Hi,
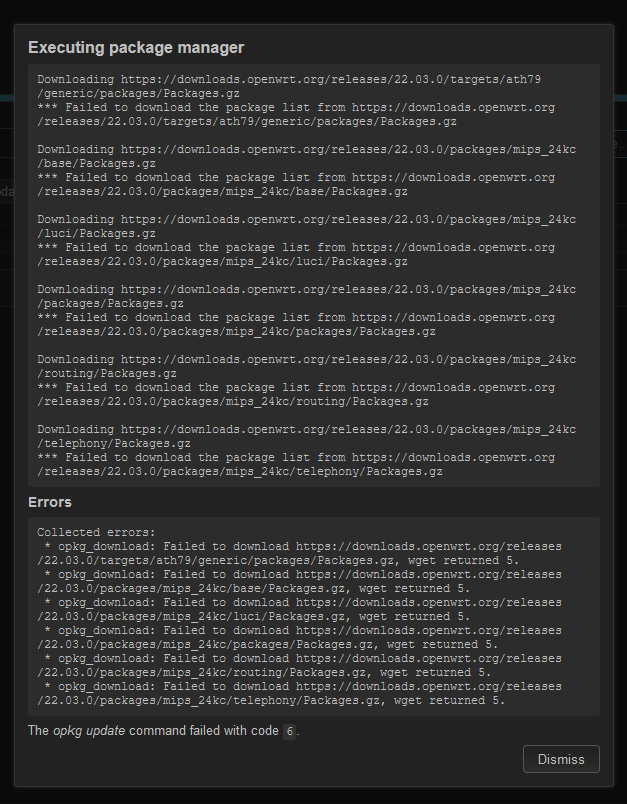
I've just woken up an old router of mine, went to update the package list and got the following
Now, from the user's point of view it is not clear what is going on, does the router have DNS, can it even ping the internet ?
For typical user this means openwrt is now broken and needs re-flash
So, I poped the hood and
So here at minimum the package manager should investigate what it can
Let the user know the certificate are failing, especially which certificates, the expiration dates on those certificates and show current system time to the user.
Also, if the remote website is reachable, present the user with the info of the remote site's certificate
At least name, address, organisation, certificate creation and expiration date, and finally, ask the user if the remote certificate should be accepted (after they've made sure they're not victim to a MitM attack). And if so, place the new certificate, in the keyring and accept as valid.
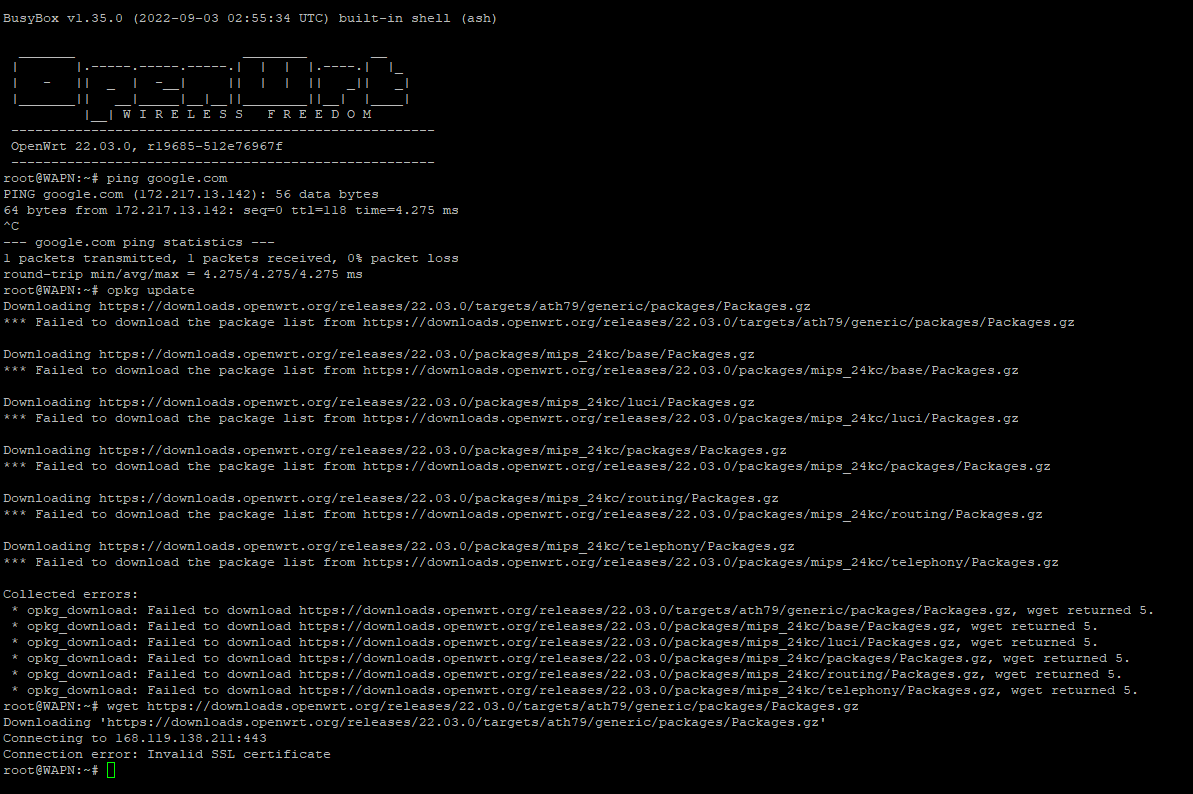
Anyway, at this point, not sure what is wrong. Found several posts with similar issues
First I managed to update with --no-check-certificate
opkg update --no-check-certificate
that worked, then I tried updating ca-bundle, strangely no output from that command
root@WAPN:~# opkg upgrade ca-bundle --no-check-certificate
root@WAPN:~#
Tested opkg update, still getting that error
Ok, upgrade everything
Ah, no, doesn't work that way
root@WAPN:~# opkg upgrade --no-check-certificate
opkg: the ``upgrade'' command requires at least one argument
Ok, let's get the list
root@WAPN:~# opkg list-upgradable
terminfo - 6.3-1 - 6.3-2
iwinfo - 2022-08-19-0dad3e66-1 - 2022-12-15-8d158096-1
luci-app-opkg - git-22.154.41881-28e92e3 - git-22.273.29004-9f6876b
rpcd - 2022-08-24-82904bd4-1 - 2022-12-15-7de4820c-1
busybox - 1.35.0-3 - 1.35.0-5
nano - 6.4-1 - 7.2-1
libiwinfo-lua - 2022-08-19-0dad3e66-1 - 2022-12-15-8d158096-1
luci-mod-system - git-22.140.66206-02913be - git-23.013.73113-588381e
libustream-wolfssl20201210 - 2022-01-16-868fd881-1 - 2022-12-08-9217ab46-2
