Right. It's astounding what a good night's sleep and shaking off a cold can do. I was giving you bad advice yesterday. Apologies for that. It was almost right, but not quite.
You're trying to prevent certain traffic from making the transition from one zone (LAN) to another one (WAN). The chain in question is FORWARD. You can insert a rule at the top of that chain to either DROP or REJECT the traffic you don't want to permit. (DROP will not respond to the source so the source has to time out; REJECT will actively tell the source to go away.)
Today I set up a test enviroment in VMware, which looks like this:
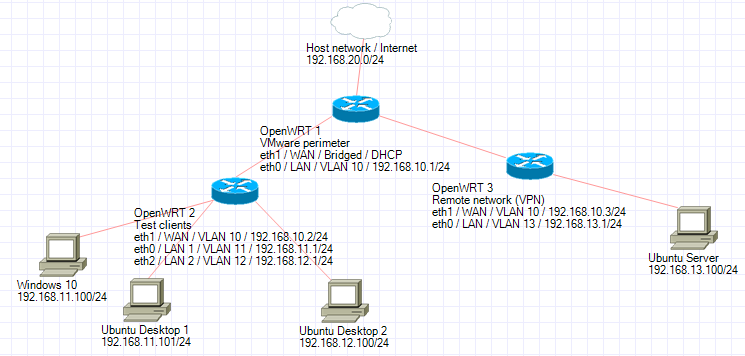
On OpenWRT 2 there are three firewall zones, LAN1, LAN2, and WAN, corresponding to the three network segments. I have configured the firewall to permit LAN1 and LAN2 to talk freely with each other, in addition to the default rules permitting outbound traffic.
I tested with ubuntudesktop1 (192.168.11.101) and ubuntudesktop2 (192.168.12.100). I also used my physical perimeter router (192.168.2.1 - on the far side of the cloud, not on the diagram) as a target "somewhere else on the Internet", to demonstrate what happens for connection attempts which go via the WAN.
Without any additional iptables shenanigans:
iplaywithtoys@ubuntudesktop1:~$ ssh 192.168.12.100
iplaywithtoys@192.168.12.100's password:
iplaywithtoys@ubuntudesktop1:~$ ssh admin@192.168.2.1
admin@192.168.2.1's password:
iplaywithtoys@ubuntudesktop2:~$ ssh 192.168.11.101
iplaywithtoys@192.168.11.101's password:
iplaywithtoys@ubuntudesktop2:~$ ssh admin@192.168.2.1
admin@192.168.2.1's password:
I can insert an iptables rule at the top of the FORWARD chain to reject all SSH traffic, regardless of where it's going: root@OpenWrt2:~# iptables -I FORWARD -p tcp -m tcp --dport 22 -j REJECT
Now, if I attempt the same tests as before, here's the result:
iplaywithtoys@ubuntudesktop1:~$ ssh 192.168.12.100
ssh: connect to host 192.168.12.100 port 22: Connection refused
iplaywithtoys@ubuntudesktop1:~$ ssh admin@192.168.2.1
ssh: connect to host 192.168.2.1 port 22: Connection refused
iplaywithtoys@ubuntudesktop2:~$ ssh 192.168.11.101
ssh: connect to host 192.168.11.101 port 22: Connection refused
iplaywithtoys@ubuntudesktop2:~$ ssh admin@192.168.2.1
ssh: connect to host 192.168.2.1 port 22: Connection refused
Let's remove that rule - iptables -D FORWARD -p tcp -m tcp --dport 22 -j REJECT - and replace it with one which rejects all SSH traffic which is destined for the WAN, regardless of its origin. This is done by modifying the iptables directive to include a specific outbound interface: iptables -I FORWARD -o eth1 -p tcp -m tcp --dport 22 -j REJECT
And the results now are:
iplaywithtoys@ubuntudesktop1:~$ ssh 192.168.12.100
iplaywithtoys@192.168.12.100's password:
iplaywithtoys@ubuntudesktop1:~$ ssh admin@192.168.2.1
ssh: connect to host 192.168.2.1 port 22: Connection refused
iplaywithtoys@ubuntudesktop2:~$ ssh 192.168.11.101
iplaywithtoys@192.168.11.101's password:
iplaywithtoys@ubuntudesktop2:~$ ssh admin@192.168.2.1
ssh: connect to host 192.168.2.1 port 22: Connection refused
This approach allows you to block traffic regardless of source. If you add the appropriate iptables rule to /etc/firewall.user then it will apply regardless of any zones you may add.
As has already been mentioned, you can also achieve similar results by manipulating /etc/config/firewall or even using the GUI.
As another example, I used the GUI to create a rule to block SSH only from lan2:

The corresponding entry in /etc/firewall/user is:
config rule
option enabled '1'
option proto 'tcp'
option dest_port '22'
option name 'Block SSH from lan2'
option family 'ipv4'
option src 'lan2'
option dest 'wan'
option target 'REJECT'
And the test:
iplaywithtoys@ubuntudesktop1:~$ ssh admin@192.168.2.1
admin@192.168.2.1's password:
iplaywithtoys@ubuntudesktop2:~$ ssh admin@192.168.2.1
ssh: connect to host 192.168.2.1 port 22: Connection refused
The above approach could be taken with any new interfaces: create the interface, create a firewall zone for that interface, configure any inter-zone forwarding, configure custom rules to allow or block certain traffic. But if you never want to allow specific traffic, regardless of how many new interfaces or zones you might add, then just use /etc/firewall.user and an explicit iptables command to insert the drop/reject rule at the top of the FORWARD chain.
Lastly, if you don't care about segregating the two LAN interfaces, you could add them both to the same LAN zone, and just use one set of rules to allow or block traffic to and from the WAN. You could also add new interfaces to the same LAN zone, and have the existing firewall rules automatically take effect.


