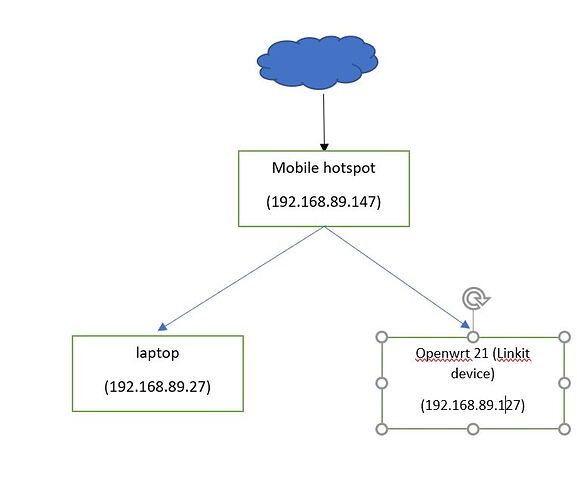
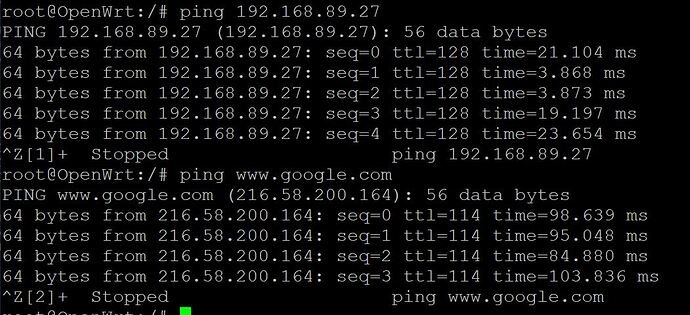
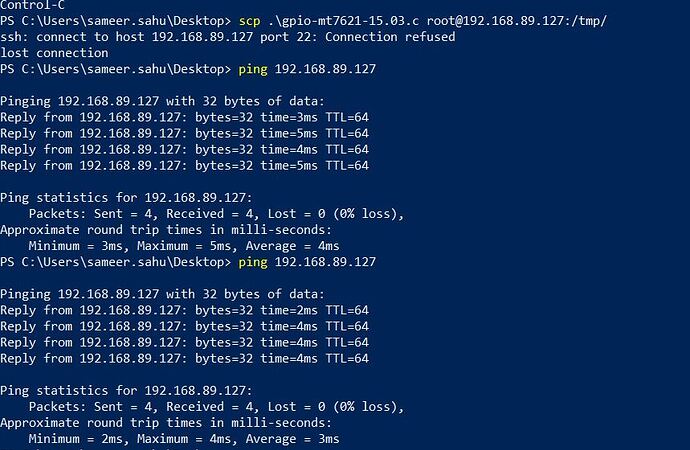
I changed Linkitsmart 7688 board firmware to Openwrt 21.02.3 version. Then I changed the wifi default setting from AP mode to STA mode. I connected my Linkit board through serial in the putty terminal and tried to ping www.google.com & it is pinging successfully and pinging to my laptop IP address. Similarly, when I tried to ping my Linkitsmart 7688 device from my laptop, it also pinged successfully. However, when I try to copy a file using SCP from my laptop to Linkit board or vice versa, it shows ssh: connect to host 192.168.89.27 port 22: Connection refused
lost connection. Can anyone suggest what I am doing wrong in the wireless setting?
I am attaching my setting below.
My dhcp file configuration:
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
My firewell file configuration:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
My wireless file configuration:
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/10300000.wmac'
option channel '1'
option band '2g'
option disabled '0'
option htmode 'HT40'
option cell_density '0'
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option network 'wwan'
option ssid 'Pixel4a'
option encryption 'psk2'
option key '9439535222'
Thanks in advance
scp -O ... ...?
If that doesn't succeed, can you log in via ssh?
I tried to do scp -o but is also not working. Do you have any other idea. Thanks for the suggestion.
Seems you're missing the 1 in your command (27, instead of 127) ?
Are you scp'ing back to the same machine ? It’s not clear if it can be pinged from this output…
Sorry, there was a type error. Actually my machine ip is 27 & Linkit ip is 127. So the machine is not pinging to itself. Machine is pinging to Linkit device. I uploaded the correct image now. Thanks for identifying the mistake. Do you have any suggestion?
Can you log in through the web UI to check if dropbear (the SSH daemon) is actually running?
Hi Borromini I am new to openwrt. Can you please tell me how yo check dropbear (SSH daemon) is running or not in openwrt?
Thanks in advance
under startup in LUCI
@fodiator I went through LUCI but didn't get understanding of its setup. Can you please guide me. I change the STA mode set up by https://openwrt.org/docs/guide-user/network/wifi/connect_client_wifi link. But once i changed to STA mode, I am unable to perform scp operation. But when I am in ap mode, the scp is working perfectly fine.
@Borromini am new to openwrt. Can you please tell me how yo check dropbear (SSH daemon) is running or not in openwrt?
I think your network being wwan is key here:
config wifi-iface 'wifinet1'
option device 'radio0'
option mode 'sta'
option network 'wwan'
That puts your interface in a different zone and different firewall rules apply - ie you are basically trying to connect from outside OpenWrt's LAN zone, so yes, SSH is blocked. It's only allowed by default inside the LAN.
The instructions you linked to talk about assigning the WWAN interface to the WAN firewall zone. That blocks SSH (and a lot of other sensitive stuff) by default. You'll need a rule to allow SSH from your specific laptop IP to access SSH. Or look into setting up WireGuard on your laptop and Linkit, I suppose your mobile hotspot has its own NAT'ing going on so people can't access the 192.168.89.x subnet from outside.
@Borromini issue is resolved. By default,openwrt do not allow ssh access from wan. I added following command in /etc/config/firewall file.
uci add firewall rule
uci set firewall.@rule[-1].src='wan'
uci set firewall.@rule[-1].dest_port='22'
uci set firewall.@rule[-1].target='ACCEPT'
uci set firewall.@rule[-1].proto='tcp'
uci commit firewall
service firewall restart
Now I am able to scp file from my laptop to openwrt device & I am also able to login through the ip address of openwrt device by putty.
Thanks for the explaining the cause of my issue.
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.