Hi,
If you're like me, you have several hostiles devices that will automaticall self-destruct if ever allowed to use their call-home backdoor on the unfiltered internet.
What we need to not accidentally destroy these devices is White List Only internet access for unknown device.
Or "DHCP client whitelist", not sure exactly what to call this, it has other uses.
So first how to do this.
Easy mode is, somehow set default Gateway for dnsmasq either to a unused address on your network, or maybe if that's possible, give no gateway address ?
First warning here, Android devices will bounce off a wifi that doesn't give them a valid gateway address and we might also need "fakeinternet" as part of this package.
Ok, now, a new unknown device connects to the network, it gets a dynamic address and a wrong or blank gateway. We're half-way there already !
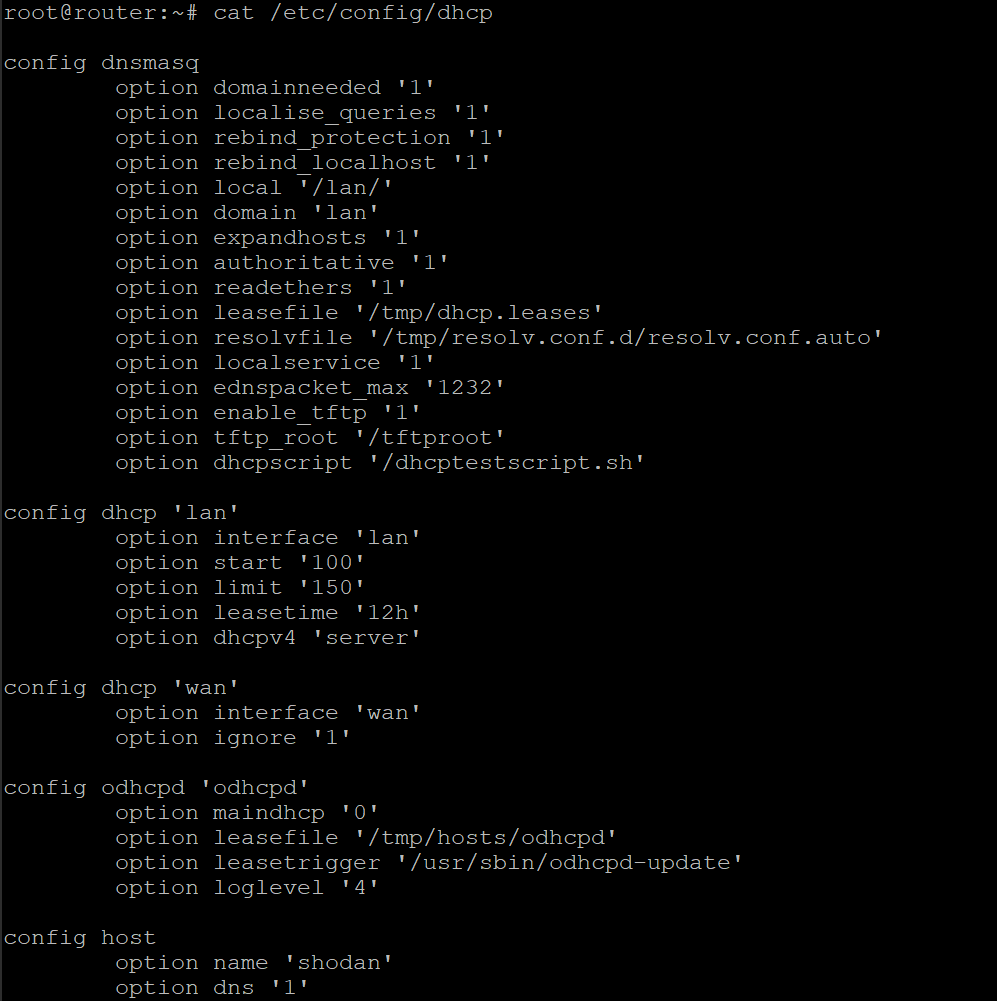
Next, each new dhcp client needs to be added to the whitelist file /etc/config/dhcp
First thing, we need a tag that contains the good gateway address
config tag 'good_gateway'
list dhcp_option '3,192.168.1.88'
list dhcp_option '6,192.168.1.112'
This will set both the gateway, helpfully named dhcp_option '3 and the DNS named dhcp_option '6
Last step, adding dhcp clients to the whitelist
config host
option name 'mycomputersname'
option dns '1'
option mac 'AB:CD:00:12:34:5F'
option ip '192.168.1.10'
option tag 'good_gateway'
I'm not sure if option dns '1' needs to be defined
I don't know if you have to decide on an ip address for every single device with option ip '192.168.1.10' preferably this line can be left off and every client just gets an address from the pool
I don't know if you can specify more than one tag per client, that would be great
And now, the Feature Request part of this message
It should be possible in LuCI to do this without modifying config files
So here is what needs to change to perform the minimum requirements
First, there needs to be a way to set the DHCP server's default gateway IP
I had a look in the current interface and I cannot see how to specify a blank or invalid or unused IP address as the gateway address
I had a look at the config files, but still can't tell where the dhcp server is being told what gateway to use
It is probably using the br-lan interface called WAN's IP address
But I don't want to set that address to a blank, invalid or unused address !