ucode-mod-ubus - 2022-08-29-344fa9e6-1 - 2022-12-02-46d93c9c-1
luci-theme-bootstrap - git-22.141.59265-d8ecf48 - git-22.288.45147-96ec0cd
wpad-basic-wolfssl - 2022-01-16-cff80b4f-11 - 2022-01-16-cff80b4f-15.2
procd-ujail - 2022-06-01-7a009685-1 - 2022-06-01-7a009685-2
ucode-mod-uci - 2022-08-29-344fa9e6-1 - 2022-12-02-46d93c9c-1
firewall4 - 2022-09-01-f5fcdcf2-1 - 2022-10-18-7ae5e14b-1
dnsmasq - 2.86-14 - 2.86-15
procd - 2022-06-01-7a009685-1 - 2022-06-01-7a009685-2
px5g-wolfssl - 4 - 6.2
luci-mod-status - git-22.189.48501-6731190 - git-23.038.33313-b256644
ucode-mod-fs - 2022-08-29-344fa9e6-1 - 2022-12-02-46d93c9c-1
libnftnl11 - 1.2.1-1 - 1.2.1-2
rpcd-mod-file - 2022-08-24-82904bd4-1 - 2022-12-15-7de4820c-1
odhcpd-ipv6only - 2022-03-22-860ca900-1 - 2023-01-02-4a673e1c-2
procd-seccomp - 2022-06-01-7a009685-1 - 2022-06-01-7a009685-2
libiwinfo-data - 2022-08-19-0dad3e66-1 - 2022-12-15-8d158096-1
ucode - 2022-08-29-344fa9e6-1 - 2022-12-02-46d93c9c-1
luci-base - git-22.245.77528-487e58a - git-23.069.50944-cd8bea9
libncurses6 - 6.3-1 - 6.3-2
libiwinfo20210430 - 2022-08-19-0dad3e66-1 - 2022-12-15-8d158096-1
uhttpd - 2022-08-12-e3395cd9-1 - 2022-10-31-23977554-1
libucode20220812 - 2022-08-29-344fa9e6-1 - 2022-12-02-46d93c9c-1
rpcd-mod-iwinfo - 2022-08-24-82904bd4-1 - 2022-12-15-7de4820c-1
luci-mod-network - git-22.244.54818-b13d8c7 - git-22.345.48602-4853e7b
uhttpd-mod-ubus - 2022-08-12-e3395cd9-1 - 2022-10-31-23977554-1
hostapd-common - 2022-01-16-cff80b4f-11 - 2022-01-16-cff80b4f-15.2
wireless-regdb - 2022.06.06-1 - 2022.08.12-1
root@WAPN:~#
Ok, let's upgrade the ones with ssl in the name
opkg upgrade libustream-wolfssl20201210 px5g-wolfssl wpad-basic-wolfssl --no-check-certificate
Oh, still doesn't work
root@WAPN:~# opkg update
Downloading https://downloads.openwrt.org/releases/22.03.0/targets/ath79/generic/packages/Packages.gz
*** Failed to download the package list from https://downloads.openwrt.org/releases/22.03.0/targets/ath79/generic/packages/Packages.gz
Ok, maybe it's time to wipe this router, I'm running out of ammo here ...
