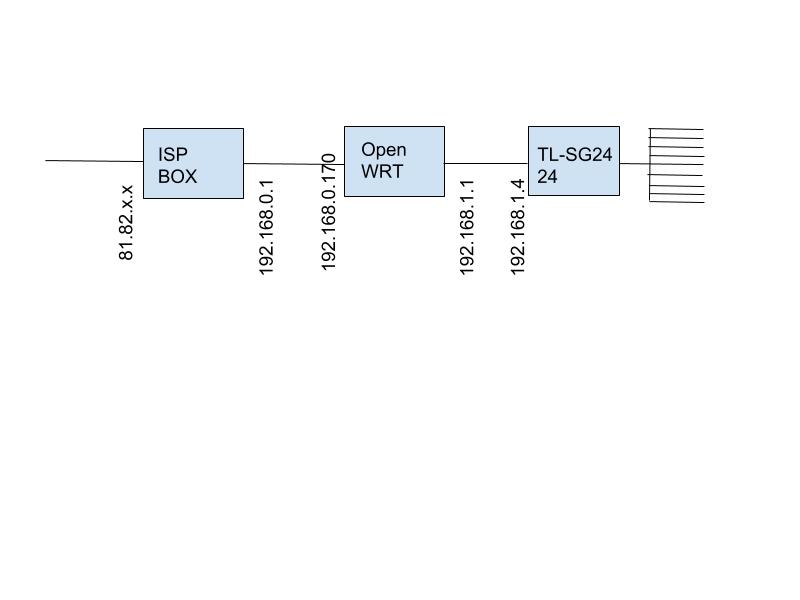
When I go to http://192.168.1.1/cgi-bin/luci/admin/status/realtime/connections I see a lot of connections and some disturbs me...
-
|IPV4|UDP|QNAP-TS869L.lan:53626|li83-132.members.linode.com:20001|604.62 KB (5368 Pkts.)|
-
|IPV4|UDP|QNAP-TS869L.lan:53626|li1552-65.members.linode.com:20001|603.70 KB (5365 Pkts.)|
-
|IPV4|UDP|QNAP-TS869L.lan:53626|101.200.208.178:20001|365.09 KB (4591 Pkts.)|
-
|IPV4|UDP|QNAP-TS869L.lan:53626|211.149.146.109:20001|365.04 KB (4590 Pkts.)|
-
IPV4|TCP|Clevo-901c.lan:49166|a173-223-106-9.deploy.static.akamaitechnologies.com:80|24.90 KB (215 Pkts.)
I have some questions..
I thought that http = 80 and https =443 why does the source uses sometimes very high numbers? Like in Line 5?
I also noticed that sometimes the source is using the same port but is going to a different address on the destination see line 1,2,3 Is this normal behavior?
I also noticed that sometimes the source is using different ports but is going to the same destination, is this normal behavior?
Some destinations have easy reading web page adres in them others are hosted in China or the Netherlands where I don’t have a server running. How can I determine how my NAS (QNAP) is going to member.linode.com and eventually closes this connection.
Last question is the standard firewall from OPENWRT considered as everything is closed and needs to be opened on command, the reserve or otherwise?
Is there a good way to scan for open ports? I ask this because when I use a scanner on my phone when on wifi I get different results for port 192.168.0.170 and 192.168.1.1.
Sorry for this long epistel I hope somebody or several can shed some light into the tunnel.
Thanks for reading
Guy