So I have to find how to set the dhcp server's default gateway address to an arbitrary value
Ah, it might be addign
option '3,192.168.1.88'
to the config dnsmasq section of /etc/config/dhcp
--------FEATURE REQUEST HERE !--------
So, ok ! Please add the ability to specify Option 3
To https://router.lan/cgi-bin/luci/admin/network/dhcp the "General Settings" page
(also option 6 DNS please)
(Also, if if you're feeling fancy, check if the option is hardcoded in the config file, if it isn't then write "automatic" in the text box, maybe with the current value "automatic(192.168.1.1)"
--------FEATURE REQUEST HERE !--------
Next, we need to define tags and assign them to static leases
First we need a way to list and assign, at least one, tag to a static lease
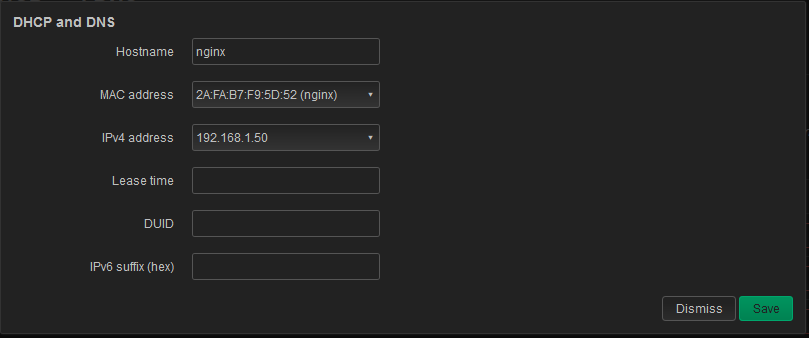
This is on the Static Lease page
(how do I make a link to the static lease page ?! It always links to https://router.lan/cgi-bin/luci/admin/network/dhcp#)
This is on the Static Lease page
As you can see, no way to set a tag
So, what we need here is
A combobox where you can see all the defined tags, and choose, at least, one
Then add, at least one, tag name to the "config host" section of the config file for that host
The text is literally
option tag 'good_gateway'
--------FEATURE REQUEST HERE !--------
Add ability to select one (or more) tag on the "DHCP and DNS/Static leases/my host/Edit" page
--------FEATURE REQUEST HERE !--------
Also, how do I NOT set an hardcoded IP address here ?
Can I just leave IPv4 address blank here ?
I'm going to need to make so many host definition, I don't want to give them all an hand picked fixed address ! It should be obvious how to create a "dynamic static lease", yes, you read that right.
Ok next we need to create Tags with our settings
Tags are really simple it's just this text
config tag 'deadend_gateway'
list dhcp_option '3,192.168.1.254'
list dhcp_option '6,192.168.1.253'
config tag 'good_gateway'
list dhcp_option '3,192.168.1.88'
list dhcp_option '4,192.168.1.55'
list dhcp_option '6,192.168.1.112'
Oh BTW, option 4 is the NTP server
config tag 'Android_fakeinternet_gateway'
list dhcp_option '3,192.168.1.36'
list dhcp_option '6,192.168.1.111'
In this case 192.168.1.111 is a DNS server which runs anti-google DNS filtering
and 192.168.1.36 is a gateway with google/android style fakeinternet
config tag 'Android_filtered_gateway'
list dhcp_option '3,192.168.1.35'
list dhcp_option '6,192.168.1.111'
And this is good internet, but all the google websites are DNS filtered AND IP Banned from that gateway
--------FEATURE REQUEST HERE !--------
Ability to see, list, create and modify DHCP option tags
In https://router.lan/cgi-bin/luci/admin/network/dhcp# probably a newtab, similar to "IP Sets" but call it "DHCP Tags", create custom tags and add them to the file /etc/config/dhcp
--------FEATURE REQUEST HERE !--------