more search
https://forum.openwrt.org/t/opkg-update-problem-invalid-ssl-certificate-letsencrypt-global-root-cert-expiration/107895/12
https://forum.openwrt.org/t/opkg-uclient-fetch-cant-download-from-https-site-invalid-ssl-certificate-letsencrypt-global-root-cert-expiration/107891/22
A few more things to check
root@WAPN:~# wget http://www.google.com
Downloading 'http://www.google.com'
Connecting to 172.217.13.164:80
Writing to 'index.html'
Cannot open output file: File exists
root@WAPN:~# opkg list-installed | grep -E "wget|ssl|cert"
libustream-wolfssl20201210 - 2022-12-08-9217ab46-2
libwolfssl5.5.4.ee39414e - 5.5.4-stable-1
luci-ssl - git-20.244.36115-e10f954
px5g-wolfssl - 6.2
wpad-basic-wolfssl - 2022-01-16-cff80b4f-15.2
root@WAPN:~#
Something's wrong about wolfssl ?
root@WAPN:~# opkg install libopenssl openssl-util --no-check-certificate
Installing libopenssl1.1 (1.1.1t-1) to root...
Downloading https://downloads.openwrt.org/releases/22.03.0/packages/mips_24kc/base/libopenssl1.1_1.1.1t-1_mips_24kc.ipk
Installing openssl-util (1.1.1t-1) to root...
Downloading https://downloads.openwrt.org/releases/22.03.0/packages/mips_24kc/base/openssl-util_1.1.1t-1_mips_24kc.ipk
Installing libopenssl-conf (1.1.1t-1) to root...
Downloading https://downloads.openwrt.org/releases/22.03.0/packages/mips_24kc/base/libopenssl-conf_1.1.1t-1_mips_24kc.ipk
Configuring libopenssl1.1.
Configuring libopenssl-conf.
Generating engines.cnf
Configuring openssl-util.
root@WAPN:~# opkg remove libustream-wolfssl
No packages removed.
root@WAPN:~# opkg remove libustream-wolfssl20201210
No packages removed.
Collected errors:
* print_dependents_warning: Package libustream-wolfssl20201210 is depended upon by packages:
* print_dependents_warning: luci-ssl
* print_dependents_warning: These might cease to work if package libustream-wolfssl20201210 is removed.
* print_dependents_warning: Force removal of this package with --force-depends.
* print_dependents_warning: Force removal of this package and its dependents
* print_dependents_warning: with --force-removal-of-dependent-packages.
root@WAPN:~# opkg remove libustream-wolfssl20201210 --force-depends
Removing package libustream-wolfssl20201210 from root...
root@WAPN:~# opkg install libustream-openssl --no-check-certificate
Installing libustream-openssl20201210 (2022-12-08-9217ab46-2) to root...
Downloading https://downloads.openwrt.org/releases/22.03.0/packages/mips_24kc/base/libustream-openssl20201210_2022-12-08-9217ab46-2_mips_24kc.ipk
wget: SSL support not available, please install one of the libustream-.*[ssl|tls] packages as well as the ca-bundle and ca-certificates packages.
Collected errors:
* opkg_download: Failed to download https://downloads.openwrt.org/releases/22.03.0/packages/mips_24kc/base/libustream-openssl20201210_2022-12-08-9217ab46-2_mips_24kc.ipk, wget returned 1.
* opkg_install_pkg: Failed to download libustream-openssl20201210. Perhaps you need to run 'opkg update'?
* opkg_install_cmd: Cannot install package libustream-openssl.
root@WAPN:~# opkg update --no-check-certificat
Downloading https://downloads.openwrt.org/releases/22.03.0/targets/ath79/generic/packages/Packages.gz
wget: SSL support not available, please install one of the libustream-.*[ssl|tls] packages as well as the ca-bundle and ca-certificates packages.
*** Failed to download the package list from https://downloads.openwrt.org/releases/22.03.0/targets/ath79/generic/packages/Packages.gz
Uh oh ....
Well, this wasn't supposed to be a support thread, I thought this was going to be a minor annoyance for me and a road block for newbies. This was supposed to just bring attention to the fact that the ssl certificate system need to have minimal amount of self-diagnostic and self-healing capabilities because it is so essential to the proper functionning of the rest of the system.
Well now it is 04h40, I have been at this for hours and still broken.
I won't give up and wipe the firmware until I come back here and post a real solution...... Well .... probably